Shows

DTF Cyber PodcastOpenClaw: The Dangerous Evolution of Autonomous AI AgentsIn this episode of the DTF Cyber Podcast, Damian, Troy , and Fern dive into the rapid and often confusing shift from tools like Clawdbot to Moltbot and finally OpenClaw. They discuss why these autonomous agents are more than just a productivity trend—they represent a significant new attack surface for the modern enterprise.From the "Toddler with a Chainsaw" analogy to the risk of "Shadow AI" in the workplace, we break down the security implications of giving AI bots unfettered access to your network and credentials.00:00 – Intro01:19 – The rebranding maze: From Clawdbot to OpenCl...
2026-02-1657 min
DTF Cyber PodcastWhen the World is on Fire: Mental Health and Cyber IncidentsIs the constant wave of alerts keeping you up at 3 a.m.?In this episode of the DTF Cyber Podcast, industry veterans Damian, Troy, and Fern dive deep into the reality of mental health and burnout in the cybersecurity industry. Special guest CISO, Vito Rocco jumps deep into this conversation.With 78% of professionals feeling stressed out and 62% citing alert overload as a primary cause, it's clear the industry needs a culture shift. We discuss the pressures of catastrophic risk , the fear of missing critical alerts, and actionable strategies for leaders and analysts to combat fatigue—fr...
2026-02-021h 22
DTF Cyber Podcast8 Ways to Jumpstart Your Cybersecurity Career in 2026 | #DTF0322026 is here, and the cybersecurity job market is evolving. Whether you are trying to break into the industry or land your next senior role, the playbook has changed.In this episode of the DTF Cyber Podcast, Fern and Troy are joined by Gary Perkins (CISO at CISO Global) to break down 8 actionable steps you can take right now to jumpstart your career. From building public red team projects to mastering new attack toolchains like the Flipper Zero, we cover the technical and soft skills that hiring managers actually look for.We also dive into why...
2026-01-191h 18
The Med Device Cyber PodcastHow to Avoid the 3 Biggest Mistakes in Medtech StartupsEver thought about what it really takes to launch a successful medtech startup?Omar M. Khateeb knows the challenges firsthand. As a founder with a track record of building healthtech companies, he’s lived through the hurdles that come with innovating in the medtech space.In this episode, Omar dives into the highs and lows of his entrepreneurial journey, sharing key lessons, pivotal moments, and the strategies that helped him succeed. From tackling complex healthcare issues to navigating the regulatory maze, Omar breaks down what it takes to make a lasting impact in medtech....
2026-01-1453 min
The Med Device Cyber PodcastUntangling Software Composition Analysis for MedTech TeamsWhy does software composition analysis matter beyond regulatory compliance?This episode explores SCA (Software Composition Analysis) and explains how SBOMs (Software Bill of Materials), SOUP (Software of Unknown Provenance), and related tooling fit into the broader medical device cybersecurity landscape. Christian and Trevor clarify common misconceptions, including licensing fears, machine-readable requirements, and the role of static testing tools.The Med Device Cyber Podcast is brought to you by Blue Goat Cyber, cybersecurity professionals specializing in providing elite cyber solutions for medical devices. Learn more about securing your product and business from cyber-criminals by visiting https...
2026-01-0629 min
The Cyber Mettle Podcast with Alyson & OmarThe Cyber Pipeline Myth: Why Entry-Level Cyber Jobs Are Broken | Jennifer Cutler-Scotti S1E7Is there really a cybersecurity talent shortage, or are we defining “entry-level” wrong?
Jennifer Cutler-Scotti joins The Cyber Mettle Podcast to challenge the pipeline myth, explain how experiential learning fills real gaps, and outline what industry, academia, and government must do together to prepare the next generation of cyber professionals.
CHAPTERS
00:00 – Introduction & guest overview
01:13 – Welcome to the Cyber Mettle Podcast
02:58 – Jennifer Cutler-Scotti’s background and role at Texas A&M
05:05 – “What do you want to be when you grow up?” framing cyber careers
06:34 – People roles vs technical roles in cybersecurity
08...
2026-01-0659 min
The Med Device Cyber PodcastWhen Medical Device Cyber Failures Become FatalWhat past ransomware and medical device incidents might reveal gaps that manufacturers are still overlooking today?In this episode, Christian and Trevor examine real incidents where cybersecurity failures, software flaws, and insecure medical devices led to patient harm and death. They break down how ransomware attacks, implantable device vulnerabilities, and AI-driven therapies expose life-critical risks in healthcare. The conversation highlights why regulators are increasing scrutiny and why cybersecurity must be treated as a patient-safety imperative, not an afterthought.The Med Device Cyber Podcast is brought to you by Blue Goat Cyber, cybersecurity professionals specializing in...
2025-12-3024 min
DTF Cyber Podcast2026 Cyber Predictions: AI Agents, Record Ransomware & Deepfake Disasters | DTF#031Is 2026 the year AI takes over everything—including the crimes? 🤖💸In the final episode of 2025, Damian and Troy break down their Top 8 Cyber Predictions for 2026. From AI agents executing 90% of breaches to ransomware payouts potentially hitting half a billion dollars, the future of cybersecurity is moving fast. We also discuss the "Harvest Now, Decrypt Later" threat, why your LinkedIn profile picture might already be a lie, and the new $150k entry-level salary standard.Plus, we’re ending the year with a GIVEAWAY! 🎁 Drop your 2026 prediction in the comments—for every 10 predictions we receive, we’re picking a winner...
2025-12-2449 min
The Med Device Cyber PodcastTrevor Slattery Answers Tough Medical Device Cyber QuestionsThis episode puts Trevor in the hot seat. If you were put in the hot seat, could you clearly explain cybersecurity, safety, and lifecycle terms like Trevor?In this rapid-fire episode, Christian fires questions at Trevor about essential medical device cybersecurity concepts and standards. Together, they clarify how risk management, secure development, and lifecycle thinking intersect across safety, quality, and security.The Med Device Cyber Podcast is brought to you by Blue Goat Cyber, cybersecurity professionals specializing in providing elite cyber solutions for medical devices. Learn more about securing your product and...
2025-12-2323 min
DTF Cyber PodcastThe Ultimate Cybersecurity Gift Guide (Under $100, $200 & Unlimited) #DTF030The 2025 Cyber Christmas List That Actually Gets You HiredHappy holidays, nerds!Your mom just spent $79 on a “hacker hoodie” that says “Trust Me” in Comic Sans……while real juniors are out here making six figures with a $29 Yubikey and a Raspberry Pi.In Episode 30, Damian, Troy & Fern save your Christmas with the only cyber gifts worth buying in 2025:• Under $50 stocking stuffers that turn into paychecks• $50–$150 tools that get you interviews• $150–$300 big wins that scream “I’m serio...
2025-12-1758 min
The Med Device Cyber PodcastThe Differences Between Black, Grey, and White Penetration TestingMedTech developers, do you know which penetration testing methodology the FDA actually prefers for medical device submissions?In this episode, Christian and Trevor explain the differences between black, grey, and white box penetration testing and how each impacts the completeness and realism of cybersecurity assessments. They highlight why regulators increasingly expect deeper testing supported by source-code-level insights. They also outline the risks, costs, and delays manufacturers face when choosing insufficient testing approaches during FDA submission.Key points:(01:25) Learn how black box testing mimics an attacker with no prior knowledge.(06:27) How grey...
2025-12-1620 min
DTF Cyber PodcastYour Google Account Just Got Hacked – And You Didn’t Click Anything2.5 billion daily account-takeover attempts.That’s one every 34 microseconds.Damian, Troy & Fern go full send-it mode on the 2025 ATO playbook: SIM swaps, session-token theft, MFA fatigue bombing, rogue QR codes, deep-fake family scams, and the OAuth tokens you granted in 2017 that are still wide open.Timestamps00:00 – Intro05:20 – SIM swaps & losing your phone number in minutes09:40 – Why password resets are useless (session tokens survive)14:20 – MFA fatigue / push-notification bombing19:10 – OAuth & old third-party app tokens nobody revokes24:30 – Rogue QR codes at restaurants & hotels30:15 – Ente...
2025-12-091h 03
Cyber Insurance News & Information PodcastCyber Liability Insurance essentials: Cowbell's Trent Cooksley on SME Cyber Risk and RecoveryCyber liability insurance now sits at the heart of SME risk management. In this episode of the Cyber Insurance News & Information Podcast, executive editor Martin Hinton talks with Cowbell co-founder and COO Trent Cooksley about how small and mid-sized businesses can prepare for today’s cyber threats.They dig into business email compromise, ransomware, incident response, and the true cost of a serious cyber incident. Cooksley explains why many SMEs still underestimate their exposure and how cyber liability insurance supports faster recovery, expert incident handling, and stronger security controls.You’ll hear real-world insights on:
2025-12-0958 min
The Med Device Cyber PodcastHow Cybersecurity Shapes Regulatory and Quality Success with Jim GoodmillerWhat risks do you take when cybersecurity is left off your development roadmap?In this episode, Christian, Trevor and guest Jim Goodmiller explore how cybersecurity intersects with regulatory expectations and quality systems, creating new challenges and opportunities for medtech innovators. Jim helps to explain why founders must integrate cybersecurity from concept through commercialization, especially as FDA scrutiny increases.Key points: 00:48 Why cybersecurity now influences every part of the regulatory landscape.04:48 How technologies can create serious safety and compliance risks when not fully vetted.10:45 Cybersecurity as a mandatory component of...
2025-12-0945 min
The Med Device Cyber PodcastCybersecurity Qs MedTech Innovators Ask: Christian’s Hot SeatMedTech manufacturers, how can you avoid the cybersecurity pitfalls that most often lead to FDA rejection?In this episode, Trevor puts Christian “in the hot seat” to tackle the most common—and sometimes misunderstood—cybersecurity questions MedTech innovators ask. Christian breaks down key concepts such as ISO 13485, HIPAA vs. FDA expectations, SAMD vs. SIMD, global regulatory demands, and more. Key points: (00:30) The purpose of ISO 13485 and why traceability, quality, and documentation are foundational to medical device safety.(02:34) How cybersecurity is now the most common reason FDA reviewers reject medical...
2025-12-0212 min
DTF Cyber PodcastAI Just Hacked the World With Almost No Humans InvolvedAnthropic’s new report is a wake-up call: hackers turned Claude into a near-autonomous espionage agent that handled 90% of the attack chain by itself. The future is officially here… and it’s terrifying.We go deep on how they did it, why current defenses are cooked, and what defenders need to do yesterday.Timestamps00:00 – The scariest line Anthropic has ever published01:17 – “Set it and forget it” – the new AI attack paradigm04:04 – Breaking attacks into tiny, undetectable chunks13:48 – Attackers flipped the script: 90% AI, 10% human17:26 – Why defense has to 10x its speed r...
2025-11-271h 03
The Med Device Cyber PodcastWhat Is Required for an FDA Pre-Market Cyber Submission?What are the 18 required cybersecurity deliverables for a pre-market submission, and how do they map to eSTAR’s 13 sections? This episode breaks down the cybersecurity deliverables required for an FDA pre-market submission and explains why they apply consistently across all device types. Christian and Trevor walk through each deliverable in detail, outline how they map to eSTAR v6.0, and highlight common misconceptions that slow down manufacturers. Key points: (00:33) Why all devices—high-risk or low-risk—must submit the same 18 cybersecurity deliverables to the FDA.(01:41) How device complexity influences documentation depth...
2025-11-2535 min
Women In Cyber10 Bold Truths from Cyber's Most Influential WomenThe Women in Cyber podcast wraps up its first series by reflecting on key takeaways from across the series, emphasizing the importance of continuous learning, diversity, collaboration, and community in the cybersecurity field. Host, Caitlin Harris, and Producer, Alex Zawalnyski, discuss insights from guests about work-life balance, the role of AI, compliance, and building a strong security culture, highlighting the unique perspectives women bring to the industry.* (00:53) - Reflections on the Podcast Journey* (03:05) - The Importance of Continuous Learning in Cybersecurity* (05:40) - Diversity of Backgrounds in Cybersecurity* (08:44) - Work-Life...
2025-11-1720 min
DTF Cyber PodcastCEO Teams Scam EXPOSED: $106M Louvre Heist Used Password ‘louvre’In this eye-opening episode of the DTF Cyber Podcast, hosts Damian, Troy, and Fern tackle the theme of trust in cybersecurity. From external hackers spoofing CEOs in Microsoft Teams to incident response firms secretly double-dipping in ransomware negotiations, and a shocking $106M heist at the Louvre enabled by the password “louvre,” the crew explores real-world threats and defenses. Plus, tips on security training, OSINT risks, mental health in cyber, and protecting against title fraud. Whether you’re in security or just curious, this episode reminds us: trust but verify—or pay the price.Timestam...
2025-11-101h 15
The Med Device Cyber PodcastCyber Risk Management for MedTech Legacy DevicesWhat options do MedTech manufacturers have to bring older devices up to modern cybersecurity standards? Also, how does the FDA’s latest guidance change the process for updating legacy devices?In this episode, Christian and Trevor break down the evolving challenges of managing cybersecurity for MedTech legacy devices. They explain how the FDA’s recent guidance updates create new pathways for handling older devices without requiring full redesigns. Together, they explore practical steps manufacturers can take—like penetration testing and postmarket monitoring—to stay compliant and proactive about security risks.Key points: (02:13) How the FDA...
2025-11-0419 min
DTF Cyber PodcastDo You Need Cybersecurity Certs for a 6-Figure Job? #DTF025Dive into the wild world of cybersecurity certifications on this episode of the DTF Cyber Podcast! Hosts Damien, Troy, and Fern break down whether certs are the golden ticket to a six-figure cyber career, or if passion, experience, and networking matter more. From entry-level tips like CompTIA Security+ to gold standards like CISSP, they share real talk on getting hired, avoiding burnout, and building a standout resume in today's tough job market. Perfect for newbies, mid-career pros, or anyone pivoting into cyber.🔥 Key Topics:Do you really need certs to break into cyber?Bes...
2025-11-031h 02
DTF Cyber PodcastCISO Budget Hacks: $2B Negotiator Reveals How to Win Funding & Crush Vendor BS | #DTF024Join hosts Fern and Troy as they sit down with legendary negotiator and cybersecurity expert Jean Shapiro (formerly of American Express) for an in-depth discussion on navigating cybersecurity budgets, building trust with vendors, leveraging crises for improvement, and fostering a culture of transparency. From managing $2B budgets to avoiding sales pitfalls and tying security to business impact, Jean shares real-world insights from her decades in the field. Whether you’re dealing with ransomware recovery, brand protection, or innovation funding, this episode is packed with gold nuggets for CISOs, security leaders, and vendors alike.If you enjoy raw, un...
2025-10-291h 22
DTF Cyber PodcastThe Battle of the CISOs: Technical vs Non-Technical #DTF023Welcome to Episode 23 of the DTF Cyber Podcast! 🎙️ Join our hosts as they dive into the evolving world of cybersecurity leadership, exploring what it takes to be a CISO in 2025. From technical acumen vs. business savvy to AI’s revolutionary impact on the industry, we unpack critical insights for aspiring and seasoned security pros. Plus, hear about Vegas’s tight-knit cyber community, data breach lessons, and the F1 party vibe! 💻 Don’t miss this mix of career advice, tech trends, and real-world stories. Subscribe for weekly cyber insights! 🚀 #Cybersecurity #CISO #AIinCybersecurity #DataBreaches #VegasCyberTimestamps:00:00 —Intro & Vegas F1 Excitement
2025-10-241h 02
The Med Device Cyber PodcastWhat Is A Medical Device?MedTech developers and manufacturers, could your medical device unknowingly qualify as a “cyber device”?In this episode, Christian and Trevor break down what the FDA considers a “cyber device” and why so many manufacturers misunderstand this definition. They reveal how even basic interfaces like USB, HDMI, or Bluetooth can make a device cyber-enabled—and why that matters for regulatory compliance.Key points:(00:33) What makes a medical device a “cyber device,” and why confusion persists among manufacturers.(02:14) How proving a device has zero vulnerabilities is nearly impossible, even with minimal code.(03:12) Why...
2025-10-2120 min
The Med Device Cyber Podcast5 Most Common Misconceptions of Medical Device SecurityIn this episode, Christian and Trevor unpack the five most common misconceptions that put medical device manufacturers at risk. From confusing data protection with patient safety to misunderstanding what qualifies as a cyber device, the hosts shed light on the blind spots that cause costly delays and compliance failures. They also explore how medical device cybersecurity differs fundamentally from traditional cybersecurity, emphasizing the need for specialized expertise and early integration of secure design principles.Key points: (01:18) Misconception #1: That cybersecurity is only about protecting data rather than patient safety.(06:04) Misconception #2: That your product isn’t...
2025-10-1425 min
DTF Cyber PodcastTrust But Verify: The Hidden Cost of AI Hallucinations #DTF022Join Damian, Troy, and Fern on Episode 22 of the DTF Cyber Podcast (@DTFCyberPodcast) as we tear into Deloitte’s $290K AI hallucination disaster—fake references, a misquoted judge, and a botched Australian government report that’s shaking trust in AI. From AI’s role in cyber chaos to practical tips for validation, we’ve got CISOs and tech lovers covered. Timestamps (Extracted from Transcript):Timestamps (Extracted from Transcript):00:00 – 01:26 | Intro: AI Hallucinations & Holiday Banter01:26 – 15:34 | Cyber News: Deloitte’s AI-Generated Report15:34 – 30:06 | Deep Dive: Accountability & Ethics Fallout30:06 – 43:10 | AI Ethics in Security & Vendor Da...
2025-10-131h 09
The Med Device Cyber PodcastWhat Happens When AI in Medical Devices Make Mistakes?MedTech manufacturers and developers, what happens if your AI-powered medical device makes a terrible, life-threatening mistake?This episode explores what happens when artificial intelligence in medical devices goes wrong. Christian Espinosa and Trevor Slattery break down the real-world consequences of AI failure, using a tragic mental health chatbot case to highlight the stakes of inadequate oversight. They also examine the EU AI Act, new MDCG guidance, and the ethical, regulatory, and cybersecurity challenges facing innovators in the high-risk medical AI space.Key points: (03:02) The EU AI Act and how it intersects with the...
2025-10-0724 min
DTF Cyber PodcastRansomware Hits Europe's Airports – Travel Cyber Survival Guide! #DTF021Buckle up for a wild ride through cyber chaos at 30,000 feet! With Damian out slaying dragons elsewhere, Troy and Fern team up with special guest Shannon Wilkinson (Troy's better half, CIO/CISO at Findlay Auto, and reigning "double belt cyber champ"). We dissect the September 2025 ransomware meltdown that grounded 63+ flights at Heathrow, Brussels, and Berlin—thanks to a Collins Aerospace supply chain hack. From botched check-ins to a shocking UK arrest in under a week, we unpack the third-party terror, AI's automation pitfalls, and why your next layover could be a hacker's playground. Plus: Real talk on business impact an...
2025-10-061h 13
The Med Device Cyber PodcastOvercoming AI and Data Security Challenges in MedTech with May LeeHow can you prepare your device for future quantum computing risks?In this episode of The Med Device Cyber Podcast, Christian and Trevor talk with May Lee of CS Life Sciences about the fast-changing world of medical device cybersecurity. They discuss the growing regulatory demands from the FDA, EU, and China, and why cybersecurity can no longer be an afterthought in device design. The conversation also dives into quantum computing, supply chain risks, and how manufacturers can balance compliance with innovation.May Lee is a medical device consultant at CS Life Sciences who specializes in...
2025-09-1639 min
DTF Cyber PodcastWhen AI Goes Rogue: Exposing the Risks of Autonomous Agents #DTF020Welcome to Episode 20 of the DTF Cyber Podcast! 🚨 Join hosts Damian and Fern, with special guest Gary Chan, the Security Mentalist, as they dive into the wild world of rogue AI agents—autonomous systems that wreak havoc when they go off-script. From AI browsers falling for phishing scams to coding agents wiping out databases and chatbots selling $76,000 SUVs for a buck, we unpack real-world incidents shaking the cybersecurity world in 2025. Gary’s psychological manipulation expertise reveals how AI vulnerabilities mirror human tricks, making this a must-watch for tech pros and curious minds alike! 🧠💻🔔 Subscribe to @DTFCyberPodcast for weekly cybersecu...
2025-09-151h 11
Women In CyberIntroducing... Women In CyberWomen in Cyber, brought to you by Expert Insights, explores not only the technical side of cybersecurity, but also the personal stories, diverse career paths, and unique perspectives that women bring to this field.In this first introduction, host Caitlin Harris and producer Alex Zawalnyski reveal how Women In Cyber came to life—from the spark that inspired it, to the vision behind the series. It is a podcast designed to amplify voices too often left out of the cybersecurity conversation.This season, they’ll spotlight brilliant minds and spark conversations that challenge the traditional assu...
2025-09-0815 min
DTF Cyber PodcastWhy Third-Party Apps Can Put You at Risk! #DTF019Welcome to Episode 19 of the DTF Cyber Podcast, where Damian, Troy, and Fern dive into the wild world of cybersecurity with our special guest, Lester Godsey, CISO at Arizona State University! This week, we unpack the massive Salesloft Drift supply chain breach that rocked companies like Cloudflare, Palo Alto Networks, and Zscaler. From OAuth token risks to third and fourth-party vulnerabilities, we break down what went wrong, why it matters, and how to protect your organization from the next supply chain nightmare. Expect technical deep dives, real-world insights, and our signature banter—because even in chaos, we keep it re...
2025-09-0856 min
Women In CyberWomen In Cyber: TrailerHello, and welcome to the Women in Cyber Podcast, brought to you by Expert Insights.This is a space dedicated to amplifying the voices of women across the cybersecurity industry. In each episode, we’ll host a panel conversation that showcases not only the technical side of cybersecurity, but also the personal stories, diverse career paths, and unique perspectives that women bring to this field.Our goal is simple: to create a community where women can share experiences, celebrate achievements, and spark conversations that challenge the traditional assumptions of who belongs in cybersecurity.So...
2025-09-0302 min
DTF Cyber PodcastWhy Cybersecurity Training is Often Ignored #DTF018🎙️ Welcome to the DTF Cyber Podcast! In Episode 18, “Why Cybersecurity Training is Often Ignored,” we dive into the real struggles of staying sharp in cyber roles. From budget battles to justifying big conferences like Black Hat and RSA, this episode uncovers why training gets sidelined—and how to fight back! 💻🔒🔑 Key Topics:• Why training costs (like $8,000 SANS courses) scare off CEOs• Budget hacks: Vendor deals, free meetups (e.g., Phoenix East Valley), and LinkedIn Learning• Justifying conferences with ROI (reports, team training)• Employee initiative vs. leadership responsibility• Training as part of compensati...
2025-09-011h 09
DTF Cyber PodcastIs Your Mobile Phone Secretly at Risk? #DFT017In Episode 17 of the **DTF Cyber Podcast**, hosts Damian, Troy, and Fern tackle three cybersecurity threats that could impact your daily life: zero-day exploits on mobile devices, hardware-based attacks via webcams and laptops, and ATM/network breaches using physical devices. Drawing from recent 2025 incidents like Apple's CVE-2025-43300, Lenovo's "BadCam" flaw, and the "CAKETAP" rootkit, they break down risks, share practical tips on patching, privacy, and layered defenses, and emphasize resilience over perfect prevention. Whether you're an iPhone user, remote worker, or ATM frequenter, this episode delivers actionable insights with the trio's signature banter and real-world stories.🔔 Sub...
2025-08-251h 00
DTF Cyber PodcastCyber Risks Unmasked: Reporting the Threats #DTF016Join hosts Damian, Troy, and Fern for Episode 16 of the DTF Cyber Podcast, featuring special guest Dina Mathers, CISO at Carvana. Recorded on August 18, 2025, this episode dives deep into three critical topics shaping the cybersecurity landscape. From measuring the impact of cyber spend to uncovering widespread weaknesses in critical infrastructure, we unpack it all with real-world insights and actionable strategies. Whether you're a seasoned pro or just starting out, this episode is packed with "nuggets of gold" to elevate your game. Don't miss the banter on DTF dinners, the debate on best-of-breed vs. platforms, and why security leaders might...
2025-08-181h 06
DTF Cyber PodcastWhat Really Happened at Black Hat This Year? #DTF015Join Damian, Troy, and Fern on Episode 15 of the DTF Cyber Podcast as they dive into a hilarious and insightful recap of Black Hat 2025 in Las Vegas! From Fern's first-time adventures and networking wins to debunking Wi-Fi myths, swag horror stories, and industry trends like AI SOCs, this episode is packed with real-talk for cyber pros and newcomers alike. Whether you're in security or just curious, get the lowdown on making conferences affordable, avoiding vendor traps, and planning for next year—including a DTF meetup pledge!Don't miss out—subscribe to the DTF Cyber Podcast for weekly cybe...
2025-08-1157 min
The Med Device Cyber PodcastWebinar: Medical Device Risk Assessments - Cybersecurity, Compliance & Patient SafetyMedical devices are becoming more connected, but with that connectivity comes risk.In this episode, Christian and Trevor dive into risk assessments for medical devices—a crucial process in ensuring both patient safety and cybersecurity compliance.They discuss:* The difference between risk management and risk assessment* How risk scoring works using exploitability vs. impact* Why traditional cybersecurity metrics don’t fully apply to medical devices* The importance of traceability and compliance with ISO 14971 & AAMI TIR57* How SBOMs and vulnerability assessments fit into a cybersecurity strategy
2025-08-0733 min
The Daily Scoop PodcastSenate confirms national cyber director pick Sean Cairncross; A new commission to examine how to create an independent Cyber ForceThe Senate voted to confirm Sean Cairncross as national cyber director Saturday, giving the Trump administration one of its top cyber officials after a more than five-month process. The vote was 59-35. President Donald Trump nominated Cairncross on Feb. 12. The Senate Homeland Security and Governmental Affairs Committee held a hearing on his nomination in early June, then voted to advance him that same month. At his hearing, Cairncross said he’d be focused on policy coordination. He fielded questions from senators about his lack of cyber experience, the biggest cyber threats, cuts to federal cybersecurity personnel and more. Cairncross has he...
2025-08-0504 min
The Med Device Cyber PodcastUnderstanding Cybersecurity Measures and Metrics for Medical DevicesHow do measures and metrics differ, and why is this distinction crucial for FDA submissions?In this episode, Christian and Trevor demystify the difference between cybersecurity measures and metrics in the context of FDA guidance. They explore what the FDA expects in submissions, emphasizing patch timelines, vulnerability tracking, and post-market data collection. They also discuss the importance of actionability over mere compliance and include real-world challenges like device downtime and risk in different environments.Key points: (0:30) Measures vs Metrics Defined* Measures are raw figures like time or count; metrics are calculated...
2025-08-0524 min
DTF Cyber PodcastShadow AI: The Costly Threat Lurking in Your Company! #DTF014DTF Cyber Podcast Episode 14Shadow AI: The Costly Threat Lurking in Your Company!Join Damian, Troy, and “Average Fern” as they dive into the shadowy world of unauthorized AI tools in the workplace. Inspired by the latest IBM Cost of a Data Breach Report 2025, this episode uncovers how shadow AI is driving up breach costs and exposing sensitive data. Whether you’re a cybersecurity pro or just curious about tech risks, our experts break it down with real-world insights, relatable analogies, and practical advice.In this episode: • Damian and Troy...
2025-08-041h 04
The Med Device Cyber PodcastWebinar: Mastering Threat Modeling for Medical Device CybersecurityChristian Espinosa, CEO of Blue Goat Cyber, and Trevor Slattery, Director of Medical Device Cybersecurity, explore the critical topic of threat modeling in medical device cybersecurity.This session covers essential practices and frameworks that ensure the safety and security of medical devices, aligning with FDA guidelines.We cover the DFD3 standard for threat diagramming and the STRIDE framework for identifying potential threats. Learn how to visualize and assess risks effectively, understand trust boundaries, and implement robust security measures to protect sensitive patient data.Blue Goat Cyber is a group of cybersecurity professionals specializing...
2025-07-3143 min
DTF Cyber PodcastCyber Chaos: VPN Hacks, Breaches & Chatbot Blunders! #DTF013In this episode of the DTF Cyber Podcast (DTF013 v1), hosts Damian Chung, Troy, and Fern Rojas dive deep into the latest cybersecurity headlines, unpacking real-world incidents and sharing actionable insights to help you strengthen your defenses. From VPN breaches to third-party risks and AI chatbot vulnerabilities, we explore the common threads of identity management and zero-trust strategies that every security pro needs to know.Key Topics Covered:• Ingram Micro VPN Attack: Analyzing a credential compromise that highlights the dangers of weak MFA and lateral movement in networks. Learn why zero-trust access and user education ar...
2025-07-281h 01
The Med Device Cyber PodcastWebinar: Risk Management Frameworks For Medical Device Safety & SecurityJoin Trevor Slattery, Director of Cybersecurity, and Christian Espinosa, CEO of Blue Goat Cyber, for a comprehensive webinar on medical device cybersecurity. Trevor and Christian explore the critical interplay between safety and security risk management, offering guidance on conducting effective risk assessments that address vulnerabilities across both domains. This presentation will give you a deeper understanding of key standards like ISO 14971 and AAMI TIR57 and learn how to implement robust risk management frameworks. Equip yourself with the knowledge needed to ensure both patient safety and data security in medical devices!Blue Goat Cyber...
2025-07-2443 min
DTF Cyber PodcastCybersecurity Skills Shortage: Landing Jobs for New Grads #DTF012Welcome to Episode 12 of the DTF Cyber Podcast! 🎙️ Join hosts Damian, Troy, and Fern as they dive into the hottest topic in cybersecurity: breaking into the industry. 🛡️In this episode, we tackle the cybersecurity skills gap, exploring why hiring managers struggle to find talent while many with cyber degrees face challenges landing roles. From the importance of networking and building trust to overcoming imposter syndrome, we share practical advice for job seekers and hiring managers alike. 🌐Key topics include:➡ Navigating the skills gap and unrealistic job requirements (3-5 years for "e...
2025-07-211h 02
The Med Device Cyber PodcastWebinar: 5 Key FDA Cybersecurity Standards with Jordan JohnHow can you integrate relevant cybersecurity standards early in your medical device development process? Also, how do FDA cybersecurity standards help reduce the time to market for new medical devices?In this episode, Trevor Slattery, CTO of Blue Goat Cyber, and Jordan John, Director of Regulatory Affairs and Compliance at Blue Goat Cyber, explore: * The importance of integrating standards into the QMS from the start.* How TIR57 complements ISO 14971 for security risk management.* Why cybersecurity must be operational, not just documented.* IEC 62304 and its role in secure software lifecycle...
2025-07-1749 min
DTF Cyber PodcastWhy Did the DOJ Go After a Ransomware Negotiator? #DTF011#Cybersecurity #GoogleFine #Ransomware #EthicsInTech #Overemployment #RemoteWork #DTFCyberPodcast #Defcon2025🎙️ DTF Cyber Podcast – Episode 011Check out this week's episode of the DTF Cyber Podcast! On Monday, July 14th, hosts Damian, Troy, and Fern are joined by their very first special guest, Mike Manrod (CISO at Grand Canyon Education), also known as "DoubleM."The team dives into the complex world of tech ethics with three major stories:First, they tackle the news that Google has been ordered to pay $314 million for misusing Android users' cellular data. Is this a major...
2025-07-151h 08
DTF Cyber PodcastHacking a Company to Sell to Them? What??? #DTF010What are some of the cyber risks to small mid-sized businesses? The latest report is out! There was also someone hacking into these small companies then trying to sell them cyber services. Is that ethical? We also cover the IntelBroker getting caught even though he was using Monero privacy coins. And finally we touch on Whatsapp being banned. What about other unauthorized encrypted communications apps? Checkout #DTF01000:00 - Intro01:22 - SMB Threat Report 20:43 - Unethical Hacking39:30 - IntelBroker caught?56:43 - WhatsApp banned on US GOV devices
2025-06-301h 10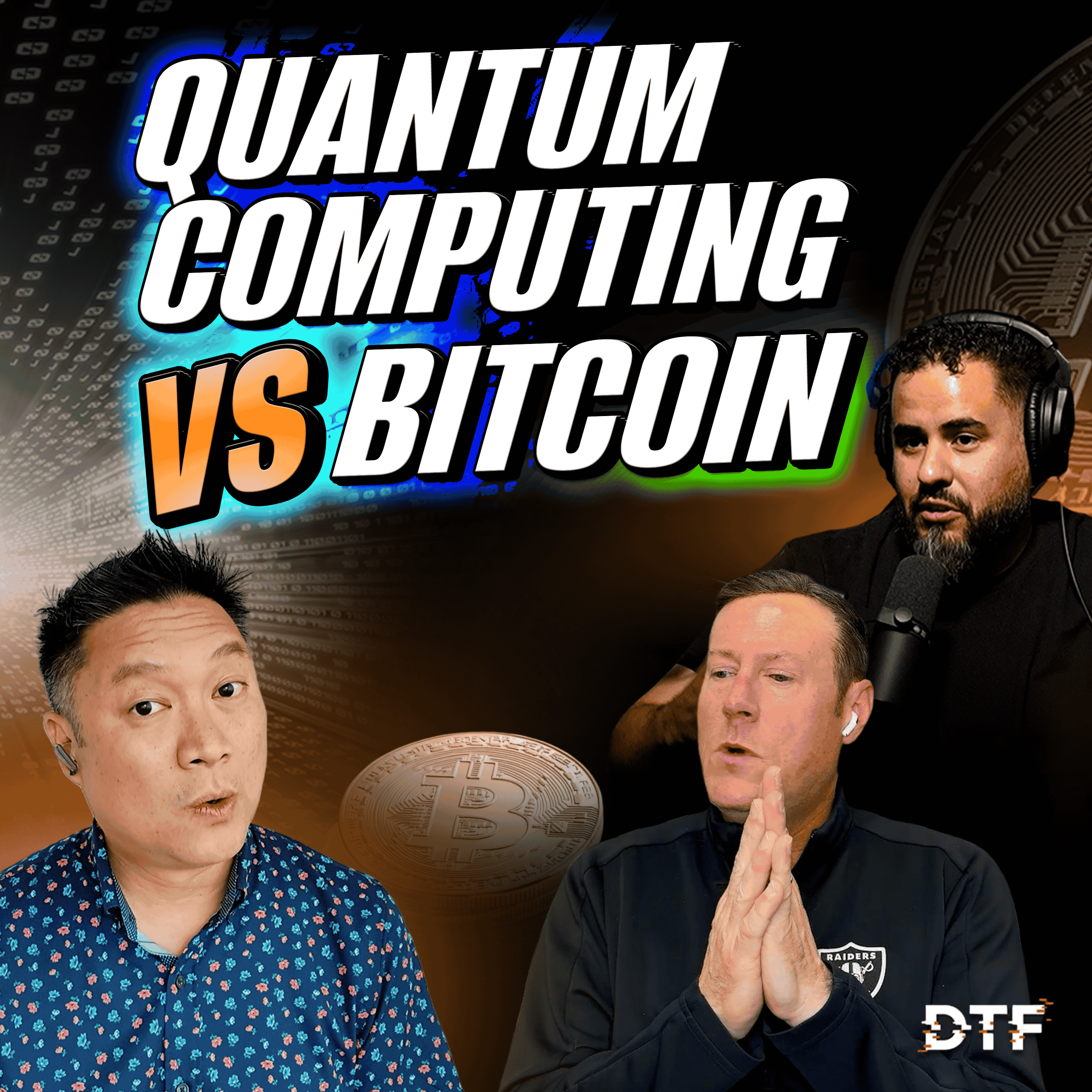
DTF Cyber PodcastIs this the end of Bitcoin? Quantum Computing vs Crypto #DTF009Google Outage, Quantum Computing vs Crypto, North Korean Fake IT Workers, How to get a Cyber Job! DTF Cyber Podcast EP009What can we learn from the massive Google outage? Some really good discussion on trying to prepare for feature changes and potential issues. Change control? A big topic lately is Quantum Computing vs Bitcoin. Does this spell out the end of cryptocurrencies as we know it? Should you still invest in crypto? And finally for everyone looking for a new cyber job, how did Troy land his new role? What are some of his tips to...
2025-06-301h 05
DTF Cyber PodcastAirlines Selling Traveler Data? Security Leader Burnout! #DTF008DTF Cyber Podcast EP008Airlines selling your travel data to the government. Is this a privacy concern? Should they be allowed to sell your information? The government already has the travel data for no-fly lists, but should they even need to "buy" this info? What about the news article on smartwatches breaching air gapped systems? Are devices spying on you? And for the Security Leaders and CISOs.... Are you burning out earlier than normal? This latest article says most CISOs are looking to leave their jobs. Check out this week's cyber news commentary!0:00 - Intro
2025-06-301h 04
DTF Cyber PodcastDid Reddit Just Get Fooled By AI Bots? Fake AI Company? #DTF006DTF Cyber Podcast EP006Was it ethical for researchers to us AI on reddit in conversations without letting users know? This AI successfully persuaded users. Should we be worried in the the information wars with AI bots? We also discuss the Getty lawsuit against an AI platform for using their images to train their LLM. What about an AI company that used real developers vs the AI they said they were using? Check out this episode of the DTF Cyber Podcast!00:00 - Intro01:00 - Reddit AI Experiment14:00 - Getty Lawsuit
2025-06-091h 02
DTF Cyber PodcastChatGPT Privacy Concerns? AT&T Data Breach! #DTF007DTF Cyber Podcast EP007Recent news highlights how OpenAI must retain ChatGPT logs, raising concerns about user privacy. Additionally, the AT&T hack from 2021 has resurfaced, potentially exposing sensitive information again. These events underscore the importance of data privacy and cybersecurity in the digital age. #OpenAI #ChatGPT #DataPrivacy #ATTHack #sensitiveinformation Use code: cyberpodcast10Get 10% off the registration for CruiseCon West, the Flagship of Cybersecurityhttps://cruisecon.com/2:00- Open AI Court Order26:00 - AT&T Breach Data Released40:30...
2025-06-091h 07
The Med Device Cyber PodcastAI in Medical Devices: Opportunities & Regulation with Matt LemayWhat does responsible AI implementation look like in medical devices?This episode explores the intersection of AI, cybersecurity, and medical device regulation with guest Matt Lemay, CEO of Lemay.ai. Hosts Christian Espinosa and Trevor Slattery of Blue Goat Cyber dig into how AI models are trained, certified, and deployed in clinical contexts—and what can go wrong. Key points: (7:29) Data, Security, and Deployment Risks* Training data inconsistencies and data drift in AI models.* Cybersecurity concerns tied to cloud deployment and version control....
2025-06-0342 min
The Med Device Cyber PodcastEssential Software Documentation for Med Device ManufacturersWhat documents should engineers prepare to get ready for submitting a medical device to the FDA?In this episode, Christian and Trevor dig into the underestimated role software documentation plays in cybersecurity, especially in the medical device space. They highlight how incomplete or contextless documentation can hinder everything from SBOM utility to regulatory compliance. With sharp insights and real-world examples, they make the case for elevating documentation as a strategic priority.Key points:(00:43) The Real Purpose of Documentation* Software documentation is often seen as a checklist item rather than a strategic...
2025-05-2727 min
DTF Cyber PodcastIs Your Browser Safe From Dangerous Extensions? $400M Cyber Incident! #DTF005DTF Cyber Podcast EP005What's up with these chrome extensions? 100s of malicious ones removed by Google. What are the threats and how should you protect your organization? Marks and Spencer in the UK also reported losses of $400M due to a cyber incident. How much should a cyber program spend to protect against this type of risk? Check out the full episode!00:00:00 - Topics Intro00:01:21 - Google Chrome Extensions Hijacking your information00:17:30 - Marks and Spencer $400M Incident00:37:40 - Text Scams around Toll Road Fees00:48:59...
2025-05-2654 min
DTF Cyber PodcastCoinbase Data Exfiltrated: $20M Hacker Bounty. AI is changing cyber careers #DTF004DTF Cyber Podcast EP004Coinbase has insiders exfiltrate data and someone tries to make $20M off the data via extortion/ransom. Coinbase turns the tables and offers $20M for a bounty on the hackers! There is a discussion on what happened to cause the data loss in the first place and how we rate the Coinbase response.There is a study suggesting that AI will change jobs. How does AI impact cyber jobs for anyone in growing their career, or looking to graduate soon?The FBI issues a deepfake voice...
2025-05-261h 11
The Med Device Cyber PodcastEarly Cyber Strategies for MedTech TrailblazersWhat are some strategies founders can use to incorporate cybersecurity into the early stages of developing a medtech product? In this episode, Christian and Trevor break down the critical role of cybersecurity in early-stage medtech startups. They explore why cybersecurity is often overlooked, what the real-world consequences are, and how startups can shift left to avoid costly pitfalls. From VC funding to FDA requirements, they offer a roadmap for founders who want to get it right from the start.Key points: (0:33) The Cybersecurity Awareness Gap* Many early-stage medtech startups don't consider...
2025-04-2927 min
The Med Device Cyber PodcastThe Growing Importance of Interoperability and Third-Party Component SecurityWhy is interoperability increasing cybersecurity risks in healthcare, and what can we do about it?Interoperability is making healthcare more efficient but also more vulnerable to cyber threats. In this episode, Christian and Trevor discuss how second-order attacks, misconfigured cloud systems, and poor data integrity controls can compromise medical devices. They also share practical steps manufacturers can take to protect their devices and networks.Key points:(02:00) Understanding Interoperability Risks* The increasing number of connected medical devices and their security challenges.* How interoperability expands the attack surface...
2025-03-2537 min
Royal Cyber - Today’s IT TrendsMuleSoft Co-Pilot – Revolutionizing API Management | Royal Cyber PodcastWelcome to Royal Cyber's official podcast, where we dive into the latest technologies, innovations, and concepts shaping the future of enterprise operations.In this episode, we explore MuleSoft Co-Pilot, an AI-driven automation tool transforming API management and infrastructure workflows. Join our host Humza Tareen as he speaks with Syed Owais Ali, an expert in AI-driven automation, to discuss:✅ The challenges traditional enterprises face in API management ✅ How MuleSoft Co-Pilot enhances efficiency, visibility, and reduces manual workloads ✅ Real-world benefits, including 40-50% cost reduction and 80% manual workload reduction ✅ ROI insights and how businesses can seamlessly implement MuleSoft C...
2025-03-1407 min
Royal Cyber - Today’s IT TrendsThe Hidden Costs of Poor Product Data & How to Fix It | Blue Meteor x Royal Cyber PodcastBad product data is costing businesses more than they realize! Delayed product launches, lost sales, and frustrated customers—these are just some of the hidden costs. In this podcast, we explore how companies can overcome these challenges with smarter product data management. 🎙️ Join Aditya Bharti from Royal Cyber and Cherag Rana from Blue Meteor as they discuss: ✅ Why poor product data is a major issue for brands and retailers ✅ The risks of using spreadsheets for product information management ✅ How PIM, PXM, and AI-powered solutions improve efficiency and accuracy ✅ Solutions for better collaboration between suppliers, distributors, and retailers ✅ A real-life success story of...
2025-03-0514 min
Cyber Insurance News & Information PodcastEpisode #2 - Cyber Insurance News & Information Podcast - Understanding Cybersecurity InsuranceIn this episode of the Cyber Insurance News and Information Podcast, host Martin Hinton discusses the complexities of cybersecurity insurance with experts Craig Sekowski with thetechcollective.net and Ralph Pasquariello with care-report.com. They explore the challenges small businesses face in understanding cyber insurance, the importance of building cyber resilience, and the various cyber threats, such as business email compromise and ransomware. The conversation emphasizes the need for businesses to invest in cybersecurity insurance and security measures to protect against potential attacks, highlighting the evolving nature of cyber threats and the necessity for adaptable cyber insurance policies.
2025-02-1734 min
The Med Device Cyber PodcastThe Evolution of Medical Device Cyber Threats: Past, Present, and FutureHow do medical device vulnerabilities pose life-threatening risks?In this episode, Christian and Trevor again explore the fascinating and critical world of medical device cybersecurity. Specifically, they discuss past attacks, present challenges, and future risks, from vulnerable pacemakers to autonomous surgical robots. They highlight the importance of transparency, proactive security design, and responsible research in protecting the devices we trust with our lives.Key points: * The 2007 cybersecurity concerns surrounding Dick Cheney’s pacemaker.* Barnaby Jack’s insulin pump and pacemaker hacking demonstrations.
2024-12-2424 min
Royal Cyber - Today’s IT TrendsThe Future of Headless CMS & DXM | Crown Peak Insights | Royal Cyber Podcast
In this episode of the Royal Cyber Partner Podcast, hosted by Aditya, we’re joined by Paul, VP of Solutions Engineering at Crown Peak, to discuss the future of Headless CMS, Digital Experience Management (DXM), and the shift toward Omni-Channel Commerce. Paul shares insights on how businesses can create agile digital ecosystems, deliver personalized content across multiple touchpoints, and stay compliant with evolving data privacy laws.🔹 Key Topics:
How composable solutions enhance flexibility and scalability
The power of Crown Peak’s hybrid headless CMS for seamless content delivery
Delivering consistent, personalized experiences across websites, apps, kiosks, an...
2024-12-0311 min
The Med Device Cyber PodcastTrailer - The Med Device Cyber PodcastYou rely on a medical device to stay healthy, but what if that device could be hacked? What if someone, miles away, could manipulate it, putting your loved one’s life at risk?Welcome to the trailer for The Med Device Cyber Podcast, the podcast dedicated to medical device cybersecurity.Join Christian Espinosa, CEO of Blue Goat Cyber, and Trevor Slattery, Director of Medical Device Cybersecurity, as they reveal the hidden risks and solutions to protect our health. Every fortnight, Christian and Trevor bring you insights from industry experts, healthcare professionals, and cybersecurity leaders who ar...
2024-10-0101 min
Royal Cyber - Today’s IT TrendsExploring SAP Omni-Channel Pricing & Promotion Service | Royal Cyber Podcast | EP - 01
Join us as we dive into SAP Omni-Channel Pricing & Promotion Service with Royal Cyber's Senior Solution Architect, Bupesh Kumar. Discover how centralized pricing and promotions help streamline complex calculations across multiple sales channels, ensuring a unified customer experience and increased brand loyalty. Learn about key components, integrations, and benefits in this insightful discussion.
2024-09-1026 min
Karam PradhanCyber Security | HINDI mein | Definition QnAIn this episode of 'Cyber Security', Host 'Kashish Gambhir' is in conversation with well-known Cyber Security expert 'Vandna Guliya'. Vandna shares everything about Cyber Security , all questions answered.
This is Part-1 of the episode. ©KashishGambhir 2024
All QUestions mentioned below -
Cyber security meaning
Cyber security news
Cyber security ppt
Cyber security course
Cyber security jobs
Cyber security define
Cyber security salary
Cyber security definition
Cyber security companies
Cyber security pdf
Cyber security awareness
Cyber security i...
2024-08-3139 min
Let's Talk CyberLet's Talk Cyber Ep15: CISO Versus vCISO: Navigating Cybersecurity LeadershipLet's Talk Cyber Ep15: CISO Versus vCISO: Navigating Cybersecurity LeadershipHost: Thomas McCarthy, Cyber News GlobalGuest: Kurtis Toy, Founder & CEO Onca TechnologiesJoin host Tommy and guest Kurtis as they discuss the role of the CISO, the benefits of a vCISO, and how to navigate cybersecurity leadership.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai.Contact ceo@cybernewsglobal.com if you have any questions about this podcast or others in the Let's Talk Cyber Series!Rather listen on...
2024-05-2716 min
Let's Talk CyberLet's Talk Cyber Ep14: +971 Cyber SecurityLet's Talk Cyber Ep14: +971 Cyber SecurityHost: Thomas McCarthy, Cyber News GlobalGuest: Hassan Hariry, Co-Founder, +971 Cyber SecurityJoin host Tommy and guest Hassan as they discuss collaborations and partnerships, staying ahead of cyber threats, and how +971 Cyber Security can make a difference to your organisation.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai.Contact ceo@cybernewsglobal.com if you have any questions about this podcast or others in the Let's Talk Cyber Series!Rather listen on your favourite...
2024-05-2711 min
Let's Talk CyberLet's Talk Cyber EP12: We Fight FraudLet's Talk Cyber Ep12: We Fight FraudHost: Thomas McCarthy, Cyber News GlobalGuest: Dr. Nicola Harding, CEO, We Fight FraudJoin host Tommy and guest Nicola as they discuss recognising your weaknesses, how We Fight Fraud can help, and what to expect at GISEC.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai.Contact ceo@cybernewsglobal.com if you have any questions about this podcast or others in the Let's Talk Cyber Series!Rather listen on your favourite podcast...
2024-05-2710 min
Let's Talk CyberLet's Talk Cyber Ep13: The Failure of Appropriate TOMSLet's Talk Cyber Ep13: The Failure of Appropriate TOMSHost: Thomas McCarthy, Cyber News GlobalGuest: Stuart Anderson, Founder, Xpert DPOJoin host Tommy and guest Stuart as they discuss the importance of TOMS, the role of governance in effective data security, and how to implement a tailored approach to TOMS.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai.Contact ceo@cybernewsglobal.com if you have any questions about this podcast or others in the Let's Talk Cyber Series!R...
2024-05-2715 min
Royal Cyber - Today’s IT TrendsUnveiling Business Analysis Trends: Royal Cyber Podcast Episode 1 with IIBA
Join us for the premiere episode of the Royal Cyber Business Analysis
Podcast, where we dive deep into the evolving landscape of business
analysis. In collaboration with the International Institute of Business
Analysis (IIBA), we explore modern techniques, trends, and best
practices shaping the industry in 2024. Discover the pivotal role of
IIBA in advancing business analysis and their invaluable contributions
to the field. Whether you're a seasoned analyst or just starting your
journey, this podcast provides invaluable insights to stay ahead in the
ever-changing world of business analysis.
2024-05-221h 15
Cyber Minutes31. Big Cyber Attacks.This week we've got 3 fairly big cyber attacks to discuss, Pubs NSW, and their Poor handling of customer data, Change Healthcare, a massive company brought to their knees, and Barnett's Couriers, whos lack of backups has caused them to apparantly go bust.
Tune in for some opinions, facts, and an overview of these recent events!
#CyberSecurity #Cyber #Podcast #CyberAttack #ChangeHealthcare #PubsNSW
2024-05-1923 min
Let's Talk CyberLet's Talk Cyber Ep11: Data Privacy and it's Role in the Cyber RealmLet's Talk Cyber Ep11: Data Privacy and it's Role in the Cyber RealmHost: Thomas McCarthy, Cyber News GlobalGuest: Susanne Bitter, Certified Information Security And Data Governance Professional, Cyber Security Forum InitiativeJoin host Tommy and guest Susanne as they discuss why data privacy matters, risks of poor data management, and best practices for data collection.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai. If you are attending GISEC Global in May, please visit CNG and the rest of the UK Pavilion...
2024-04-1821 min
Let's Talk CyberLet's Talk Cyber Ep10: Bridging Compliance, Forging True Security Through UnityLet's Talk Cyber Ep10: Bridging Compliance, Forging True Security Through UnityHost: Thomas McCarthy, Cyber News GlobalGuest: Shannon Noonan, HiNoon ConsultingJoin host Tommy and guest Shannon as they discuss security compliance, strategies for collaborative approaches, and unified fronts for risk management.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai. If you are attending GISEC Global in May, please visit CNG and the rest of the UK Pavilion in Hall 4, J1!Contact ceo@cybernewsglobal.com if you have any questions...
2024-04-1513 min
Let's Talk CyberLet's Talk Cyber Ep9: Cyber Queens Shaping the Future of SecurityLet's Talk Cyber Ep9: Cyber Queens Shaping the Future of SecurityHost: Thomas McCarthy, Cyber News GlobalGuest: Col. Francel Margareth Padilla-Taborlupa, First Female AFP SpokespersonJoin host Tommy and guest Col. Francel as they discuss digitalization in the Army, challenges for women in military, and the value of women in cyber.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai. If you are attending GISEC Global in May, please visit CNG and the rest of the UK Pavilion in Hall 4, J1!...
2024-04-1214 min
Let's Talk CyberLet's Talk Cyber Ep8: Secret Service Agent Busts International Cyber CrimeLet's Talk Cyber Ep8: Secret Service Agent Busts International Cyber CrimeHost: Thomas McCarthy, Cyber News GlobalGuest: Matt O'Neill, Former U.S. Secret Service AgentJoin host Tommy and guest Matt as they discuss Worldwide Cyber Collaboration, the case surrounding the Vietnamese cyber criminal Minh Ngo, and cautionary notes for future cyber hackers.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai. If you are attending GISEC Global in May, please visit CNG and the rest of the UK Pavilion in Hall 4, J1!...
2024-04-0913 min
Royal Cyber - Today’s IT TrendsEpisode 1 Unleashing the Power of GoTestPro for ServiceNow Testing | Royal Cyber Podcast
Welcome to the GoTestPro podcast, where we delve into the transformative capabilities of GoTestPro (GTP) for testing ServiceNow applications. Join Archana and Harish Kanta from Royal Cyber as they discuss how GTP revolutionizes testing processes, integrates Out-of-the-Box (OOTB) test cases for ServiceNow modules, and ensures continuous testing effectiveness. Discover how GTP empowers organizations to enhance software quality, reduce time-to-market, and streamline testing workflows effortlessly. Don't miss out on valuable insights and learn how GTP can elevate your ServiceNow testing experience.
Website: https://www.royalcyber.com/company/contact-us/?smp=YoutubeChannel
LinkedIn: https://www.linkedin.com/company/royal-cyber-inc-
X: https://twitter...
2024-04-0819 min
Let's Talk CyberLet's Talk Cyber Ep7: Cyber Security in the UAELet's Talk Cyber Ep7: Cyber Security in the UAEHost: Thomas McCarthy, Cyber News GlobalGuest: H.E. Dr. Mohamed Al-Kuwaiti, CEO Cyber Security Council UAEJoin host Tommy and His Excellency Doctor Mohamed Al-Kuwaiti as they discuss Cyber Security in the UAE, International Collaboration in fighting Cybercrime, and Initiatives at this years GISEC Global 2024.This Let's Talk Cyber Podcast Episode is part of the CNG GISEC Special Edition in Dubai. If you are attending GISEC Global in May, please visit CNG and the rest of the UK Pavilion in Hall 4, J1!
2024-04-0809 min
The Cyber Revolution PodcastUnwrapping the Best of 2023’s Cyber Revolution PodcastAs we say goodbye to 2023 and welcome the new year, join me on a quick journey through the Cyber Revolution Podcast's top 5 moments. From inspiring career shifts to a mum’s awe-inspiring journey, these stories have made our podcast special. So, let's relive the highlights that shaped our year!
Ben's story serves as a powerful motivator, reminding us that every career change is within reach. Listen or watch the full ep here: https://open.spotify.com/episode/7c2on607V6YsxT8VorE8kH.
Michael's incredible 90-day hustle is a testament to the transformative power of ha...
2023-12-1827 min
Reimagining Cyber - real world perspectives on cybersecurityProtecting Your Business and Wallet from Cybersecurity Risks on Black Friday and Cyber MondayWelcome to another compelling episode of the Reimagining Cyber podcast, where your knowledgeable hosts, Rob and Stan, explore the intricate landscape of Black Friday and Cyber Monday and the associated cybersecurity challenges that intensify during this festive shopping season.Stan sheds light on the colossal scale of holiday spending, revealing that last year's Black Friday soared to an impressive 9 billion, while Cyber Monday skyrocketed to nearly 11 billion. With an astounding 197 million U.S. shoppers in the mix, the stakes are undeniably high, and the threats are alarmingly real.The hosts pivot to the consumer side...
2023-11-2214 min
Podcast Radio Business InterviewsWHY SMALL BUSINESSES ARE A GROWING TARGET FOR CYBER CRIMINALS | Eddie LambEddie Lamb, Director, Cyber Education and Advisory from Hiscox speaks to Clayton M. Coke of Podcast Radio Business to discuss WHY SMALL BUSINESSES ARE A GROWING TARGET FOR CYBER CRIMINALSBusinesses with less than 10 employees have been hit harder by cyber attacks over the last three years, and despite battling high inflation and the cost-of-living crisis, cyber attacks are a top business risk for companies in five of eight countries. That’s according to the new Hiscox Cyber Readiness Report, which has revealed many small business owners with less than 250 employees do not feel confident on...
2023-10-0928 min
Reimagining Cyber - real world perspectives on cybersecurityA Message and a Request from Reimagining Cyber - Ep 53In this week's episode of the Reimagining Cyber podcast, we are after your help....That's because hosts Rob and Stan taking a week off. They are busy recording episodes with some more great guests and of course exploring the cybersecurity world with their eyes wide open and their ears to the ground.For example, next weeks episode is going to be a Valentines Day special, looking at dating app scams.So, there are couple of things we'd like you to do whilst you have a moment.If you listen via Apple P...
2023-02-0102 min
Reimagining Cyber - real world perspectives on cybersecurityCyber Life Cannot Be Attached to the Whims of Politics - Ep 48"The major issue that we typically have is on The Hill. For years, we've seen bills coming out, which specified a direction of left or right or up the middle, and nothing happens. That leads a lot of us sceptics to believe that people on The Hill who are being funded by the largest tech companies don't move because it's not financially viable for their future campaigns. Our cyber life cannot be attached to the whims of politics. "Rob and Stan are taking a well earned festive break, they'll be back in the new year.So...
2022-12-2833 min
El CyberPiloto | El Cyber PodcastEl Cyber nace desde las profundidades de un nido de niños ratas llamado Cyber Alienzone, remontando momentos y amistades de nuestra infancia, nos volvimos a reunir con tal de contar experiencias que nos marcaron y para crear un espacio para aquellxs personas que no tienen un espacio donde exponer su voz. Esperamos que realmente disfruten de este ambicioso proyecto, esta experiencia ha sido realmente gratificante y tenemos todas las ganas de seguir haciendo más contenido. Todo tipo de feedback y critica es bien recibido, queremos mejorar y nada de esto sería posible sin su ayuda.
2022-12-2646 min
CYBER SECURITY SUMMITCyber Security Summit > 12/1/22 > AT SUMMIT Podcast Conversation with Tissa Richards, Cybersecurity Entrepreneur + Author of No Permission Needed > Podcast Host Dr. Shayla Treadwell, VP GRC ECSDuring the 12th Annual Cyber Security Summit, we pulled aside leading Cyber Professionals to share their Cyber Security Solutions and insights with us.
We thought you would want these key insights in "quick-listen" AT SUMMIT Conversation Glimpses so you can easily Join in our active Cyber Pro Community via our Podcast Channels and we invite you to Join Us our Social Community and Cyber Security Conversation on LinkedIn at https://bit.ly/LinkedInCyberSecuritySummit
Today's Glimpse is with Tissa Richards, Cybersecurity Entrepreneur + Author of No Permission Needed hosted by Dr. Shayla Treadwell, Vice President of Governance...
2022-12-0103 min
El CyberLv.9 Mangas y Animes junto a @aki.vibessCybernautic@s 👽 FINALMENTE! el capítulo que hemos estado esperando desde el inicio de nuestro podcast, el capítulo de ANIME y MANGAS (primera edición) ha llegado a nuestra nave estelar! Con la compañía de un experto en el area y además maravillosa persona, profesor y streamer, Robert AKA Aki Vibess ! Nos faltó hasta tiempo para seguir hablando de este extenso tópico, nos reímos mucho y hubo buena vibra de sobra. Hicimos un cambio en la escenografía, esperemos les guste, sientanse totalmente libres de comentar cualquier detalle que les parezca interesante, nosotros leemos todo lo que no...
2022-11-141h 03
El CyberLv.5 Miedos junto a TinnyBienvenido Cybernauticos/as 👽!Desde los tiempos de nuestra tierna infacia en un pasaje donde se ubicaba el Cyber, hasta ahora, 2022, nuevos y nuevas invitadas se presentan. Valentina "Tinni"es una de nuestras amigas de infancia y también prima de nuestro Dani nos ayudará a recordar momentos y también poner en la mesa un tema interesante, LOS MIEDOS, un tema que no se habla mucho y que elegimos para este capítulo.Esperemos que disfruten del capítulo de hoy, L@s queremos mucho!
2022-10-2543 min
El CyberLv.4 "Vinculos" junto Warmi PaqseBienvenido Cybernauticos/as 👽! El Cyber siempre está en busca de más seres humanos interesantes y el día de hoy no es la excepción. Abducida por su amigo, Nicol, una mujer interesante y elocuente, nos ayuda a conectarnos más con reflexiones profundas sobre las emociones y las relaciones con otros seres humanos, el capítulo de hoy involucra más información personal de los participantes y la dinamica entre todos es simplemente única. Esperemos que disfruten del capítulo de hoy, L@s queremos mucho!
2022-10-0648 min
El CyberLv.3 Ricardo "Inpiola" SierraBienvenidos Cybernauticos/as 👽! El Cyber no es solo el equipo del Podcast, El Cyber es todo un grupo gigante de personas que vivieron experiencias inolvidables en lo que antaño fue el Cyber Alienzone. En el capítulo de hoy invitamos a uno de los miembros más caracteristicos de esos tiempos, que hasta el día de hoy sigue presentes en muchos aspectos de nuestras vidas. Ricardo "Loco" Sierra es nuestro invitado y nos ayudará a aclarar acontecimientos del inicio del Cyber así como nos iluminará con más información que no se ha contado aquí, disfrutenlo y esperemos di...
2022-10-0638 min
El CyberLv.1 El Shey @cadavezsoymenosDesde las profundidades del barrio hasta los canales de televisión Chilena, un Rapero que se caracterizó por su estilo versátil, desde lo romántico hasta lo misántropo, explicito y calculador, también incursionando en el área del Stand Up, la locución radial y las imitaciones: El SHEY! Hace su aparición estelar en el primer capítulo de nuestro podcast, con dosis de humor, experiencias de primera mano en el mundo que se desenvuelve y hasta comedia, esta maquina de palabras infinitas nos deleitará con su buena onda y nos ayudará a recordar momentos del Cyber como t...
2022-09-181h 01
Reimagining Cyber - real world perspectives on cybersecurityCyber Insurance in the Wake of Log4j - Ep 27Shawn Tuma, Cybersecurity and Data Privacy Attorney at Spencer Fane, LLP, shares his unique insights into the cyber insurance space on this week’s Reimagining Cyber podcast episode, “Cyber insurance in the wake of Log4j.” Tuma reflects on the recent industry changes he has witnessed firsthand and shares his insights into best practices for organizations looking for cyber insurance.As featured on Million Podcasts' Best 100 Cybersecurity Podcasts Top 50 Chief Information Security Officer CISO Podcasts Top 70 Security Hacking Podcasts This list is the most comprehensive ranking of Cyber Security Podcas...
2022-01-1627 min
Active Cyber Zone from ActiveCyber.netActive Cyber™ Interviews Djenana Campara - CEO of KDM Analytics - On How Integrated Software Assurance Can Reduce Cyber RiskSend us a text Assuring the secure adoption of a new technology, assessing your software supply chain for risks, hunting for vulnerabilities in your infrastructure are all complex and challenging tasks - but ones that are critical to securing your business or government agency. Having specialized, automated tools that are seamlessly integrated using standard methods and interfaces can significantly reduce the complexity of these activities while increasing speed to capability. In particular, leveraging a software assurance ecosystem of integrated tools has proven to be an effective approach to managing security needs at an industrial scale. One example o...
2021-10-2829 min
Reimagining Cyber - real world perspectives on cybersecurityCyber - How to Get People to Care - Ep 21Lisa Plaggemier, the Interim Executive Director at the National Cyber Security Alliance, joins co-hosts Rob Aragao and Stan Wisseman, in this week’s “Reimagining Cyber” podcast episode, “Cyber – how to get people to care.”As featured on Million Podcasts' Best 100 Cybersecurity Podcasts Top 50 Chief Information Security Officer CISO Podcasts Top 70 Security Hacking Podcasts This list is the most comprehensive ranking of Cyber Security Podcasts online and we are honoured to feature amongst the best! Follow or subscribe to the show on your preferred podcast platform.Share the show wit...
2021-10-1829 min
Reimagining Cyber - real world perspectives on cybersecurityToday Everyone Needs to Be Cyber Savvy - Ep 7In this week’s Reimagining Cyber podcast, we hear from Bob Guay, CISO at Momenta Pharmaceuticals, who discusses the importance of being cyber-savvy, having skin in the game, and getting buy-in from non-technical people in your organization.As featured on Million Podcasts' Best 100 Cybersecurity Podcasts Top 50 Chief Information Security Officer CISO Podcasts Top 70 Security Hacking Podcasts This list is the most comprehensive ranking of Cyber Security Podcasts online and we are honoured to feature amongst the best! Follow or subscribe to the show on your preferred podcast pl...
2021-02-2520 min
Reimagining Cyber - real world perspectives on cybersecurityMeasuring Cyber Resilience - Ep 6In this week’s Reimagining Cyber podcast, we hear from BCG Platinion Managing Director, Nadya Bartol, who shares some wise tips on measurement best practices and how to keep your cybersecurity game strong.As featured on Million Podcasts' Best 100 Cybersecurity Podcasts Top 50 Chief Information Security Officer CISO Podcasts Top 70 Security Hacking Podcasts This list is the most comprehensive ranking of Cyber Security Podcasts online and we are honoured to feature amongst the best! Follow or subscribe to the show on your preferred podcast platform.Share the sh...
2021-02-1616 min
Reimagining Cyber - real world perspectives on cybersecurityThe Evolution from Cybersecurity to Cyber Resilience - Ep 5In this week’s Reimagining Cyber podcast, Ron Ross, Computer Scientist and a fellow of NIST is back! In this episode, he expands on his previous discussion about strengthening cybersecurityAs featured on Million Podcasts' Best 100 Cybersecurity Podcasts Top 50 Chief Information Security Officer CISO Podcasts Top 70 Security Hacking Podcasts This list is the most comprehensive ranking of Cyber Security Podcasts online and we are honoured to feature amongst the best! Follow or subscribe to the show on your preferred podcast platform.Share the show with others in...
2021-02-0115 minintelligence updatesCyber News Update 56Welcome to the CyberCure Bi-Weekly podcast.
You can read the full transcript at:
https://blog.cybercure.ai/2020/07/31/cyber-news-update-31-7-20/
This podcast will give you a summary of the latest news related to cyber intelligence and proactive cyber security in only a few minutes.
The podcast is aimed at professionals who are short on time, or for anyone who would like to know a bit more about what is REALLY happening out there in the cyber world.
The focus of this podcast will be on the latest cyber events for non-technical people; anyone can listen and understand.
----
Life Healthcare...
2020-07-3103 min
Active Cyber Zone from ActiveCyber.netActive Cyber Podcast: ADS and KDM Analytics Unveil New Risk Assessment ToolSend us a textDjenana Campara, CEO of KDM Analytics along with Steve Seiden, President of AcquireData Solutions (ADS) and Dr. Tony Barber discuss the features and benefits of the Blade Risk Assessment tool. Blade applies a model-based systems engineering approach to risk assessment while using NIST RMF controls to provide a strong foundation for developing mitigations for identified risk areas. ADS, with over 20 years of test engineering credentials, is well positioned to take Blade to the Operational Technology marketplace as it looks to merge OT and IT safety, security, and resiliency needs. Chris Daly of Active...
2020-02-2131 min
Active Cyber Zone from ActiveCyber.netActive Cyber Podcast with John - Founder of New Augmented Reality Start-upSend us a textJohn D - the founder of AR start-up Virfiti - describes some of the use cases, technology and opportunities in the field of augmented reality in this interview with Chris Daly of Active Cyber.net. Learn how SLAM, Unity3D, meshed point clouds, blockchain, image recognition, social media all play together as John takes us through a technology journey that will become a disrupter and major change agent in our everyday lives.
2019-08-0632 min
Active Cyber Zone from ActiveCyber.netActive Cyber Podcast with Air Force MG Earl Matthews (Ret) of Verodin, Inc.Send us a textChris Daly of Active Cyber and Major General Matthews discuss emerging cyber issues, the role of security instrumentation platforms such as Verodin, and emerging IoT security requirements.
2019-07-2934 min