Shows

InfoSec BitesNIST PQC: The Race for Post-Quantum StandardsThe discussion in this podcast provides an extensive overview of the National Institute of Standards and Technology (NIST) Post-Quantum Cryptography (PQC) standardisation process, which was initiated to combat the existential threat posed by future quantum computers to current public-key algorithms like RSA and ECC. NIST’s multi-year effort, which began in 2016, culminated in the selection of a diverse portfolio of quantum-resistant algorithms—including the lattice-based ML-KEM and ML-DSA, the hash-based SLH-DSA, and the code-based HQC—to ensure cryptographic resilience. A primary driver for this urgent transition is the "harvest now, decrypt later" threat model, where adversaries steal encrypted data today...
2025-10-1635 min
InfoSec BitesActive Directory, EntraID, Azure AD: MS Identity Services Architecture, Security & IncidentsThe podcat discussion provides a comprehensive security audit of Microsoft's identity services, comparing the architecture, protocols, and vulnerabilities of three distinct platforms: Active Directory Domain Services (AD DS), the legacy on-premises solution; Active Directory Federation Services (ADFS), the traditional federation server; and Entra ID (formerly Azure AD), the cloud-native identity platform. The text details the logical and physical structures of AD DS, focusing on Kerberos and NTLM vulnerabilities like the Golden Ticket attack, before examining ADFS's role in hybrid environments and its security burden. The analysis concludes by highlighting the Zero Trust capabilities of Entra ID, such as Conditional...
2025-10-1547 min
InfoSec BitesOpenSSL: Architecture, Agility, and Quantum ResilienceThe discussion in this podcast provides an extensive audit of the OpenSSL 3.x toolkit, focusing on its architecture, strategic agility, and quantum resilience. It highlights that the shift to the modular Provider concept in OpenSSL 3.x is a critical evolution enabling cryptographic agility, particularly for the transition to Post-Quantum Cryptography (PQC) using hybrid key exchange schemes in TLS 1.3. The analysis identifies that historical failures, such as Heartbleed, stem primarily from low-level C memory safety issues and flaws in protocol state machine handling. Finally, it contrasts OpenSSL’s commitment to API stability and feature richness against security-focused forks like LibreSSL an...
2025-10-1431 min
InfoSec BitesAWS Security: An Exhaustive Analysis of its Defense in Depth ArchitectureThe podcast discusses an extensive analysis of the Amazon Web Services (AWS) security architecture, focusing on its implementation of the Defense in Depth (DiD) strategy through a multi-layered framework. It establishes the Shared Responsibility Model as the foundational security principle, clearly separating AWS's responsibility for the "Security of the Cloud" from the customer's accountability for the "Security in the Cloud." The analysis systematically breaks down the architecture into five layers—including Identity and Access Management and Monitoring, Detection, and Automation—and details how various AWS services contribute to a robust security posture. While affirming that AWS offers a highly secu...
2025-10-131h 06
InfoSec BitesHTTP/2 Deep Dive: Architecture, Security, Vulnerabilities & Quantum ThreatThe discussion in this podcast provides an extensive analysis of the HTTP/2 protocol, detailing its architectural shift from the text-based HTTP/1.1 to a more efficient binary and stateful framework using features like multiplexing and HPACK header compression. It thoroughly explains how these performance-enhancing changes, which solve application-layer Head-of-Line (HOL) blocking, simultaneously introduce new security vulnerabilities centred on computational amplification and resource exhaustion. It examines several critical denial-of-service (DoS) vectors, including the Rapid Reset attack (CVE-2023-44487) and the HPACK Decompression Bomb, noting that these attacks exploit the protocol's state management complexities. Finally, the analysis discusses necessary layered mitigation strategies—st...
2025-10-1239 min
InfoSec BitesISO 27001: Strategic Information Security FrameworkThe discussion in this podcast provides an extensive overview of the ISO/IEC 27001:2022 standard, which serves as the international framework for an Information Security Management System (ISMS). It explains that the standard is a strategic, risk-driven approach built upon the core principles of Confidentiality, Integrity, and Availability (CIA), rather than a mere technical checklist. It details the operational mechanism of the ISMS, which is mandatorily structured around the Plan-Do-Check-Act (PDCA) cycle for continuous improvement. Crucially, the source outlines the mandatory clauses (4-10) of the standard and analyses the Annex A control catalog, including its reorganization in the 2022 revision into...
2025-10-1139 min
InfoSec BitesAWS ELB, Route 53, and CloudFront Deep DiveThis podcast provides a comprehensive architectural and security analysis of three core AWS global delivery services: Elastic Load Balancing (ELB), Amazon Route 53 (DNS), and Amazon CloudFront (CDN). It explains the foundational mechanics of each service, detailing how ELB leverages the Hyperplane for scaling, how Route 53 uses an Anycast data plane for global resilience, and how CloudFront relies on a multi-tiered Edge and Regional Cache hierarchy for performance. A significant portion of the discussion focuses on the AWS Shared Responsibility Model, explicitly outlining customer configuration mandates for security, such as compulsory use of Origin Access Control (OAC), enforcement of strong...
2025-10-1044 min
InfoSec BitesSolarWind's Supply Chain Espionage: How Sunburst Attack Shattered Digital TrustThe discussion in this podcast provides an extensive analysis of the SolarWinds cyber incident, detailing how the sophisticated, state-sponsored attack leveraged the software supply chain to compromise thousands of customers, including critical U.S. government agencies. The operation, formally attributed to Russia's Foreign Intelligence Service (SVR), involved a meticulous infiltration of SolarWinds’ build environment to inject the SUNBURST backdoor into legitimate software updates. This overview explains the technical tradecraft of the malware, the systemic governance failures at SolarWinds, and the industry-wide shift toward zero-trust models and enhanced supply chain security. Furthermore, it addresses the legal ramifications, noting the landmark SE...
2025-10-0927 min
InfoSec BitesPillars of Cyber Risk : Vectors, Surface, Appetite, ToleranceThe podcast provides a comprehensive discussion on the Governance, Risk, and Compliance (GRC) Nexus, specifically exploring four foundational cybersecurity concepts. It first defines the threat landscape from an attacker’s perspective, distinguishing between an Attack Vector, which is the specific method of exploitation (e.g., phishing), and the Attack Surface, which is the totality of an organization's exposure (e.g., all systems and employees). The second half of the discussion addresses the strategic response from the defender's perspective, explaining that Risk Appetite is the high-level willingness to accept risk to achieve goals, while Risk Tolerance consists of the measurable, op...
2025-10-0649 min
InfoSec BitesCISSP Domain-8: Software Development SecurityThe dicussion in this podcast offers a comprehensive overview of Software Development Security, covering the Software Development Life Cycle (SDLC) and various Development Methodologies. The text systematically explains the phases of the SDLC—including requirements gathering, design, development, testing, and operations and maintenance—while stressing the importance of integrating security at every stage. Furthermore, the discussion contrasts traditional methods like Waterfall with iterative approaches such as Agile, Spiral, and Rapid Application Development (RAD), and introduces modern team structures like DevOps and DevSecOps. Finally, it details the technical aspects of software development, including programming language generations, Object-Oriented Programming (OOP) concepts, appl...
2025-10-0555 min
InfoSec BitesCapital One Cloud Breach: Misconfigured WAF and Least Privilege Principle ViolationThe podcast discusses post-mortem analysis of the 2019 Capital One cloud breach, detailing the technical, human, and systemic failures that allowed for the compromise of approximately 106 million individuals' data. It explains that the attack was successful due to a misconfigured Web Application Firewall (WAF) and the violation of the Principle of Least Privilege, which allowed an attacker to steal highly privileged AWS credentials. Furthermore, the analysis emphasizes that the breach was a result of systemic governance failures and inadequate internal detection capabilities, ultimately resulting in an $80 million regulatory fine and a $190 million class-action settlement. The discussion concludes that the incident...
2025-10-0426 min
InfoSec BitesJFrog Artifactory: DevSecOps, Binary Repository Management and Image SecurityThe discussion in this podcast provides a comprehensive security overview of JFrog Artifactory, a critical and foundational component acting as a universal binary repository manager within the software supply chain. It explains Artifactory's core architecture, including its server, database, and various repository types (local, remote, virtual), and emphasizes its indispensable role in DevOps and CI/CD pipelines. It highlights that the platform faces significant threats stemming from misconfigurations like anonymous access and public exposure, as well as the critical risk of leaked, broadly privileged tokens that can enable catastrophic supply chain attacks. Finally, it details a strategic set of...
2025-10-0237 min
InfoSec BitesCISSP Domain-7: Security OperationsThe podcast discussions details critical aspects of maintaining an organisation's security posture and operational resilience. The discussion covers security operational controls such as auditing and logging, enforcing least privilege and separation of duties, and implementing change management and configuration management practices to maintain system integrity. A significant portion addresses physical security measures, including defensive perimeters, access controls like locks and surveillance (CCTV), and the use of intrusion detection systems (IDSs). Finally, the sources extensively describe incident response (IR), digital forensics, disaster recovery (DR), and business continuity planning (BCP), focusing on strategies like defining recovery objectives (RPO/RTO), managing backup...
2025-10-0151 min
InfoSec BitesCISSP Domain-6: Security Assessment and TestingThis discussion in the podcast provides an extensive overview of security assessments, testing, and audits, detailing the processes necessary to evaluate an organization's security posture. It explains the differences between vulnerability testing, penetration testing, and formal audits, including various testing methodologies like black box, white box, and gray box approaches. Furthermore, it discusses the importance of security metrics and indicators (such as KPIs and KRIs) for measuring the effectiveness of an Information Security Management System (ISMS) and communicating strategic insights to management. Finally, we cover critical administrative security processes, including account management, backup verification, security awareness training, and disaster...
2025-09-3048 min
InfoSec BitesAustralian Privacy Principles: Deep Dive for InfoSec ProfessionalsThe podcast dicussion provides an extensive analysis of the Australian Privacy Principles (APPs), which constitute the core legal framework for data protection under Australia's Privacy Act 1988. It functions as a strategic guide for Information Security (InfoSec) professionals, breaking down the thirteen legally binding principles that govern how most government agencies and private organisations ("APP entities") must manage personal information throughout its lifecycle. Key concepts examined include the objective standard of "reasonable steps", the stringent rules for collecting sensitive information and unsolicited data, and the crucial distinction between internal "use" and external "disclosure" of personal data. Furthermore, it meticulously details...
2025-09-2956 min
InfoSec BitesCISSP Domain-5: Identity and Access Management (IAM)The dicussion in this podcast provides an extensive overview of Identity and Access Management (IAM) concepts, focusing on the critical phases of identification, authentication, and authorization within secure systems. They detail various authentication methods, including passwords, multi-factor authentication (MFA), and biometrics, explaining the mechanics and weaknesses of each. A significant portion covers different access control models such as Discretionary (DAC), Mandatory (MAC), and Role-Based (RBAC), alongside the use of XML-based markup languages like SAML and XACML for secure data exchange in web services. Furthermore, it examines centralized remote access technologies like RADIUS, TACACS+, and Diameter, the functions of Kerberos...
2025-09-2851 min
InfoSec BitesISO 27005: A Strategic Deep Dive into Information Security Risk ManagementThe discussion in this podcast provides an extensive comparative analysis of two leading information security risk management methodologies: the ISO/IEC 27005 standard and the NIST Risk Management Framework (RMF). It establishes that modern organisations require a proactive, systematic approach to manage persistent cyber threats and details the philosophical differences, with ISO 27005 being a flexible, global standard for enterprise-wide Information Security Management Systems (ISMS), and NIST RMF being a prescriptive, U.S.-centric framework used primarily for achieving a formal Authority to Operate (ATO) for specific systems. Despite their distinct audiences and purposes, the report concludes that the frameworks are...
2025-09-2735 min
InfoSec BitesCISSP Domain-4: Communication and Network SecurityThe discussion in this podcast provides an extensive overview of networking fundamentals and secure communication channels, primarily focusing on the foundational concepts and technologies within the OSI and TCP/IP models. Key discussions includes the layers of the OSI model (Application, Presentation, Session, etc.) and their functions, as well as a detailed examination of IP addressing (IPv4 and IPv6), routing protocols (distance-vector and link-state), and various network topologies (bus, star, mesh). Furthermore, the dicussion thoroughly covers wireless networking standards (802.11, 802.16), different mobile wireless generations (1G to 5G), and crucial secure protocols like TLS, IPSec, DNSSEC, and S/MIME. Finally, it...
2025-09-2737 min
InfoSec BitesCISSP Domain-3: Architectures, Cryptography, and Physical Security.The podcast disucssion offers an expansive overview of various information technology (IT) and operational technology (OT) concepts, covering system architectures, cryptology, and security architecture design principles. The discussion initially details system architectures, explaining multi-tier server-based systems and the security implications of Industrial Control Systems (ICS), where safety is paramount, particularly in SCADA and DCS environments. A significant portion addresses cryptology, outlining the history of ciphers, the difference between symmetric and asymmetric encryption, key management challenges, and the use of hashing functions for integrity verification. Finally, it introduces security architectures, discussing threat modeling frameworks like STRIDE and the Cyber Kill...
2025-09-271h 17
InfoSec BitesCISSP Domain-2: Asset SecurityThe discussion in this podcast provides a comprehensive overview of asset and data security, focusing heavily on information as an organisation's most valuable asset. The podcast details the data life cycle—from acquisition to destruction—and stresses the critical importance of data classification based on sensitivity and criticality to determine appropriate security controls. Furthermore, the discussion explores the three states of data (at rest, in motion, and in use) and discuss various protection methods, including data loss prevention (DLP) solutions and the roles of key personnel such as data owners and custodians.
2025-09-2732 min
InfoSec BitesCISSP Domain-1: Security, Risk, and Compliance ManagementIn this podcast we discuss a comprehensive overview of cybersecurity governance, risk management, and compliance within an organizational context. It explores the foundational concepts of the CIA triad (confidentiality, integrity, and availability), along with authenticity and nonrepudiation, and details the development of an enterprise-wide security program supported by management. Furthermore, it examines various risk management frameworks (RMFs), such as the NIST RMF and ISO/IEC 27005, and contrasts quantitative and qualitative risk analysis methodologies. A significant portion addresses the legal and regulatory landscape, including international laws like the GDPR and US statutes, intellectual property protection, and different types of investigations...
2025-09-2740 min
InfoSec BitesAWS GuardDuty: Threat Hunting Beyond Alerts, Architecture and IncidentsThe discussion in this podcast provides a comprehensive analysis of Amazon GuardDuty, an intelligent, fully managed threat detection service within the AWS ecosystem. It explains the service's multi-layered architecture, which combines machine learning, anomaly detection, and curated threat intelligence feeds to monitor core data sources like CloudTrail and VPC Flow Logs. The discussion stresses that GuardDuty functions as a detective control critical to a defense-in-depth strategy, and its true power is realized through seamless integration and automation with other AWS services such as Security Hub, Amazon Detective, and Lambda for rapid incident response and containment. Furthermore, it positions GuardDuty...
2025-09-2531 min
InfoSec BitesXSS, CSRF, and SSRF Analysis: Web Application Forgeries.The podcast discussion provides an extensive analysis of three major web application security flaws: Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and Server-Side Request Forgery (SSRF). It explains that these attacks exploit weaknesses in the web's foundational trust relationships, with XSS compromising user trust, CSRF exploiting the website's trust in the browser, and SSRF leveraging a server's internal network trust. It categorizes XSS into three vectors—Reflected, Stored, and DOM-based—detailing their mechanisms and objectives, which include credential theft and data manipulation. Finally, the analysis maps these techniques to the MITRE ATT&CK framework and stresses the necessity of a la...
2025-09-2447 min
InfoSec BitesAWS Security Incident Lessons: Customer Failure ArchetypesThe discussion in this podcast provides a detailed analysis of significant security incidents involving Amazon Web Services (AWS) and consistently conclude that the vast majority of major breaches stem from customer-side failures rather than flaws in AWS infrastructure. This principle is governed by the AWS Shared Responsibility Model, which dictates that customers are responsible for security in the cloud, managing elements like configurations, data, and access controls. The discussion examines high-profile cases, including Capital One, Uber, and Code Spaces, categorizing common root causes into four primary archetypes: leaked credentials, misconfigured cloud services, insider threats, and resource abuse like cryptojacking...
2025-09-2039 min
InfoSec BitesAWS IAM: Architecture, Security, and Incident AnalysisThe discussion in this podcast provides an extensive overview of AWS Identity and Access Management (IAM), describing it as the foundational service governing all resource access within the AWS ecosystem. It details IAM’s core architectural components, including Users, Groups, Roles, and Policies, emphasizing the use of temporary credentials and the Principle of Least Privilege. Furthermore, it explains the complex policy evaluation logic and advanced security features such as Service Control Policies (SCPs) and Permissions Boundaries used for setting enterprise-wide guardrails. Finally, it reviews the crucial alignment of IAM with frameworks like NIST and analyzes major security incidents to il...
2025-09-1939 min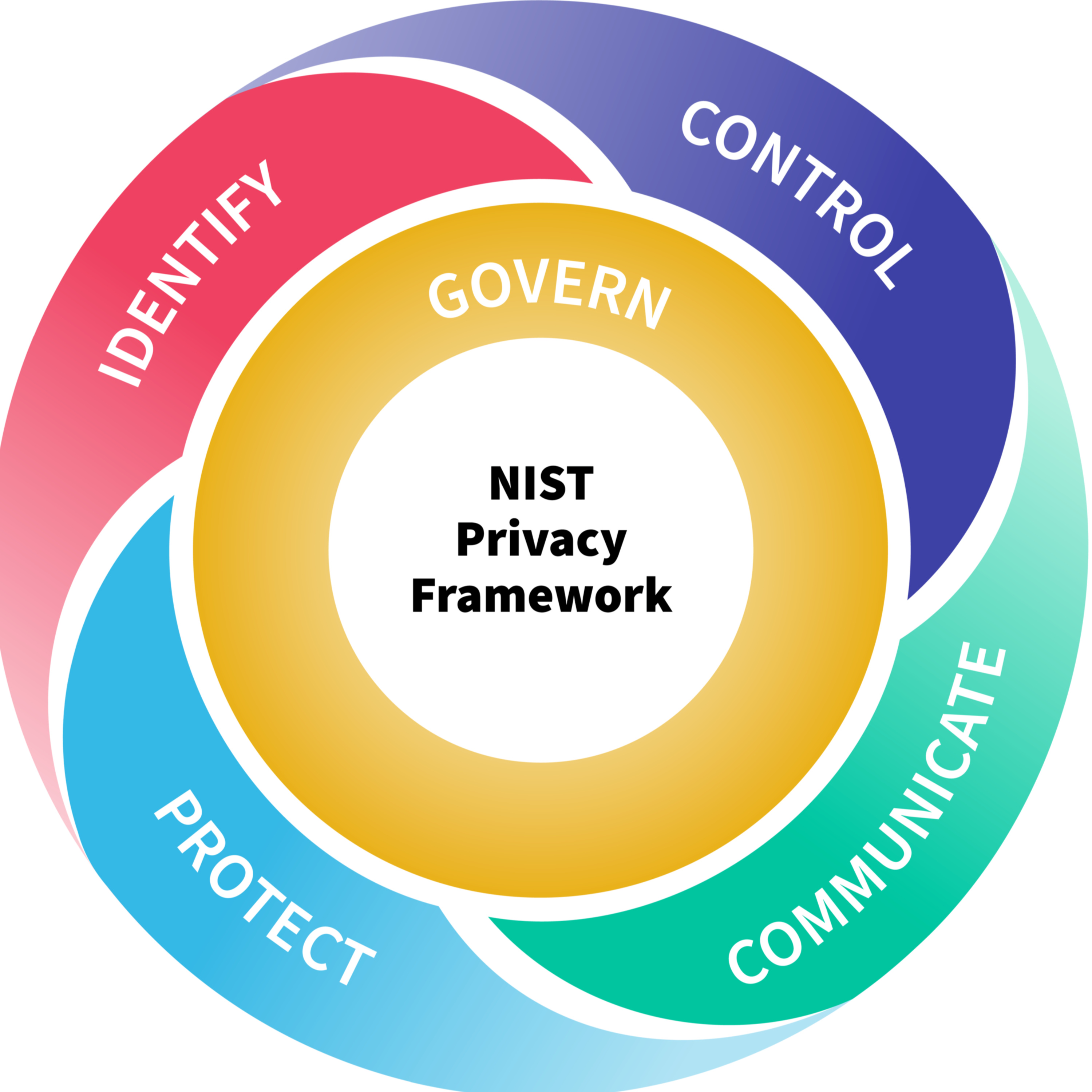
InfoSec BitesNIST Privacy Framework: Enterprise Risk Management for the Digital AgeThis podcast discussion is about NIST Privacy Framework which is a voluntary, risk-based tool designed to assist organisations in managing the complex privacy challenges of the digital age. It distinguishes privacy risk from cybersecurity risk, highlighting that privacy issues can arise even when systems function as intended. The framework is structured around a Core of five functions (Identify-P, Govern-P, Control-P, Communicate-P, and Protect-P), which are customised through Profiles and assessed for maturity via Implementation Tiers. Continuously evolving, with Version 1.1 incorporating guidance for AI risks and aligning with the Cybersecurity Framework 2.0, it promotes a "privacy by design" approach and integration...
2025-09-191h 18
InfoSec BitesAWS Container Security, Architecture and Incident ResponseThe discussion in this podcast offers a comprehensive expert analysis of container security on Amazon Web Services (AWS), focusing on the architectures and security trade-offs of services like EKS, ECS, and Fargate. It thoroughly explains the nuances of the AWS Shared Responsibility Model, emphasizing that most security failures are caused by customer-side misconfigurations, such as overly permissive IAM roles and poor secrets management. It examines real-world security incidents, including the Capital One breach and the SCARLETEEL campaign, to illustrate how attackers use initial vulnerabilities to escalate privileges and move laterally. Finally, the analysis presents a strategic security framework, advocating...
2025-09-1935 min
InfoSec BitesNIST Risk Management Framework: Cybersecurity's Gold StandardThe discussion in this podcast comprehensively outlines the NIST Risk Management Framework (RMF), presenting it as the definitive gold standard for cybersecurity governance in the United States federal government. It details the RMF's evolution from a compliance-focused model to a dynamic, risk-based, and continuous process, particularly highlighting its seven sequential steps: Prepare, Categorise, Select, Implement, Assess, Authorise, and Monitor. The document emphasises the RMF's symbiotic relationship with supporting NIST publications like FIPS 199, FIPS 200, and SP 800-53, which provide its foundational principles and comprehensive control catalogue. Furthermore, it distinguishes the RMF from the NIST Cybersecurity Framework (CSF) by their respective...
2025-09-1934 min
InfoSec BitesUber 2022 Data Breach: How an 18 Year Old Hacker Exploited Human NatureThe discussion in this podcast analyzes the Uber 2022 data breach, detailing how a multi-vector attack exploited both technical vulnerabilities and human weaknesses. It explains that the incident began with a compromised contractor password and escalated through MFA fatigue social engineering, ultimately leading to a full network compromise via hardcoded administrative credentials. The report emphasizes the need for a fundamental shift in security philosophy, advocating for proactive cyber resilience through enhanced third-party risk management, human-centric security awareness, and robust technical controls aligned with NIST frameworks. Ultimately, the breach serves as a case study for improving enterprise security posture and building...
2025-09-1850 min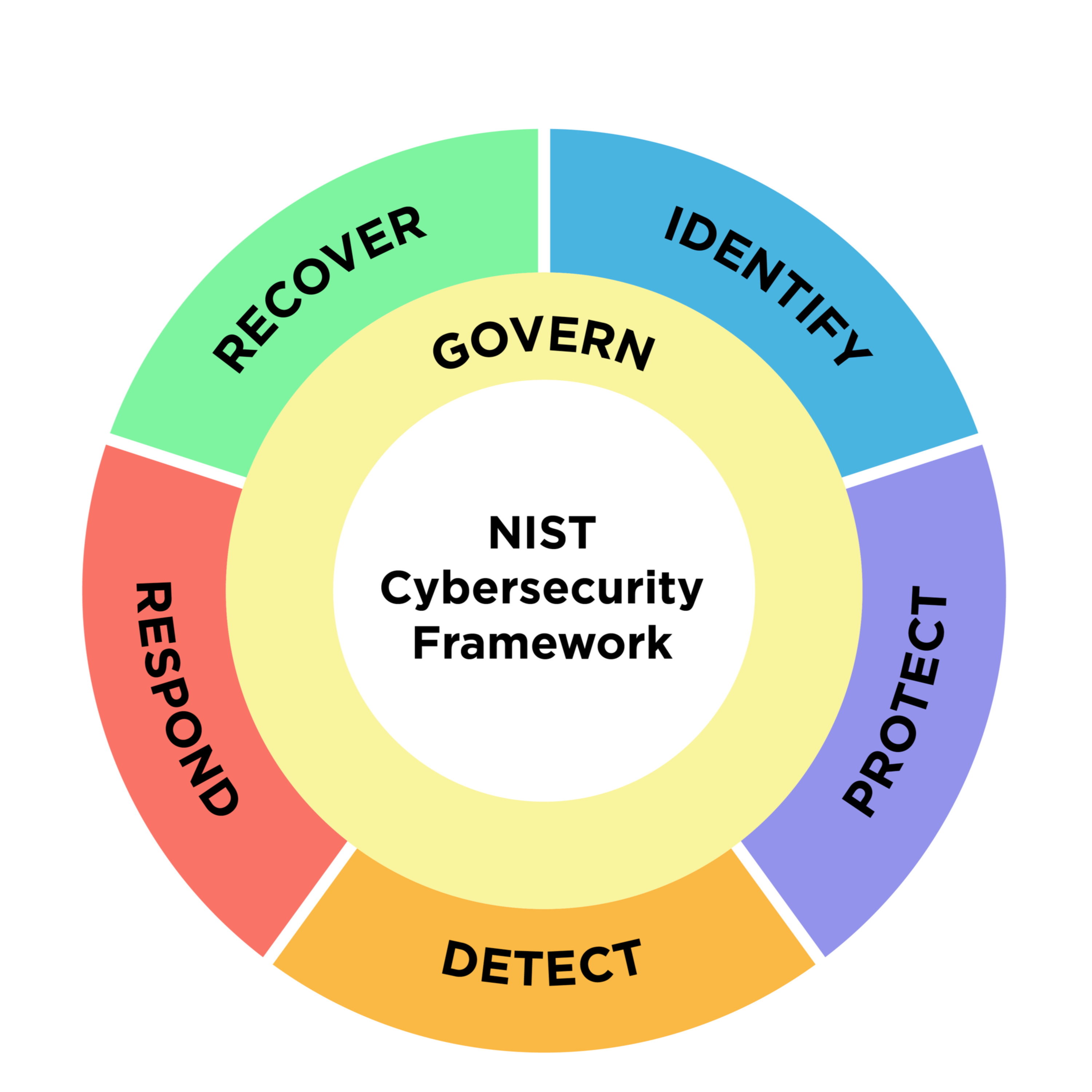
InfoSec BitesNIST Cybersecurity Framework: A Guide to Digital ResilienceThe discussion in this podcast offers a comprehensive analysis of the NIST Cybersecurity Framework (CSF), detailing its evolution from a critical infrastructure directive to a globally applicable guide for digital risk management, particularly highlighting the significant enhancements introduced in CSF 2.0. It meticulously explains the framework's three core components: the Framework Core, which outlines six key functions (Govern, Identify, Protect, Detect, Respond, Recover); Implementation Tiers, serving as a maturity model for risk management practices; and Profiles, which allow organisations to customise the framework to their specific needs. The discussion also draws a clear distinction between the strategic purpose of the...
2025-09-1855 min
InfoSec BitesIPv6 on AWS: Architecture, Benefits, and SecurityThe discussion on this podcast offers a comprehensive overview of IPv6 implementation on AWS, detailing its strategic importance and practical application. The discussion explains how IPv6 addresses the exhaustion of IPv4 addresses and the economic imperative driven by AWS's charging for public IPv4 addresses. The dicussions further outlines the technical advantages of IPv6, such as simplified network architecture, reduced NAT reliance, and enhanced security features like mandatory IPsec. Furthermore, it provides step-by-step guides for dual-stack and IPv6-only VPC configurations, cover the integration of IPv6 with various AWS services, and highlight real-world case studies demonstrating its benefits in scalability...
2025-09-171h 00
InfoSec BitesQuantum Supremacy: Reshaping the FutureThis podcast discusses around Michio Kaku's 2023 book, "Quantum Supremacy," which explores the revolutionary potential of quantum computing. Kaku's work describes how this emerging technology, leveraging principles like superposition and entanglement, could solve complex global challenges in areas such as medicine, energy, and climate modeling. While acknowledging the transformative promise and milestones like Google's Sycamore, it also present critiques regarding Kaku's optimistic speculations, highlighting current limitations like decoherence, high error rates, and scalability issues. The book's structure is outlined, moving from foundational quantum mechanics to speculative societal applications, all while addressing the geopolitical "quantum arms race" and the need for...
2025-09-161h 00
InfoSec BitesDigital Forensics: Unmasking the secret world of digital ghostIn this podcast we explore the multifaceted field of digital forensics, detailing the tools, techniques, and ethical considerations involved in uncovering digital evidence. It explains how specialised software like EnCase and Autopsy, alongside hardware cloners and write-blockers, are used for disk imaging, file carving, and timeline analysis to reconstruct events from fragmented data. The discussion also highlight real-world applications, such as tracking ransomware, debunking deepfakes, and investigating intellectual property theft, while emphasising the critical importance of chain of custody and balancing truth-seeking with individual privacy. Finally, we touch upon the future of the discipline, acknowledging challenges like encrypted data...
2025-09-1520 min
InfoSec BitesAWS API Gateway: Architecture, Use Cases, and SecurityThe dicussion in this podcast offers a comprehensive analysis of AWS API Gateway, outlining its architecture, various use cases, and robust security features. It explains how API Gateway acts as a managed entry point for APIs, simplifying traffic management, authentication, and authorization for backend services. The dicussion distinguishes between REST, HTTP, and WebSocket API types, detailing their respective features, performance characteristics, and cost implications. Furthermore, it covers integration patterns, lifecycle management, and strategies for performance optimization and API monetization, concluding with best practices for secure and efficient deployment.
2025-09-141h 07
InfoSec BitesDeep Dive: Mobile Apps and Unpacking Its Hidden SecurityThe dicussion in this podcast offers a comprehensive overview of mobile application security, exploring its foundational architecture, prevalent threats, and effective defenses. It examines the security implications of different development paradigms—native, hybrid, and cross-platform—and dissects the layered architecture of mobile applications, emphasizing the roles of presentation, business logic, and data access. The discussion then analyzes the distinct security models of iOS and Android, highlighting hardware and software-based protections, and details common vulnerabilities using the OWASP Mobile Top 10 framework, discussing attacker tactics and the debate surrounding TLS pinning. Finally, it presents case studies of high-impact data breaches to illu...
2025-09-141h 09
InfoSec BitesOWASP API Security Top-10(2023): Essential Deep DiveThe podcast dicussion introduces the OWASP API Security Top 10 (2023) list, which identifies the most critical security risks facing APIs today, highlighting that many threats arise from fundamental architectural and implementation flaws rather than complex exploits. The dicussion details each of the ten vulnerabilities, including Broken Object Level Authorization (BOLA) and Broken Authentication, explaining their exploitation methods, potential impacts, and crucial mitigation strategies. Emphasizing a proactive, defense-in-depth approach, the document underscores the importance of security by design, rigorous validation, and comprehensive inventory management to protect against issues like Security Misconfiguration and Improper Inventory Management. Ultimately, this dicussion serves as a...
2025-09-141h 43
InfoSec BitesVulnerability Management and Scoring SystemsIn this podcast we discuss vulnerability management, a crucial cybersecurity practice involving the identification, assessment, prioritisation, resolution, and continuous monitoring of weaknesses in computer systems and networks. A key tool highlighted is the Common Vulnerability Scoring System (CVSS), an open framework for quantifying the severity of vulnerabilities through a numerical score (0-10) derived from base, temporal, and environmental metrics. While CVSS is widely adopted, including by the National Vulnerability Database (NVD), some sources note its limitations for granular risk prioritisation, advocating for integration with asset criticality and exploit prediction scoring systems (EPSS). The podcast also details the role of...
2025-09-131h 56
InfoSec BitesLattice-Based Post-Quantum Cryptography: A Comprehensive GuideThe podcast collectively offers a comprehensive overview of lattice-based post-quantum cryptography (PQC), detailing its fundamental principles and practical applications. It explains how traditional cryptographic methods are vulnerable to quantum computers and introduce lattices as a quantum-resistant solution. It discusses the mathematical foundations of lattices, focusing on their "hard problems" like the Shortest Vector Problem (SVP) and the Closest Vector Problem (CVP), which form the basis of security. Key algorithms such as Learning With Errors (LWE) and Short Integer Solution (SIS), including their Ring-LWE (RLWE) and Module-LWE (MLWE) variants, are presented as core engines for constructing secure systems. Finally, we...
2025-09-131h 08
InfoSec BitesSession Cookies: The Digital Passport to Your Online LifeThe discussion in this Podcast comprehensively discuss session cookies, explaining their fundamental role in maintaining user state across stateless HTTP connections, which is crucial for personalized web experiences like online shopping or persistent logins. The discussion thoroughly details the inherent weaknesses of these cookies, such as their susceptibility to theft on unsecured networks, predictability if poorly generated, and potential for manipulation. They then outline various exploitation methods, including session hijacking, fixation, and cross-site scripting (XSS), supported by real-world examples like Firesheep and the TJX breach. Crucially, the discussion also provides robust security measures, emphasizing the use of flags like...
2025-09-131h 08
InfoSec BitesMicroservices Unpacked: Architecture, Principles, Security, and Strategic ImplicationsThe discussion in this podcast offers a comprehensive analysis of microservices architecture, contrasting it with traditional monolithic systems. It explores the foundational principles guiding microservices, such as Domain-Driven Design and the Single Responsibility Principle, and details the significant business benefits, including enhanced scalability, improved resilience, and faster time-to-market. The discussion also addresses the technical complexities of microservices, covering inter-service communication, service discovery, and modern deployment strategies. Crucially, it highlights the security challenges inherent in distributed systems, emphasizing the importance of a "security-by-design" approach, and illustrates these points with case studies of major security incidents at Capital One and Uber...
2025-09-131h 15
InfoSec BitesAPIs & Gateways: The Invisible Digital BackboneThe discussion in this podcast offers an in-depth analysis of Application Programming Interfaces (APIs) and API gateways, outlining their architectural roles as foundational components in modern software development. It explains how APIs facilitate software communication and drive business innovation, detailing various API types and their strategic importance. It also highlights the critical function of API gateways as centralized traffic managers that enhance security and streamline complex microservices architectures by offloading concerns like authentication and rate limiting. A significant portion focuses on API security, discussing common vulnerabilities identified by OWASP, particularly Broken Object Level Authorization (BOLA), and emphasizing the need...
2025-09-131h 14
InfoSec BitesOWASP Top-10 A02 Cryptographic Failures: The Encryption ExploitThe Podcast, "Cryptographic Failures: A Comprehensive Guide," presents an in-depth exploration of vulnerabilities stemming from improper or inadequate use of cryptographic techniques. It explains that these failures, ranked highly on the OWASP Top 10, lead to the exposure or compromise of sensitive data through issues like weak encryption, poor key management, or insecure transport protocols. The guide details various attack scenarios and uses the 2017 Equifax breach as a real-world case study to illustrate the severe consequences. Ultimately, the discussion offers extensive prevention techniques, tools, and testing methodologies to help organizations safeguard sensitive information and maintain compliance.
2025-09-1343 min
InfoSec BitesPasskeys: Passwordless future and its hidden trapsThis Podcast comprehensively discusses passkeys as a cutting-edge, passwordless authentication method built on public-key cryptography. It explains that passkeys involve a private key stored securely on a user's device and a public key held by the service, enabling login through simple actions like fingerprint or PIN, thus replacing traditional passwords. The discussion highlights the necessity of passkeys due to the inherent weaknesses of passwords, such as vulnerability to phishing, data breaches, and brute-force attacks, while improving user experience. It details the robust security of passkeys, particularly their phishing resistance and the fact that no sensitive data leaves the device...
2025-09-1232 min
InfoSec BitesOSI Layer-7 Application Layer Incident ResponseThe podcast discussion comprehensively explores the Application Layer (OSI Layer-7), focusing on incident response strategies. It examines various protocols, including HTTP, HTTPS, DNS, SMTP, and FTP, alongside application-specific APIs. It details incident response tactics for common threats like web application attacks, injection flaws, cross-site scripting, CSRF, API abuse, and zero-day exploits, using real-world case studies such as the Equifax breach and Log4Shell. Furthermore, it outlines the use of playbooks and runbooks for operational responses, aligning with industry standards like NIST, SANS, and ISO, and addresses forensics at Layer-7 through log analysis and packet capture. The discussion also projects...
2025-09-1245 min
InfoSec BitesOSI Layer-6 Presentation Layer: Incident ResponseThe discussion in this podcast outlines a comprehensive incident response playbook specifically for the OSI Presentation Layer (Layer 6), a critical component responsible for data formatting, compression, and encryption. It begins by introducing the Presentation Layer's role and functions, explaining how it ensures interoperability, security, and efficiency in network communications through protocols like SSL/TLS, JPEG, and XML. The playbook then details various vulnerabilities and threats that target this layer, including encryption-related attacks, data format exploits, and compression-based attacks. Finally, it provides a structured incident response framework—following the NIST model—with prerequisites, workflows, checklists, and specific playbooks for common scen...
2025-09-1235 min
InfoSec BitesHeartbleed CVE-2014-0160: The invisible flaw that bled the internet dryThe dicussion in this podcast offers a comprehensive overview of the Heartbleed bug, a critical security flaw identified as CVE-2014-0160. This vulnerability stemmed from improper input validation within specific, outdated versions of the OpenSSL cryptographic library, particularly concerning the TLS Heartbeat extension. Attackers could exploit this "buffer over-read" to extract sensitive data, such as private keys, passwords, and other confidential information, from affected systems without leaving a trace. The bug's widespread impact prompted an urgent need for patching to OpenSSL version 1.0.1g or later, as well as the reissuance of compromised certificates and password changes for users. Heartbleed...
2025-09-1216 min
InfoSec BitesAI Powered OSINTThe dicussion in this podcast explores how artificial intelligence (AI) is revolutionising open-source intelligence (OSINT), which is derived from publicly available data. It highlights that AI technologies, such as machine learning, natural language processing, and computer vision, significantly enhance the speed and scale of OSINT activities for various sectors including governments, law enforcement, journalists, and corporations. The discussion details specific AI tools and their applications in real-world scenarios, ranging from tracking cybercrime and disinformation to investigating war crimes and monitoring protests. However, it also critically examines the strategic and ethical implications of AI-powered OSINT, raising concerns about mass surveillance...
2025-09-1247 min
InfoSec BitesThe Invisibe Web: Your Public Digital FootprintThe dicussion in this podcast critically examines the pervasive myth of digital anonymity, arguing that individuals' online presence is a fragmented collection of data points, readily discoverable and aggregated. It differentiates between the surface, deep, and dark web, clarifying that publicly accessible personal data resides on the surface web, even if it's "invisible" to the average user without specialised tools. The discussion then introduces Open-Source Intelligence (OSINT) as the process of connecting these disparate digital "breadcrumbs" to form detailed profiles. It highlights the significant role of data brokers and the concept of digital permanence, demonstrating how seemingly innocuous information...
2025-09-1253 min
InfoSec BitesOSINT(Open Source Intelligence): Threats & Digital Self-DefenseDiscussion in this podcast explores the concept of Open Source Intelligence (OSINT), defining it as the systematic collection and analysis of publicly available information. It highlights OSINT's dual-use nature, demonstrating how the same techniques employed for legitimate purposes like investigating war crimes can be weaponised against individuals through doxxing, social engineering, and identity theft. It details the mechanics of OSINT, differentiating between passive and active methods, and identifies numerous sources of personal exposure, including social media, public records, and IoT devices. Finally, it offers a practical guide to digital self-defence, emphasising mindful sharing, privacy settings management, and the implementation...
2025-09-1251 min
InfoSec BitesPublic Key Infrastructure(PKI): Invisible Architect of Digital TrustThis podcast discusses the critical concept of digital trust and its implementation within enterprises, highlighting the challenges organisations face in establishing and maintaining it. The 2024 State of Digital Trust Report by DigiCert, explores how enterprises are performing across various areas such as Enterprise IT, IoT & Connected Devices, Software, and eSignature trust, revealing that while digital trust is considered vital, maturity levels are generally low. It also identifies key challenges like lack of staff expertise, network complexity, and management support, while distinguishing between "leaders" and "laggards" in these efforts. Concurrently, it also provides an overview of how digital certificates work...
2025-09-121h 04
InfoSec BitesIPsec Deep Dive: Security, Vulnerabilities, and Quantum EvolutionThis podcast offer a comprehensive examination of the Internet Protocol Security (IPsec) suite, detailing its role in securing network-layer communications. The discussion explain IPsec's foundational security features, including confidentiality, integrity, authentication, and replay protection, and how these are delivered by its constituent protocols like Authentication Header (AH) and Encapsulating Security Payload (ESP). The discussion further illuminate IPsec's operational modes (Transport and Tunnel), its reliance on the Internet Key Exchange (IKE) protocol for key management, and its specific cryptographic algorithms. Crucially, it addresses prevalent vulnerabilities, misconfigurations, and historical security incidents, highlighting the practical challenges of implementation. Finally, the discussion converge...
2025-09-1257 min
InfoSec BitesS/MIME, PGP, and GPG: Securing Digital Communication for True PrivacyIn this podcast discussion explores email encryption technologies, primarily PGP (Pretty Good Privacy), GPG (GNU Privacy Guard), and S/MIME (Secure/Multipurpose Internet Mail Extension). Discussion details how these systems use public and private key cryptography for confidentiality, authentication, and integrity in digital communication. While all aim to secure emails, it highlights their fundamental differences, particularly in their trust models – PGP/GPG utilise a "web of trust", whereas S/MIME relies on a hierarchical Public Key Infrastructure (PKI) with Certificate Authorities (CAs). It also discuss practical and theoretical vulnerabilities, such as pass-phrase compromises, public key tampering, operating system weaknesses, Tr...
2025-09-1020 min
InfoSec BitesInjection Vulnerabilities: A Comprehensive GuideThis podcast "Injection Vulnerabilities: A Comprehensive Guide," offers an extensive examination of injection vulnerabilities, which are a critical cybersecurity threat. It details how these flaws arise when untrusted user input is processed by interpreters without proper validation or sanitisation, enabling attackers to execute malicious code. The guide categorises various types of injection, including SQL, Command, NoSQL, and LDAP injection, explaining their technical underpinnings and common attack scenarios. Furthermore, it highlights the real-world impact through a case study of the 2018 Panera Bread SQL injection breach, underscoring the importance of robust prevention techniques such as parameterized queries and input validation. The...
2025-09-0916 min
InfoSec BitesOSI Presentation Layer: Security, Exploits, and DefensesThe podcast discussion offers a comprehensive overview of cybersecurity threats across the Open Systems Interconnection (OSI) model's various layers, with a particular focus on the Presentation Layer. They detail how each layer, from the Physical Layer to the Application Layer, is susceptible to specific types of attacks, such as sniffing, IP spoofing, SYN floods, session hijacking, and malware. A significant portion of the discussion then outlines mitigation strategies and best practices for each layer, including secure configurations, strong encryption, intrusion detection systems, and regular updates. Furthermore, the texts explore the critical role of the Presentation Layer (Layer 6) in data...
2025-09-081h 03
InfoSec BitesInvisible Frontline: Decoding OSI Layer-7 Application Layer Incident ResponseThe discussion in this podcast outlines a strategic framework for responding to cybersecurity incidents that specifically target the application layer (Layer 7) of the OSI model. It emphasizes the shift in threat landscape from network-level to more sophisticated application-level attacks, which mimic legitimate user behavior and are harder to detect. The topic details a structured approach to incident response, differentiating between high-level Incident Response Plans, scenario-specific Playbooks, and step-by-step Runbooks. It also covers the phases of incident response—preparation, detection and analysis, containment, eradication, recovery, and post-incident activity—highlighting the importance of proactive measures, cross-functional teams, and essential security tools. It f...
2025-09-081h 02
InfoSec BitesOSI Application Layer 7 Security: Exploits and DefenseThe podcast offers an extensive overview of the Open Systems Interconnection (OSI) Application Layer (Layer 7), explaining its role as the interface between users and network services. It contrasts the OSI model with the TCP/IP model, highlighting how the OSI framework aids in understanding security vulnerabilities and the necessity of tools like Web Application Firewalls (WAFs). The discussion further explores various Application Layer protocols such as HTTP/HTTPS, FTP/SFTP, email protocols, and DNS, detailing their mechanisms and inherent security weaknesses. Finally, it examines common Layer 7 exploits, including injection attacks, authentication failures, DDoS attacks, and security misconfigurations, alongside comprehensive...
2025-09-081h 25
InfoSec BitesOpen Source Intelligence(OSINT): Real-World Applications and Case StudiesThis podcast discusses the growing threat of cybercrime and the critical role of Open-Source Intelligence (OSINT) in both perpetrating and defending against these attacks. It highlights how Artificial Intelligence (AI) is rapidly advancing phishing and social engineering tactics, making it harder for individuals and organisations to detect fraudulent schemes. The discussion emphasises the importance of managing one's digital footprint by being cautious about shared information on social media platforms like Facebook and Instagram, and online reviews. The dangers of inadvertently revealing personal and professional data that can be harvested by threat actors for targeted attacks are a recurring theme...
2025-09-0854 min
InfoSec BitesAdvanced Persistant Threat(APT): Who are they? What do they want?This podcast offers a humorous yet comprehensive guide to Advanced Persistent Threats (APTs), defining them as highly sophisticated and persistent cyber-attacks, often orchestrated by nation-states or well-resourced criminal groups. It explains that these actors, unlike typical hackers, infiltrate systems to remain undetected for extended periods, engaging in activities like espionage, sabotage, or financial theft. The overview further outlines the motivations behind APTs, such as geopolitical advantage and intellectual property acquisition, and illustrates their impact through numerous high-profile incidents like Stuxnet and SolarWinds. Ultimately, the source emphasises the evolving nature of these threats and the critical need for robust cybersecurity...
2025-09-0858 min
InfoSec BitesSecure Hash Algorithm (SHA): A Comprehensive Analysis-Foundations, Evolution, Applications, and Post-Quantum ResilienceThis podcast offers a comprehensive overview of the **Secure Hash Algorithm (SHA)** family, detailing its **evolution from SHA-0 to SHA-3** and its critical role in digital security. It explains that SHA functions act as **one-way digital fingerprints**, ensuring **data integrity, authenticity, and non-repudiation** across diverse applications like digital signatures, password storage, and blockchain technology. It differentiates between the **Merkle-Damgård construction** of SHA-1 and SHA-2, highlighting SHA-1's deprecation due to collision vulnerabilities and SHA-2's current security, while introducing SHA-3's **sponge construction** as a more resilient and versatile design. Furthermore, we explore **quantum threats** from algorithms like G...
2025-09-0855 min
InfoSec BitesVulnerability Management: Understanding CVE, CVSS, and NVDThis Podcast primarily discusses cybersecurity vulnerabilities and the Common Vulnerability Scoring System (CVSS), an open framework for rating their severity. They explain that vulnerabilities are flaws in computer systems that malicious actors can exploit, and highlight the National Vulnerability Database (NVD), a US government database that enriches Common Vulnerabilities and Exposures (CVEs) with additional information, including CVSS scores. The discussion details the CVSS framework, which comprises base, temporal, and environmental metric groups that contribute to a score from 0 to 10, indicating the severity of a threat. While acknowledging the widespread use of CVSS for vulnerability management and prioritizing responses, one...
2025-09-081h 08
InfoSec BitesNavigating Cryptographic Agility: A Deep Dive into Resilient SecurityThis podcast comprehensively discusses cryptographic agility, defining it as the essential ability of digital systems to seamlessly and rapidly adapt their cryptographic components without operational disruption. It emphasizes that this adaptability is no longer a luxury but a strategic imperative driven by the constant evolution of cyber threats, past failures of inflexible systems like DES and SHA-1, and the looming existential threat of quantum computing via algorithms like Shor's. The discussion outlines architectural blueprints for achieving agility at protocol, software, and hardware layers, highlighting the importance of modular design, APIs, and negotiation mechanisms while also acknowledging challenges like increased...
2025-09-0751 min
InfoSec BitesQuantum Computing's Rapid Ascent in 2025: Milestones and Dual ImpactThe dicussion in this podcast portrays 2025 as a pivotal year for quantum computing, marked by its transition from theoretical promise to practical application, leading to its designation as the International Year of Quantum Science and Technology. It outlines significant advancements in hardware and software by major companies like Google, IBM, Microsoft, and Amazon, each pursuing distinct strategies toward achieving fault-tolerant quantum computers by the end of the decade. The discussion emphasizes the dual impact of this progress: immense potential to revolutionize fields like drug discovery and finance, alongside an urgent threat to current encryption methods, necessitating a rapid shift...
2025-09-071h 07
InfoSec BitesAustralia's Post-Quantum Cryptography(PQC) Readiness: Challenges and ImperativesThis Podcast discusses Australia's preparedness for post-quantum cryptography (PQC), which is essential to secure digital systems against the emerging threat of quantum computers that could render current encryption obsolete. The discussion highlights Australia's ambitious 2030 deadline for transitioning to PQC, five years earlier than some allies, demonstrating a strong strategic intent to counter the "Harvest Now, Decrypt Later" threat, where encrypted data is collected today for future decryption. The discussion identifies China as the principal and most imminent threat due to its significant quantum investments and history of cyber espionage. While Australia possesses a robust policy framework and invests in...
2025-09-071h 01
InfoSec BitesThreats, Vulnerabilities, and Risk: A Comprehensive GuideIn this podcast we discuss cybersecurity risk management and vulnerability management, outlining systematic approaches to identify, assess, and address weaknesses in information systems. Several sources, including NIST Special Publication 800-30, detail the fundamental steps of risk assessment, which involve identifying threats, vulnerabilities, and the potential impact and likelihood of their exploitation. Wiz and Splunk elaborate on the lifecycle of vulnerability management, emphasising discovery, prioritisation, remediation, validation, and reporting, often supported by specialised tools and cross-team collaboration. The CISA Known Exploited Vulnerabilities Catalog provides concrete examples of identified vulnerabilities and associated mitigation actions, illustrating the practical application of these concepts...
2025-09-0619 min
InfoSec BitesOSI Model: Your Data's Journey through the invisible layers of the Internet!The podcast discusses the OSI (Open Systems Interconnection) model, a conceptual framework that standardizes how data communicates across networks. The discussion details its seven distinct layers, from the Physical Layer (Layer 1), handling raw bit transmission, to the Application Layer (Layer 7), which interfaces with user software. The articles illustrate how data undergoes encapsulation—adding information as it travels down the layers on the sender's side—and decapsulation—removing this information as it moves up the layers on the receiver's side—using real-world examples like sending photos or browsing websites. While acknowledging that the TCP/IP model is more prevalent in practica...
2025-09-0647 min
InfoSec BitesRSA Encryption: The silent guardian facing quantum revolution!Discussion in this Podcast offers a comprehensive overview of RSA encryption, a foundational public-key cryptosystem invented by Rivest, Shamir, and Adleman. Discussion explains its historical context, including its independent discovery by Clifford Cocks and its critical role in solving the key distribution problem. The texts detail the intricate mathematical principles behind RSA, particularly modular arithmetic and prime factorization, and outline the step-by-step processes of key generation, encryption, decryption, and digital signing. Crucially, it addresses RSA's vulnerabilities arising from implementation flaws and the existential threat posed by quantum computing via Shor's algorithm, ultimately describing the transition to post-quantum cryptography (PQC...
2025-09-061h 27
InfoSec BitesMosca's Theorem: Are you ready for Quantum threat(Q-Day)?The podcast discusses Mosca's Theorem, a critical framework for assessing and mitigating the cybersecurity risks posed by future quantum computers. This theorem, often expressed as the inequality (X+Y)>Z, highlights the urgency of preparing for a "Store Now, Decrypt Later" attack, where encrypted data is harvested today for future decryption by powerful quantum machines. X represents the required security lifespan of data, Y signifies the time needed for an organization to migrate to quantum-safe systems, and Z is the estimated time until a cryptographically relevant quantum computer becomes operational. The theorem emphasizes that if the sum of X...
2025-09-0656 min
InfoSec BitesElliptic Curve Cryptography: Foundations, Applications, and Quantum FutureDiscussion in this podcast provides a comprehensive overview of Elliptic Curve Cryptography (ECC), a modern public-key encryption method. They explain that ECC leverages the Elliptic Curve Discrete Logarithm Problem (ECDLP) for its security, allowing for smaller key sizes and greater efficiency compared to traditional algorithms like RSA. It details ECC's mathematical foundations, including curve definitions and point operations, and illustrate its widespread applications in areas like secure web communication (TLS), cryptocurrencies, and mobile devices. Crucially, we also discuss implementation vulnerabilities and highlight the existential threat posed by quantum computing via Shor's algorithm, leading to the necessary development and adoption...
2025-09-061h 15
InfoSec BitesCryptographic Agility: A Strategic Imperative for Cybersecurity ResilienceThis podcast thoroughly explain cryptographic agility as a vital, proactive cybersecurity strategy, defining it as a system's ability to swiftly and seamlessly swap cryptographic algorithms without disruption. It emphasizes that this capability is critical for responding to new threats, vulnerabilities, and regulatory changes, especially with the impending risk of quantum computers rendering current encryption obsolete. The discussion details the historical cycle of cryptographic obsolescence and the technical and organizational barriers to achieving agility, advocating for modular design, automation, and a centralized inventory of cryptographic assets. Ultimately, the sources position cryptographic agility not as a mere technical feature, but as...
2025-09-0646 min
InfoSec BitesUnveiling Blockchains: Beyond Bitcoins, True Power in our world!The discussion in this podcast explores blockchain technology's expanding influence beyond cryptocurrencies, presenting it as a foundational shift in data management. It highlights its core principles of decentralization, immutability, and transparency as crucial for building trust and efficiency in various industries. The discussion details real-world applications in areas such as supply chain management, healthcare, identity verification, and intellectual property, showcasing how blockchain addresses challenges like fraud and inefficiency. While acknowledging hurdles like scalability and interoperability, it forecasts significant market growth and enterprise adoption, emphasizing blockchain's role as a "behind-the-scenes" utility for automating trust and facilitating transparent interactions in the...
2025-09-0650 min
InfoSec BitesAES Encryption Explained: Your invisible online guardian!This Podcast offers a comprehensive overview of the Advanced Encryption Standard (AES), detailing its origins, technical mechanics, and paramount importance in modern cryptography. It explains that AES, a symmetric-key block cipher, was established by NIST through a transparent, global competition to replace its predecessor, DES, due to its enhanced security with 128, 192, or 256-bit key lengths. It meticulously describe AES's Substitution-Permutation Network (SPN) design, highlighting the SubBytes, ShiftRows, MixColumns, and AddRoundKey transformations that ensure confusion and diffusion. While acknowledging AES's unassailable core algorithm against practical attacks, the discussion emphasize that most vulnerabilities stem from implementation flaws, side-channel attacks, or insecure...
2025-09-0649 min
InfoSec BitesIPv6: Unpacking the Internet's infinite future and why we need it NOW!The discussion in this Podcast offers a comprehensive overview of Internet Protocol Version 6 (IPv6), detailing its origin, features, and implementation. It explains how IPv6 was developed to address IPv4 address exhaustion by introducing a significantly larger address space (128-bit addresses compared to IPv4's 32-bit). Key advantages and technical aspects of IPv6 are highlighted, including multicasting as a replacement for broadcast communication, stateless address autoconfiguration (SLAAC), and the structure of IPv6 packet headers with their extension headers. It also discuss transition mechanisms like dual-stack implementation and tunnelling, acknowledging the complexity of migrating from IPv4 while emphasising the security benefits...
2025-09-061h 13
InfoSec BitesWeb3: Allure, Abyss, and the Decentralized Wild WestIn this Podcast we explore Web3, describing it as the next generation of the internet that aims for decentralization through blockchain technology, cryptocurrencies, and tokens. Discussion highlights Web3's potential to transform financial services by reducing costs and fostering innovation in areas like payments and lending, as well as its ability to empower creators and offer enhanced user experiences through AI, 3D graphics, and VR/AR. However, the texts also address significant challenges, including scalability issues, the lack of skilled talent, environmental concerns related to Proof of Work consensus mechanisms, and the prevalence of scams, hacks, and regulatory complexities...
2025-09-061h 34
InfoSec BitesPhishing: The Art of Digital Deception"Phishing: The Art of Digital Deception," Podcast offers a comprehensive overview of phishing attacks, explaining this prevalent form of cybercrime where malicious actors trick individuals into revealing sensitive information. It details numerous types of phishing, from the classic email phishing and personalized spear phishing to voice-based vishing and text-based smishing, illustrating how these tactics are employed in daily life. It also highlights the devastating financial, reputational, and emotional damage that phishing can inflict on both individuals and businesses. Furthermore, it examines the psychological exploitation tactics used by attackers and provides real-world examples of major cyber incidents, such as the...
2025-09-0635 min
InfoSec BitesGoogle Chrome: Capabilities, Security, and VulnerabilitiesThe podcast dicusses comprehensive overview of Google Chrome's architecture, security mechanisms, and vulnerabilities. It highlights Chrome's multi-process design, which isolates components like the browser, renderer, and GPU processes to enhance stability, fault tolerance, and security through sandboxing. It also explains key technical components such as the Blink rendering engine and the V8 JavaScript engine, emphasizing their role in performance. A significant portion details Chrome's robust security posture, including features like Site Isolation, Google Safe Browsing, automatic updates, and secure Inter-Process Communication (IPC). Finally, we discuss common vulnerability classes, such as memory corruption and zero-day exploits, and recount major security...
2025-09-0626 min
InfoSec BitesThe Quantum Internet: A Hybrid FrontierIn this podcast we discuss comprehensive overview of the quantum internet, describing it as a transformative evolution of global communication that will operate as a hybrid classical-quantum network. It explains that this next-generation infrastructure harnesses quantum mechanics principles like superposition and entanglement through qubits to enable unprecedented security and efficiency. The dicussion highlight the primary driver for its development as the looming threat of fault-tolerant quantum computers rendering current cryptography obsolete, introducing the "harvest now, decrypt later" concern. Furthermore, it details architectural components such as quantum nodes, memories, and repeaters, acknowledging significant technical and engineering challenges like qubit fragility...
2025-09-0629 min
InfoSec BitesQuantum Crossroads: Securing Our Digital Future from Distributed Quantum Computing ThreatsLets explores the challenges and opportunities presented by quantum computing, particularly focusing on the urgent need for Post-Quantum Cryptography (PQC). We details how distributed quantum computing (DQC) is overcoming hardware limitations to create powerful quantum machines, which in turn pose an existential threat to current encryption methods. The report highlights the "Harvest Now, Decrypt Later" strategy, where adversaries collect encrypted data today for future decryption by quantum computers, emphasizing the immediate risk to long-term data confidentiality. It outlines the NIST standardization process for PQC algorithms and offers a strategic roadmap for organizations to migrate to these new, quantum-resistant standards...
2025-09-061h 03
InfoSec BitesHomomorphic Encryption: Securing Data in UseIn this Podcast we introduce and explain homomorphic encryption (HE), a groundbreaking cryptographic method that permits computations directly on encrypted data without prior decryption. We highlight how HE addresses critical security gaps in "data-in-use," where traditional encryption methods fall short. It categorizes HE into partially, somewhat, and fully homomorphic schemes, with fully homomorphic encryption (FHE) being the most robust, allowing unlimited operations through techniques like bootstrapping, despite its current computational overhead. The discussion also explore diverse applications of HE, including secure cloud computing, privacy-preserving AI and machine learning, healthcare analytics, financial fraud detection, and secure voting, underscoring its role...
2025-09-0617 min
InfoSec BitesUnravelling TLS 1.2: Security, Handshake, and VulnerabilitiesIn this Podcast we discuss, "Exploiting SSL/TLS Vulnerabilities in Modern Technologies" by Simreen Kaur Matharu, comprehensively examines cryptography fundamentals, the evolution of SSL/TLS protocols, and a timeline of significant security attacks against these protocols. It details various attack methods, such as BEAST, CRIME, Lucky13, Heartbleed, POODLE, FREAK, and ZOMBIE POODLE, explaining their mechanisms and mitigation strategies, with practical demonstrations of some vulnerabilities. The secondary source, "Is TLS 1.2 Deprecated? Key Difference from TLS 1.3" by Tolu Michael, focuses on the increasing deprecation of TLS 1.2, highlighting its vulnerabilities compared to the more secure TLS 1.3 and providing guidance for transitioning to...
2025-09-0622 min
InfoSec BitesEmail Forensics: Uncovering Digital EvidencesThis podcast collectively provides a comprehensive overview of email forensics, defining it as a specialized discipline within digital forensics crucial for investigating cybercrimes and legal disputes. It explains that email forensics systematically recovers and analyzes email data to determine authenticity, origin, and content, emphasizing that this goes beyond mere message review. It details a structured, multi-phase forensic lifecycle, including identification, collection, preservation, analysis, reporting, and testimony, all designed to maintain a legally defensible chain of custody. The Podcast highlights the critical importance of analyzing email headers and metadata to trace an email's path, verify authenticity using protocols like SPF...
2025-09-0646 min
InfoSec BitesData Breach & Spill: PII & PHI ExplainedThis podcast comprehensively explains the critical differences between data breaches and data spills, highlighting how both expose sensitive information. It clarifies that data breaches typically involve unauthorized, often malicious, access to data, while data spills are the result of accidental exposure due to errors or misconfigurations. It details the significance of Personally Identifiable Information (PII) and Protected Health Information (PHI) within these incidents, using real-world examples to illustrate their impact on individuals and organizations. Furthermore, it outlines common causes for each incident and recommends preventative measures along with legal and regulatory considerations, such as HIPAA and GDPR.
2025-09-0613 min
InfoSec BitesZero Trust: Digital Survival Guide in a Treacherous Online WorldIn this podcast, discussing Zero Trust, a cybersecurity framework that operates on the principle of "never trust, always verify." It highlights how this model assumes all users and devices are potential threats until their legitimacy is continuously validated, moving away from older perimeter-based security. The discussion outlines key principles such as least privilege access, continuous monitoring, and robust identity verification, while also exploring the tools and techniques used to implement Zero Trust, including multi-factor authentication and network segmentation. It stresses the necessity of Zero Trust in an era of sophisticated cyber threats and human error, despite acknowledging the challenges...
2025-09-0638 min
InfoSec BitesConfidentiality Integrity Availability(CIA Triad): The ultimate guideThis podcast offers an extensive and often humorous exploration of the CIA Triad, a foundational concept in information security comprising Confidentiality, Integrity, and Availability. It explains each principle in detail, using sarcastic and satirical examples to illustrate common security failures and their consequences. The podcast outlines various tools and strategies for upholding each aspect of the Triad, such as encryption and access controls for confidentiality, hashing and digital signatures for integrity, and redundancy and disaster recovery for availability. Ultimately, it underscores the critical importance of the CIA Triad in preventing data breaches and system failures, often attributing these issues...
2025-09-0646 min
InfoSec BitesAuthentication Authorisation & Accounting: Digital fortress of Information SecurityThis podcast explains the three core pillars of digital security: Authentication, Authorisation, and Accounting (AAA). Authentication involves verifying a user's identity through methods like passwords, physical tokens, or biometrics, with a focus on the increased security of multi-factor authentication. Following this, Authorisation determines a user's permissions and access levels to specific resources, highlighting different control models such as role-based or attribute-based access. Finally, Accounting tracks and logs all user activities to monitor for security incidents and maintain an audit trail. The article uses an engaging, satirical tone to discuss the challenges and complexities of implementing effective AAA systems, from...
2025-09-0640 min
InfoSec BitesTrusted Platform Module(TPM): Invisible Hardware Guardian Against Cyber ThreatsIn this podcast we offer a comprehensive overview of the Trusted Platform Module (TPM), a specialised hardware chip crucial for modern computer security. We explain what a TPM is, detailing its internal components like cryptographic engines, unique keys, and Platform Configuration Registers (PCRs), which enable secure operations. It also describe how TPMs function, from generating and storing keys to verifying system integrity during boot-up, underpinning features like secure boot and full-disk encryption. Furthermore, it discusses the critical need for TPMs in safeguarding data and authenticating devices in today's threat landscape. Finally, assess the security of TPMs, acknowledging their strengths...
2025-09-061h 11
InfoSec BitesQuantum Computing: A Deep Dive, from spooky action to world changing technologyThis podcast collectively offers a comprehensive overview of quantum computing, explaining its fundamental principles and future implications. They clarify how quantum bits (qubits), utilising superposition and entanglement, enable quantum computers to tackle problems beyond the reach of traditional machines, such as drug discovery and optimisation. We also highlight the dual nature of quantum computing for cybersecurity, noting its potential to both break existing encryption with algorithms like Shor's and offer unbreakable communication through quantum key distribution (QKD). Furthermore, we discuss the current challenges in developing these systems, particularly decoherence and the need for error-corrected logical qubits, while showcasing real-world...
2025-09-0656 min
InfoSec BitesThe Harvest Now, Decrypt Later Threat and Quantum computing: What we must do today?In this podcast we discuss the "Harvest Now, Decrypt Later" (HNDL) threat, a critical and immediate cyber security risk where adversaries, primarily nation-states and sophisticated cybercrime groups, are actively stockpiling encrypted data today, anticipating future decryption by quantum computers. This data, particularly long-lived sensitive information like medical records, intellectual property, and government secrets, will become vulnerable when cryptographically relevant quantum computers (CRQCs) capable of breaking current encryption (like RSA and ECC) become available. Organisations are urged to immediately begin migrating to post-quantum cryptography (PQC), a complex and phased process requiring crypto-agility and re-encryption for critical data, as highlighted by...
2025-09-0636 min
InfoSec BitesGovernance Risk & Compliance(GRC): Study GuideThis podcast about "Risk and Information Systems Control ," provides a comprehensive overview of risk management and information system controls, primarily designed as a study aid. It explores key concepts such as identifying threats and vulnerabilities, developing risk scenarios, and understanding information security goals like confidentiality, integrity, and availability. The guide details various risk management frameworks and methodologies, including the NIST Risk Management Framework and ISACA's Risk IT Framework, along with different types of controls (administrative, technical, physical) and their assessment. Furthermore, it covers legal and regulatory requirements influencing risk management, such as HIPAA and FISMA, and outlines methods for...
2025-09-0656 min
InfoSec BitesOWASP Top 10 A01 -Broken Access Control: A Comprehensive Guide, why the #1 Web vulnerability threatens your digital securityIn this guide we examine Broken Access Control, identified by OWASP as the number one security risk in 2021, due to its widespread occurrence and severe impact. It details how applications fail to adequately restrict user actions or access, enabling attackers to view private data or perform unauthorised tasks. It explains various types of access control (such as Role-Based Access Control) and common vulnerabilities, including Insecure Direct Object References (IDOR) and missing function-level access control. Furthermore, it outlines attack scenarios, illustrates prevention techniques through secure coding practices and architectural best practices, and highlights the real-world implications with a case study...
2025-09-0622 min
InfoSec Bites2025's Top Cyber IncidentIn this podcast we outline four major cybersecurity incidents from 2025, highlighting the diverse and evolving threat landscape. It details attacks ranging from sophisticated social engineering campaigns like the attempted infiltration of SentinelOne by PurpleHaze, to large-scale ransomware breaches such as the Coinbase password leak. We also discuss critical software vulnerabilities exemplified by CitrixBleed 2 and the phishing-led heist against UK retailers. For each incident, it explains the vulnerability exploited, detection methods, remediation steps, and controls applied, offering a comprehensive overview of how these significant cyber threats unfolded and were addressed.
2025-09-0641 min
InfoSec BitesThe Explainer: AWS WAF, Shield and Firewall ManagerIn this podcast we provide a comprehensive overview of AWS WAF, a web application firewall that helps protect web applications from common web exploits. It explains how to set up and configure WAF accounts, including user creation and tool downloads, and details the creation and management of protection packs, web ACLs, and rules, including different rule actions like allow, block, count, CAPTCHA, and challenge. The text further explores intelligent threat mitigation features like AWS WAF Fraud Control (ACFP and ATP) and Bot Control, along with the use of tokens for client session tracking and validation. Additionally, it covers monitoring...
2025-09-0645 min
InfoSec BitesEssential Eight Cybersecurity Maturity ModelIn this podcast we collectively outline the Australian Signals Directorate's (ASD) Essential Eight cybersecurity mitigation strategies, designed to protect organisations from various cyber threats. The Essential Eight maturity model details four levels, from zero to three, indicating increasing sophistication in mitigating cyber attacks and targeting. The Essential Eight assessment process guide provides instructions for evaluating an organisation's adherence to these maturity levels, including guidance on evidence quality and assessment outcomes. Furthermore, the Essential Eight maturity model and ISM mapping document correlates the Essential Eight requirements with the Information Security Manual (ISM), offering a framework for implementing and assessing cyber...
2025-09-061h 10
InfoSec BitesBrowser: The New Cybersecurity BattlegroundIn this episode we are discussing a fundamental shift in cybersecurity from "How the Browser Became the Main Cyber Battleground", where attackers increasingly target web browsers rather than traditional local network endpoints. This change is driven by the "SaaS-ification" of enterprise IT, meaning core business systems are now accessed online via browsers, making user identities and their associated credentials the primary target. The discussion highlights phishing as the most impactful weapon for identity-driven breaches and points out that while attackers have adapted, security measures have not kept pace. Finally, it proposes that the browser itself offers the ideal platform...
2025-09-0617 min
InfoSec BitesQuantum AI: Future Computing and Its ImpactsIn this podcast lets discuss the intersection of quantum computing and artificial intelligence, exploring their individual capabilities and combined impact, particularly on cybersecurity and data protection. This podcast highlights the fundamental differences between classical and quantum AI, with quantum systems utilising qubits for parallel processing, offering significant speed advantages for specific problems. A major theme is the threat quantum computers pose to current cryptographic methods, such as RSA, and the urgent need for quantum-resistant solutions, including post-quantum cryptography like lattice-based and code-based systems, and quantum key distribution. We also touch on the practical integration of these emerging technologies into...
2025-09-061h 08
InfoSec BitesQuantum Threat to CryptographyThis podcast collectively explore the profound impact of quantum computing on information security, examining both threats and solutions. They consistently highlight Shor's and Grover's algorithms as significant dangers to current public-key and symmetric cryptography, respectively. We also universally present Quantum Key Distribution (QKD) and Post-Quantum Cryptography (PQC) as crucial countermeasures, with a particular focus on NIST's PQC standardisation efforts. Across the summaries, there is a strong emphasis on the "harvest now, decrypt later" threat and the urgent need for organisations to adopt crypto-agile strategies and hybrid security models to prepare for a quantum-resilient future. They discuss the practical applications...
2025-09-0659 min
InfoSec BitesOWASP Top 10 (2021) Comprehensive GuideThe OWASP Top 10 (2021) Comprehensive Guide provides a detailed overview of the ten most critical web application security risks, identifying prevalent and impactful vulnerabilities. It outlines various categories such as Broken Access Control, Cryptographic Failures, and Injection, explaining their technical details, common attack scenarios, and real-world case studies. The guide offers practical prevention techniques, including code examples and recommended tools, to help developers and organisations mitigate these risks effectively. Emphasising the importance of secure design and continuous monitoring, it serves as a crucial resource for building and maintaining robustly secure applications.
2025-09-0626 min
InfoSec BitesInformation Security Manual(ISM): Principles and GuidelinesThis podcast present two distinct perspectives on success and security. The first source, an Information Security Manual (ISM), outlines a comprehensive cybersecurity framework for organisations, detailing guidelines and principles across five key functions: govern, identify, protect, detect, and respond. It emphasizes risk management, the importance of evaluated products, secure IT equipment maintenance, and personnel security training, with specific controls for various data classifications (e.g., OFFICIAL: Sensitive, PROTECTED, SECRET, TOP SECRET).
2025-09-0637 min
InfoSec BitesMITRE ATT&CK Matrices: Decoding a Cyberattack's PlaybookThis Podcast offers a comprehensive overview of the MITRE ATT&CK framework, a standardised model for understanding cyber adversary behaviours. It details four distinct matrices: Enterprise, Mobile, Industrial Control Systems (ICS), and Cloud, each tailored to specific technological environments. For each matrix, the document explains various tactics—the objectives of an attack—and their associated techniques—the methods used to achieve those objectives. Real-world examples are integrated throughout to illustrate how these tactics and techniques manifest in actual cyber incidents, such as the SolarWinds attack or the Pegasus spyware. This resource serves to help organisations map threats, improve detection capabi...
2025-09-0622 min
InfoSec BitesPost-Quantum Cryptography(PQC): Preparing for the Quantum MenacePost-Quantum Cryptography (PQC), highlighting its critical role in safeguarding digital security against the imminent threat of quantum computers. They explain that PQC involves developing new algorithms resistant to quantum attacks, which could otherwise break current encryption methods like RSA and ECC, primarily through Shor's algorithm. The video detail the NIST standardisation process, which has identified key PQC algorithms such as lattice-based ML-KEM and ML-DSA, and hash-based SLH-DSA, with code-based HQC as a backup, noting their varying strengths and weaknesses. They underscore the urgency of PQC migration due to the "Harvest Now, Decrypt Later" threat, where adversaries store encrypted data...
2025-09-0651 min
InfoSec BitesAI's role in Cyber SecurityThe provided text summarises Nimeshkumar Patel's 2025 book, "Securing the Future: Harnessing AI in Cybersecurity," which explores the crucial role of Artificial Intelligence in combating evolving cyber threats. The book details AI's applications in areas such as advanced threat detection, automated incident response, identity management, and vulnerability management, showcasing how these technologies enhance security. It also addresses the significant ethical and legal considerations involved in deploying AI, including privacy, bias, and accountability. Through various real-world case studies, Patel illustrates the tangible benefits and challenges of integrating AI into cybersecurity practices. Finally, the work looks ahead to future trends and potential...
2025-09-0644 min