Shows
 IT SPARC CastTop 10 Hackers That Ran Afoul of the Law and Then Made GoodIn this week’s episode of IT SPARC Cast - Top Ten, hosts John Barger and Lou Schmidt dive into the darker side of tech turned bright. We’re counting down the Top 10 Hackers That Ran Afoul of the Law and Then Made Good. These are real-life stories of rogue coders, phone phreaks, worm creators, and cyber anarchists who got busted but eventually turned things around to use their skills to do good—some became teachers, consultants, or even government allies.Ranked from least to most positive impact, this episode highlights infamous names like Kevin Mitnick, Marcus...2025-04-0939 min
IT SPARC CastTop 10 Hackers That Ran Afoul of the Law and Then Made GoodIn this week’s episode of IT SPARC Cast - Top Ten, hosts John Barger and Lou Schmidt dive into the darker side of tech turned bright. We’re counting down the Top 10 Hackers That Ran Afoul of the Law and Then Made Good. These are real-life stories of rogue coders, phone phreaks, worm creators, and cyber anarchists who got busted but eventually turned things around to use their skills to do good—some became teachers, consultants, or even government allies.Ranked from least to most positive impact, this episode highlights infamous names like Kevin Mitnick, Marcus...2025-04-0939 min IntrusionsInDepth Podcast005.1: Lapsus$ | The APTeens and INTERNET JOYRIDINGEpisode Description:In this episode of Intrusions and Depth, Josh Stepp unpacks the audacious rise and chaotic downfall of the Lapsus$ hacking collective. Known for targeting some of the biggest names in technology, including Microsoft, Nvidia, and Rockstar Games, this group rewrote the playbook on cybercrime with tactics as unconventional as their teenage leadership. From SIM-swapping and MFA fatigue attacks to social engineering and public Telegram boasts, Josh examines how Lapsus$ exposed glaring vulnerabilities in global cybersecurity defenses while raising ethical questions about balancing punishment and rehabilitation for young offenders.Main Topics Discussed:...2024-12-231h 34
IntrusionsInDepth Podcast005.1: Lapsus$ | The APTeens and INTERNET JOYRIDINGEpisode Description:In this episode of Intrusions and Depth, Josh Stepp unpacks the audacious rise and chaotic downfall of the Lapsus$ hacking collective. Known for targeting some of the biggest names in technology, including Microsoft, Nvidia, and Rockstar Games, this group rewrote the playbook on cybercrime with tactics as unconventional as their teenage leadership. From SIM-swapping and MFA fatigue attacks to social engineering and public Telegram boasts, Josh examines how Lapsus$ exposed glaring vulnerabilities in global cybersecurity defenses while raising ethical questions about balancing punishment and rehabilitation for young offenders.Main Topics Discussed:...2024-12-231h 34 Digital DesperadosEpisode #31 – Samy Kamkar: A Hacker’s Quick Pivot to CyberSecurity This week, Digital Desperados takes a lighthearted stroll through the story of Samy Kamkar, a hacker who quickly found out that hacking isn’t a game. Remember MySpace? (Yes, it’s the “classic rock” of social media.) Back in 2005, teenage Samy created the “Samy Worm,” a harmless-yet-viral hack that declared him a hero on over a million profiles before getting him in major trouble with the Secret Service. Fast forward and Samy has become a cybersecurity trailblazer, exposing vulnerabilities in everything from RFID credit cards to IoT gadgets like drones and car systems. Along the way, Samy’s work has reve...2024-11-2720 min
Digital DesperadosEpisode #31 – Samy Kamkar: A Hacker’s Quick Pivot to CyberSecurity This week, Digital Desperados takes a lighthearted stroll through the story of Samy Kamkar, a hacker who quickly found out that hacking isn’t a game. Remember MySpace? (Yes, it’s the “classic rock” of social media.) Back in 2005, teenage Samy created the “Samy Worm,” a harmless-yet-viral hack that declared him a hero on over a million profiles before getting him in major trouble with the Secret Service. Fast forward and Samy has become a cybersecurity trailblazer, exposing vulnerabilities in everything from RFID credit cards to IoT gadgets like drones and car systems. Along the way, Samy’s work has reve...2024-11-2720 min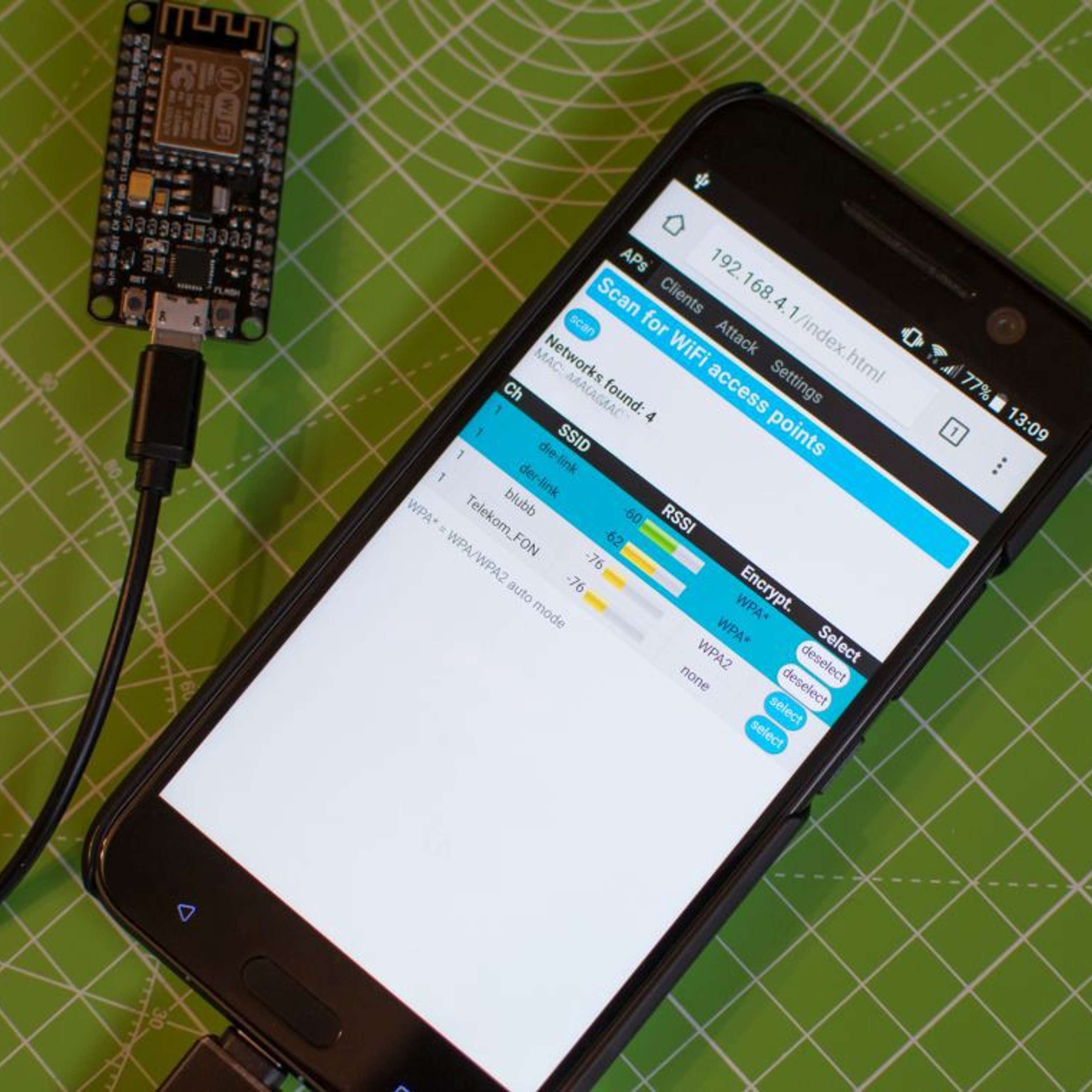 Futurism Tech Brief By HackerNoonDeauthentication attack and other ‘wifi hacks’ using an ESP8266 module.
This story was originally published on HackerNoon at: https://hackernoon.com/deauthentication-attack-and-other-wifi-hacks-using-an-esp8266-module-14f9142b063d.
As famed wifi hacker Samy Kamkar recently said we should move towards low-cost hacking/exploitation tools. NodeMCU is one of such tools, a LUA based firmware for the ESP8266 WiFi SOC under $5.
Check more stories related to futurism at: https://hackernoon.com/c/futurism.
You can also check exclusive content about #iot, #wifi, #infosec, and more.
This story was written by: @tomac. Learn more about this writer by checking @tomac's about page,
and for more stories, please visit hackernoon...2024-04-1904 min
Futurism Tech Brief By HackerNoonDeauthentication attack and other ‘wifi hacks’ using an ESP8266 module.
This story was originally published on HackerNoon at: https://hackernoon.com/deauthentication-attack-and-other-wifi-hacks-using-an-esp8266-module-14f9142b063d.
As famed wifi hacker Samy Kamkar recently said we should move towards low-cost hacking/exploitation tools. NodeMCU is one of such tools, a LUA based firmware for the ESP8266 WiFi SOC under $5.
Check more stories related to futurism at: https://hackernoon.com/c/futurism.
You can also check exclusive content about #iot, #wifi, #infosec, and more.
This story was written by: @tomac. Learn more about this writer by checking @tomac's about page,
and for more stories, please visit hackernoon...2024-04-1904 min The Amp Hour Electronics Podcast#658 – Uncle Al’s Eating Garbage Again
AI tools for recording
32 bit recording
Pool robot
Home assistant
Power points in the ceiling in Dave’s office park
CH32V003 board
CNLohr episode
rv003usb library
Mike Harrison doing a video about a CH32V003 standalone programmer
nRF24
Low cost modules Chris bought on Amazon
Samy Kamkar on the show
Samy talk about balloons
Drone shows
Time difference of distances
Dave’s video about HP atomic clocks
XKCD Radiation Dose Chart
DTCXO
In the Bond movies they’re not nerds
LCD and fonts
AI pin
Vision Pro
iFixit teardown
Chris will be at Embedded World again this y...2024-02-131h 07
The Amp Hour Electronics Podcast#658 – Uncle Al’s Eating Garbage Again
AI tools for recording
32 bit recording
Pool robot
Home assistant
Power points in the ceiling in Dave’s office park
CH32V003 board
CNLohr episode
rv003usb library
Mike Harrison doing a video about a CH32V003 standalone programmer
nRF24
Low cost modules Chris bought on Amazon
Samy Kamkar on the show
Samy talk about balloons
Drone shows
Time difference of distances
Dave’s video about HP atomic clocks
XKCD Radiation Dose Chart
DTCXO
In the Bond movies they’re not nerds
LCD and fonts
AI pin
Vision Pro
iFixit teardown
Chris will be at Embedded World again this y...2024-02-131h 07 The Amp Hour Electronics Podcast#658 – Uncle Al’s Eating Garbage Again
AI tools for recording
32 bit recording
Pool robot
Home assistant
Power points in the ceiling in Dave’s office park
CH32V003 board
CNLohr episode
rv003usb library
Mike Harrison doing a video about a CH32V003 standalone programmer
nRF24
Low cost modules Chris bought on Amazon
Samy Kamkar on the show
Samy talk about balloons
Drone shows
Time difference of distances
Dave’s video about HP atomic clocks
XKCD Radiation Dose Chart
DTCXO
In the Bond movies they’re not nerds
LCD and fonts
AI pin
Vision Pro
iFixit teardown
Chris will be at Embedded World again this y...2024-02-131h 07
The Amp Hour Electronics Podcast#658 – Uncle Al’s Eating Garbage Again
AI tools for recording
32 bit recording
Pool robot
Home assistant
Power points in the ceiling in Dave’s office park
CH32V003 board
CNLohr episode
rv003usb library
Mike Harrison doing a video about a CH32V003 standalone programmer
nRF24
Low cost modules Chris bought on Amazon
Samy Kamkar on the show
Samy talk about balloons
Drone shows
Time difference of distances
Dave’s video about HP atomic clocks
XKCD Radiation Dose Chart
DTCXO
In the Bond movies they’re not nerds
LCD and fonts
AI pin
Vision Pro
iFixit teardown
Chris will be at Embedded World again this y...2024-02-131h 07 Deep FutureSamy is My Hero — Samy Kamkar
This is probably the conversation I had in mind when I decided to start this podcast. Samy Kamkar is an old buddy of mine, a genius hacker. When you guys hear me praising the minds of hackers and how brilliant they can be and how they think, Samy is the example in my mind that I’m thinking of, and I always love to share him.
Samy’s famous for having written a computer virus that he was using to meet girls on the internet, which is probably ill-advised. The virus he wrote took over MySpace. It was in...2024-01-041h 29
Deep FutureSamy is My Hero — Samy Kamkar
This is probably the conversation I had in mind when I decided to start this podcast. Samy Kamkar is an old buddy of mine, a genius hacker. When you guys hear me praising the minds of hackers and how brilliant they can be and how they think, Samy is the example in my mind that I’m thinking of, and I always love to share him.
Samy’s famous for having written a computer virus that he was using to meet girls on the internet, which is probably ill-advised. The virus he wrote took over MySpace. It was in...2024-01-041h 29 The Host Unknown PodcastEpisode 170 - The No Show Notes EpisodeThis week in InfoSec (08:56)With content liberated from the “today in infosec” twitter account and further afield2006: The http://wikileaks.org domain name was registered, though the first document wasn't posted to WikiLeaks until December.Assange taken from Ecuador embassy in April 2019, since been staying at his majesty’s pleasure at Belmarsh.2005: The Samy worm, the first self-propagating cross-site scripting worm, was released onto the mega-popular MySpace by 19-year-old Samy Kamkar (@samykamkarHe's since made numerous impactful security and privacy field contributions. https://en.m.wikiped...2023-10-0648 min
The Host Unknown PodcastEpisode 170 - The No Show Notes EpisodeThis week in InfoSec (08:56)With content liberated from the “today in infosec” twitter account and further afield2006: The http://wikileaks.org domain name was registered, though the first document wasn't posted to WikiLeaks until December.Assange taken from Ecuador embassy in April 2019, since been staying at his majesty’s pleasure at Belmarsh.2005: The Samy worm, the first self-propagating cross-site scripting worm, was released onto the mega-popular MySpace by 19-year-old Samy Kamkar (@samykamkarHe's since made numerous impactful security and privacy field contributions. https://en.m.wikiped...2023-10-0648 min The BootloaderSupersized for SuperconTod shares some of his favorite talks from the recent Supercon conference in Pasadena, CA. Paul and Tod each share one thing they found interesting. Follow Tod on Mastodon: @todbot@mastodon.social Follow Paul on Mastodon: @prcutler@fosstodon.orgShow Notes0:00 Welcome to the Supersize Supercon episode3:17 The Supercon badge8:02 DIY Vacuum Tubes by Nick Pool10:31 Personal Electric Vehicles by Bradley Gawthrop13:00 Samy Kamkar’s Random Walk Exploration15:45 How to Hang and Sell Your Blinky Goodness as Art byChris Combs18:15...2022-12-0525 min
The BootloaderSupersized for SuperconTod shares some of his favorite talks from the recent Supercon conference in Pasadena, CA. Paul and Tod each share one thing they found interesting. Follow Tod on Mastodon: @todbot@mastodon.social Follow Paul on Mastodon: @prcutler@fosstodon.orgShow Notes0:00 Welcome to the Supersize Supercon episode3:17 The Supercon badge8:02 DIY Vacuum Tubes by Nick Pool10:31 Personal Electric Vehicles by Bradley Gawthrop13:00 Samy Kamkar’s Random Walk Exploration15:45 How to Hang and Sell Your Blinky Goodness as Art byChris Combs18:15...2022-12-0525 min Tech with TommyHow to hack a computerHollywood has many ideas about how to hack computers. But, unfortunately, those are mostly not related to reality.
So how do you actually hack a computer? In this episode, we will look at some of the ways nefarious neverdowells have hacked computers in the past and see if we can learn a lesson or two from them.
This is quite a long podcast, so I have included section markers you can pause at if you want.
Links I mentioned in the show:
Yahoo and their medireview https://en.wiktionary.org/wiki/medireview
...2022-11-0643 min
Tech with TommyHow to hack a computerHollywood has many ideas about how to hack computers. But, unfortunately, those are mostly not related to reality.
So how do you actually hack a computer? In this episode, we will look at some of the ways nefarious neverdowells have hacked computers in the past and see if we can learn a lesson or two from them.
This is quite a long podcast, so I have included section markers you can pause at if you want.
Links I mentioned in the show:
Yahoo and their medireview https://en.wiktionary.org/wiki/medireview
...2022-11-0643 min Built for ChangeThe Path to Cyber ResilienceCyber attacks are on the rise – and companies face a constant battle to stay ahead. In 2021, breaches of data, networks, services and other assets climbed by 31%. In this episode, we’ll talk to a former hacker who, years ago, was responsible for one of the fastest-spreading computer viruses in history. We’ll also discuss the risks facing organizations that don’t prioritize the alignment of cybersecurity best practices with their overall business strategy. Our guests this week are Samy Kamkar, C.S.O. at Openpath, and Jacky Fox, the European Lead for Security at Accenture.
2022-06-0127 min
Built for ChangeThe Path to Cyber ResilienceCyber attacks are on the rise – and companies face a constant battle to stay ahead. In 2021, breaches of data, networks, services and other assets climbed by 31%. In this episode, we’ll talk to a former hacker who, years ago, was responsible for one of the fastest-spreading computer viruses in history. We’ll also discuss the risks facing organizations that don’t prioritize the alignment of cybersecurity best practices with their overall business strategy. Our guests this week are Samy Kamkar, C.S.O. at Openpath, and Jacky Fox, the European Lead for Security at Accenture.
2022-06-0127 min Unnamed Reverse Engineering Podcast057 - I Did Not Expect Sharks!Michael Ossmann (@michaelossmann) from Great Scott Gadgets joined us to chat all things SDR, Open Source Hardware, education, and more! Here are links to some of the topics we covered: HackRF One Ubertooth One GreatFET One A Mathematician's Lament WEP Wep dead again article APCO P25 Ettus USRP NTLMv1 Dominic Spill GNU Radio Michael’s KiCon Talk gr-bluetooth Michael’s awesome video series on SDR http://www.nsaplayset.org/ https://en.wikipedia.org/wiki/NSA_ANT_catalog IMSI Catcher DEF CON 22 - Michael Ossmann - The NSA Playset: RF Retroreflectors https://en.wikipedia.org/wiki/The_Thing...2022-05-091h 37
Unnamed Reverse Engineering Podcast057 - I Did Not Expect Sharks!Michael Ossmann (@michaelossmann) from Great Scott Gadgets joined us to chat all things SDR, Open Source Hardware, education, and more! Here are links to some of the topics we covered: HackRF One Ubertooth One GreatFET One A Mathematician's Lament WEP Wep dead again article APCO P25 Ettus USRP NTLMv1 Dominic Spill GNU Radio Michael’s KiCon Talk gr-bluetooth Michael’s awesome video series on SDR http://www.nsaplayset.org/ https://en.wikipedia.org/wiki/NSA_ANT_catalog IMSI Catcher DEF CON 22 - Michael Ossmann - The NSA Playset: RF Retroreflectors https://en.wikipedia.org/wiki/The_Thing...2022-05-091h 37 EmbeddedThis Is the WheyAlvaro Prieto (@alvaroprieto) spoke with us about cheese, making, work, the reverse engineering podcast, weather, and motivation. Alvaro is a host of the Unnamed Reverse Engineering podcast. Some of his favorite episodes include #41 with Samy Kamkar, #14 with Joe Grand, and #23 with Major Malfunction. (Jen Costillo co-hosts the show and has been on Embedded several times.) Alvaro works at Sofar Ocean, making oceanic sensing platforms. He has a personal website linking to his other exploits. We talked about some Embedded episodes as well: #282 with Laughlin Barker about OpenROV #174 with Evan...2021-04-2358 min
EmbeddedThis Is the WheyAlvaro Prieto (@alvaroprieto) spoke with us about cheese, making, work, the reverse engineering podcast, weather, and motivation. Alvaro is a host of the Unnamed Reverse Engineering podcast. Some of his favorite episodes include #41 with Samy Kamkar, #14 with Joe Grand, and #23 with Major Malfunction. (Jen Costillo co-hosts the show and has been on Embedded several times.) Alvaro works at Sofar Ocean, making oceanic sensing platforms. He has a personal website linking to his other exploits. We talked about some Embedded episodes as well: #282 with Laughlin Barker about OpenROV #174 with Evan...2021-04-2358 min BrakeSec Education PodcastSlipstreaming blocked by Chrome, Slack being used for malware, plus dork and deskjockeys! Chrome Blocks Port 10080 to Prevent Slipstreaming Hacks - E Hacking News - Latest Hacker News and IT Security News https://www.reddit.com/r/netsec/comments/jlu3cf/nat_slipstreaming/ Samy Kamkar - NAT Slipstreaming v2.0 Slack and Discord are Being Hijacked by Hackers to Distribute Malware - E Hacking News - Latest Hacker News and IT Security News Texan's alleged Amazon bombing effort fizzles: Militia man wanted to take out 'about 70 per cent of the internet' • The Register Pwn2O...2021-04-1351 min
BrakeSec Education PodcastSlipstreaming blocked by Chrome, Slack being used for malware, plus dork and deskjockeys! Chrome Blocks Port 10080 to Prevent Slipstreaming Hacks - E Hacking News - Latest Hacker News and IT Security News https://www.reddit.com/r/netsec/comments/jlu3cf/nat_slipstreaming/ Samy Kamkar - NAT Slipstreaming v2.0 Slack and Discord are Being Hijacked by Hackers to Distribute Malware - E Hacking News - Latest Hacker News and IT Security News Texan's alleged Amazon bombing effort fizzles: Militia man wanted to take out 'about 70 per cent of the internet' • The Register Pwn2O...2021-04-1351 min Junior to Senior with David GuttmanSamy Kamkar, co-founder of Openpath SecurityTalking Points:
Engineering Team Organization
Networking at Tech Events
Personal Meaning in Side Projects
Accessibility of Side Projects
Importance of Public Speaking Skills
Quotable Quotes:
“It’s really good to join one if these communities and share what you are working on because it’s a great way for people working on similar and really cool projects find you.” - DG
“It’s very hard to be good at something and deliver good results if you’re spending a lot of time with something you don’t enjoy, or just don’t have a lot of passion for.” - DG
...2020-11-3046 min
Junior to Senior with David GuttmanSamy Kamkar, co-founder of Openpath SecurityTalking Points:
Engineering Team Organization
Networking at Tech Events
Personal Meaning in Side Projects
Accessibility of Side Projects
Importance of Public Speaking Skills
Quotable Quotes:
“It’s really good to join one if these communities and share what you are working on because it’s a great way for people working on similar and really cool projects find you.” - DG
“It’s very hard to be good at something and deliver good results if you’re spending a lot of time with something you don’t enjoy, or just don’t have a lot of passion for.” - DG
...2020-11-3046 min Security Now - 16k MP3SN792: "Slipstream" NAT Firewall BypassThis week we look at the dilemma of Let's Encrypt's coming root expiration, new Chrome and Apple zero-day vulnerabilities, some new high-profile ransomware victims, China's Tianfu Cup pwning competition, the retirement of a PC industry insider, the continuing Great Encryption Dilemma, police monitoring of consumers' video, more ongoing pain for WordPress, a note about a sci-fi book event one week from now, and Samy Kamkar's tricky Slipstream attack and its mitigations.2020-11-1100 min
Security Now - 16k MP3SN792: "Slipstream" NAT Firewall BypassThis week we look at the dilemma of Let's Encrypt's coming root expiration, new Chrome and Apple zero-day vulnerabilities, some new high-profile ransomware victims, China's Tianfu Cup pwning competition, the retirement of a PC industry insider, the continuing Great Encryption Dilemma, police monitoring of consumers' video, more ongoing pain for WordPress, a note about a sci-fi book event one week from now, and Samy Kamkar's tricky Slipstream attack and its mitigations.2020-11-1100 min Security Now 2020SN 792: “Slipstream” NAT Firewall BypassThis week we look at the dilemma of Let's Encrypt's coming root expiration, new Chrome and Apple zero-day vulnerabilities, some new high-profile ransomware victims, China's Tianfu Cup pwning competition, the retirement of a PC industry insider, the continuing Great Encryption Dilemma, police monitoring of consumers' video, more ongoing pain for WordPress, a note about a sci-fi book event one week from now, and Samy Kamkar's tricky Slipstream attack and its mitigations.2020-11-101h 38
Security Now 2020SN 792: “Slipstream” NAT Firewall BypassThis week we look at the dilemma of Let's Encrypt's coming root expiration, new Chrome and Apple zero-day vulnerabilities, some new high-profile ransomware victims, China's Tianfu Cup pwning competition, the retirement of a PC industry insider, the continuing Great Encryption Dilemma, police monitoring of consumers' video, more ongoing pain for WordPress, a note about a sci-fi book event one week from now, and Samy Kamkar's tricky Slipstream attack and its mitigations.2020-11-101h 38 Unnamed Reverse Engineering Podcast041 - What did you fail at this week?Jen and Alvaro chat with Samy Kamkar about his new NAT Slipstreaming research and a lot more! Samy is the co-founder of Openpath Security. You can find him on twitter @samykamkar and on his website https://samy.pl. Here are links to some of the topics we covered: NAT Slipstreaming Mr. Robot draw.io DNS SIP Protocol HTTP Protocol OSI Layer IP Fragmentation RFCs IP Fragmentation RFC 791 WebRTC UPnP Netfilter Binwalk ALG IDA Pro Ghidra Rolljam - Car unlocker David Shorey (Patreon) Iridescent Chocolate Fravia.com (archived) Fravia’s Pages of Reverse Engineering RAM Cold...2020-11-071h 31
Unnamed Reverse Engineering Podcast041 - What did you fail at this week?Jen and Alvaro chat with Samy Kamkar about his new NAT Slipstreaming research and a lot more! Samy is the co-founder of Openpath Security. You can find him on twitter @samykamkar and on his website https://samy.pl. Here are links to some of the topics we covered: NAT Slipstreaming Mr. Robot draw.io DNS SIP Protocol HTTP Protocol OSI Layer IP Fragmentation RFCs IP Fragmentation RFC 791 WebRTC UPnP Netfilter Binwalk ALG IDA Pro Ghidra Rolljam - Car unlocker David Shorey (Patreon) Iridescent Chocolate Fravia.com (archived) Fravia’s Pages of Reverse Engineering RAM Cold...2020-11-071h 31 The Backend Engineering Show with Hussein NasserRemotely access any TCP/UDP service bound to a victim machine - Let us discuss NAT SlipstreamingEver heard of HTTP Smuggling? will this is smuggling a TCP packet into an HTTP body so that it can be interpreted by the router to open internal ports to your machine. NAT Slipstreaming was discovered by Samy Kamkar, Article and research by @SamyKamkar https://samy.pl/slipstream/2020-11-0220 min
The Backend Engineering Show with Hussein NasserRemotely access any TCP/UDP service bound to a victim machine - Let us discuss NAT SlipstreamingEver heard of HTTP Smuggling? will this is smuggling a TCP packet into an HTTP body so that it can be interpreted by the router to open internal ports to your machine. NAT Slipstreaming was discovered by Samy Kamkar, Article and research by @SamyKamkar https://samy.pl/slipstream/2020-11-0220 min The Host Unknown PodcastEpisode 27 - Normal Service is ResumedYour regular features and even more, such as vegan sweets, Host Unknown imposters, Jav appears in the press with the same quote for different stories, and HMRC incompetence.Vegan sweetshttps://www.thejealouslife.com/products/tropical-wonderWill the real Host Unknown please stand up? This Week in Infosec5th October 1991: The Linux kernel was released by Linus Torvalds."This is a program for hackers by a hacker." -Linus Benedict TorvaldsFor those keeping score at home, he said "hacker[s]" 4 times in his p...2020-10-091h 01
The Host Unknown PodcastEpisode 27 - Normal Service is ResumedYour regular features and even more, such as vegan sweets, Host Unknown imposters, Jav appears in the press with the same quote for different stories, and HMRC incompetence.Vegan sweetshttps://www.thejealouslife.com/products/tropical-wonderWill the real Host Unknown please stand up? This Week in Infosec5th October 1991: The Linux kernel was released by Linus Torvalds."This is a program for hackers by a hacker." -Linus Benedict TorvaldsFor those keeping score at home, he said "hacker[s]" 4 times in his p...2020-10-091h 01 Lock and CodeInvestigating digital vulnerabilities in our physical world with Samy KamkarA recent history of hacking shows the importance of experimentation. In 2015, security researchers hacked a Jeep Cherokee and took over its steering, transmission, and brakes. In 2019, researchers accessed medical scanning equipment to alter X-ray images, inserting fraudulent, visual signs of cancer in a hypothetical patient.
Today, we're discussing one such experiment—a garage door opener called “Open Sesame.”
Join us for a discussion with "Open Sesame"'s developer, who is also the chief security officer and co-founder of Open Path, Samy Kamkar, to hear about how his tool works, and who holds responsibility for protecting against modern attacks.
2020-09-2832 min
Lock and CodeInvestigating digital vulnerabilities in our physical world with Samy KamkarA recent history of hacking shows the importance of experimentation. In 2015, security researchers hacked a Jeep Cherokee and took over its steering, transmission, and brakes. In 2019, researchers accessed medical scanning equipment to alter X-ray images, inserting fraudulent, visual signs of cancer in a hypothetical patient.
Today, we're discussing one such experiment—a garage door opener called “Open Sesame.”
Join us for a discussion with "Open Sesame"'s developer, who is also the chief security officer and co-founder of Open Path, Samy Kamkar, to hear about how his tool works, and who holds responsibility for protecting against modern attacks.
2020-09-2832 min The Entrepreneur CastHow to Identify and Protect Against Business Risks--Episode 38 - How to Identify and Protect Against Business Risks--Sam McRoberts, CEO of VUDU Marketing and the author of Screw the Zoo, and Jayson DeMers, CEO of EmailAnalytics, discuss How to Identify and Protect Against Business Risks.With many decades of combined business and digital marketing experience, Jayson and Sam will walk you through everything you need to know as you go through your own entrepreneurial journey.Links to things mentioned in the podcast:Catch Me If You Can - movie about Frank AbagnaleKevin MitnickSamy KamkarPablos HolmanThe Definitive Guide to Wordpress...2020-07-2728 min
The Entrepreneur CastHow to Identify and Protect Against Business Risks--Episode 38 - How to Identify and Protect Against Business Risks--Sam McRoberts, CEO of VUDU Marketing and the author of Screw the Zoo, and Jayson DeMers, CEO of EmailAnalytics, discuss How to Identify and Protect Against Business Risks.With many decades of combined business and digital marketing experience, Jayson and Sam will walk you through everything you need to know as you go through your own entrepreneurial journey.Links to things mentioned in the podcast:Catch Me If You Can - movie about Frank AbagnaleKevin MitnickSamy KamkarPablos HolmanThe Definitive Guide to Wordpress...2020-07-2728 min El Tao del Hacking#43: Quieren llorarContenidos de las secciones de este episodio:Conceptos: Informes de seguridad (II). Casos: Wannacry. Personajes: Samy Kamkar. Recursos: Kali Linux Revealed. 2020-06-0925 min
El Tao del Hacking#43: Quieren llorarContenidos de las secciones de este episodio:Conceptos: Informes de seguridad (II). Casos: Wannacry. Personajes: Samy Kamkar. Recursos: Kali Linux Revealed. 2020-06-0925 min CybercrimeologyThe Things of Internet: Actor Network Theory and CybercrimeAbout the guest:https://www.eur.nl/people/wytske-van-der-wagenPapers mentioned in this episode:Wytske van der Wagen, The Significance of ‘Things’ in Cybercrime: How to Apply Actor-network Theory in (Cyber)criminological Research and Why it Matters, Journal of Extreme Anthropology, Volume 3 Number 1, 2019Assistant Professor at Erasmus University, Department of CriminologyDOI: https://doi.org/10.5617/jea.6895Wytske van der Wagen, Wolter Pieters, From Cybercrime to Cyborg Crime: Botnets as Hybrid Criminal Actor-Networks, The British Journal of Criminology, Volume 55, Issue 3, May 2015, Pages 578–595,https://doi.org/10.1093/bjc/azv009...2020-06-0139 min
CybercrimeologyThe Things of Internet: Actor Network Theory and CybercrimeAbout the guest:https://www.eur.nl/people/wytske-van-der-wagenPapers mentioned in this episode:Wytske van der Wagen, The Significance of ‘Things’ in Cybercrime: How to Apply Actor-network Theory in (Cyber)criminological Research and Why it Matters, Journal of Extreme Anthropology, Volume 3 Number 1, 2019Assistant Professor at Erasmus University, Department of CriminologyDOI: https://doi.org/10.5617/jea.6895Wytske van der Wagen, Wolter Pieters, From Cybercrime to Cyborg Crime: Botnets as Hybrid Criminal Actor-Networks, The British Journal of Criminology, Volume 55, Issue 3, May 2015, Pages 578–595,https://doi.org/10.1093/bjc/azv009...2020-06-0139 min Talking TechExplainer: how those new contact tracing apps will workSamy Kamkar, the chief security officer for Openpath, explains how the new contact tracing apps from Apple and Google will work to combat COVID-19.See Privacy Policy at https://art19.com/privacy and California Privacy Notice at https://art19.com/privacy#do-not-sell-my-info.2020-04-1706 min
Talking TechExplainer: how those new contact tracing apps will workSamy Kamkar, the chief security officer for Openpath, explains how the new contact tracing apps from Apple and Google will work to combat COVID-19.See Privacy Policy at https://art19.com/privacy and California Privacy Notice at https://art19.com/privacy#do-not-sell-my-info.2020-04-1706 min Plus FeedSamySamy Kamkar is a hacker. And while he’s done a lot of stuff, he’s best known for creating the Samy Worm. Which spread its way through a popular social media site and had crazy results.Thanks to our guest Samy Kamkar for telling his story. Learn more about him by visiting https://samy.pl/.SponsorsThis episode was sponsored by IT Pro TV. Get 65 hours of free training by visiting ITPro.tv/darknet. And use promo code DARKNET25.Support for this episode comes from LastPass. LastPass is a great pass...2020-03-171h 01
Plus FeedSamySamy Kamkar is a hacker. And while he’s done a lot of stuff, he’s best known for creating the Samy Worm. Which spread its way through a popular social media site and had crazy results.Thanks to our guest Samy Kamkar for telling his story. Learn more about him by visiting https://samy.pl/.SponsorsThis episode was sponsored by IT Pro TV. Get 65 hours of free training by visiting ITPro.tv/darknet. And use promo code DARKNET25.Support for this episode comes from LastPass. LastPass is a great pass...2020-03-171h 01 Darknet DiariesSamySamy Kamkar is a hacker. And while he’s done a lot of stuff, he’s best known for creating the Samy Worm. Which spread its way through a popular social media site and had crazy results.Thanks to our guest Samy Kamkar for telling his story. Learn more about him by visiting https://samy.pl/.SponsorsThis episode was sponsored by IT Pro TV. Get 65 hours of free training by visiting ITPro.tv/darknet. And use promo code DARKNET25.Support for this episode comes from LastPass. LastPass is a great pass...2020-03-171h 01
Darknet DiariesSamySamy Kamkar is a hacker. And while he’s done a lot of stuff, he’s best known for creating the Samy Worm. Which spread its way through a popular social media site and had crazy results.Thanks to our guest Samy Kamkar for telling his story. Learn more about him by visiting https://samy.pl/.SponsorsThis episode was sponsored by IT Pro TV. Get 65 hours of free training by visiting ITPro.tv/darknet. And use promo code DARKNET25.Support for this episode comes from LastPass. LastPass is a great pass...2020-03-171h 01 Lock and CodeIntroducing Lock and Code, a Malwarebytes podcast on cybersecurityLock and Code is the flagship podcast from the cybersecurity experts at Malwarebytes. Hosted by online privacy advocate and senior threat content writer David Ruiz, Lock and Code not only offers listeners an update on recent cybersecurity news, but it also features in-depth conversations about technology, privacy, cybersecurity, and hacking.
Listen every other week as we talk to a variety of internal and external guests. We've featured Director of Malwarebytes Labs Adam Kujawa, 1Password Chief Operations Optimist Matt Davey, Mozilla Chief Security Officer Marshall Erwin, Open Path co-founder Samy Kamkar, cybersecurity journalists Alfred Ng and Seth Rosenblatt, and far m...2020-02-2102 min
Lock and CodeIntroducing Lock and Code, a Malwarebytes podcast on cybersecurityLock and Code is the flagship podcast from the cybersecurity experts at Malwarebytes. Hosted by online privacy advocate and senior threat content writer David Ruiz, Lock and Code not only offers listeners an update on recent cybersecurity news, but it also features in-depth conversations about technology, privacy, cybersecurity, and hacking.
Listen every other week as we talk to a variety of internal and external guests. We've featured Director of Malwarebytes Labs Adam Kujawa, 1Password Chief Operations Optimist Matt Davey, Mozilla Chief Security Officer Marshall Erwin, Open Path co-founder Samy Kamkar, cybersecurity journalists Alfred Ng and Seth Rosenblatt, and far m...2020-02-2102 min The Story ColliderLove and Technology: Stories about the technology that alters our livesVote for your favorite Story Collider story of all time here: https://airtable.com/shreBxfsM5XYktIT5This week we present stories from people who navigated our changing relationship to technology.Part 1: As a kid, Samy Kamkar discovers his superpower -- hacking.Part 2: When Jordan Bush's father-in-law-to-be is diagnosed with cancer shortly before her wedding, she finds a creative way to help him attend.Samy Kamkar is a cofounder of Openpath, security researcher, and huge nerd. His open source hardware and software highlight the insecurities in everyday technologies, such as w...2020-02-0733 min
The Story ColliderLove and Technology: Stories about the technology that alters our livesVote for your favorite Story Collider story of all time here: https://airtable.com/shreBxfsM5XYktIT5This week we present stories from people who navigated our changing relationship to technology.Part 1: As a kid, Samy Kamkar discovers his superpower -- hacking.Part 2: When Jordan Bush's father-in-law-to-be is diagnosed with cancer shortly before her wedding, she finds a creative way to help him attend.Samy Kamkar is a cofounder of Openpath, security researcher, and huge nerd. His open source hardware and software highlight the insecurities in everyday technologies, such as w...2020-02-0733 min The Story ColliderLove and Technology: Stories about the technology that alters our livesVote for your favorite Story Collider story of all time here: https://airtable.com/shreBxfsM5XYktIT5This week we present stories from people who navigated our changing relationship to technology.Part 1: As a kid, Samy Kamkar discovers his superpower -- hacking.Part 2: When Jordan Bush's father-in-law-to-be is diagnosed with cancer shortly before her wedding, she finds a creative way to help him attend.Samy Kamkar is a cofounder of Openpath, security researcher, and huge nerd. His open source hardware and software highlight the insecurities in everyday technologies, such as w...2020-02-0735 min
The Story ColliderLove and Technology: Stories about the technology that alters our livesVote for your favorite Story Collider story of all time here: https://airtable.com/shreBxfsM5XYktIT5This week we present stories from people who navigated our changing relationship to technology.Part 1: As a kid, Samy Kamkar discovers his superpower -- hacking.Part 2: When Jordan Bush's father-in-law-to-be is diagnosed with cancer shortly before her wedding, she finds a creative way to help him attend.Samy Kamkar is a cofounder of Openpath, security researcher, and huge nerd. His open source hardware and software highlight the insecurities in everyday technologies, such as w...2020-02-0735 min Innovation by Place NorthSamy Kamkar on security in real estateSamy Kamkar, privacy and security researcher and cofounder of Openpath, joined PlaceTech to chat about the security threats in real estate, the time he was arrested by the US secret services and three simple steps companies can take to prevent being hacked. The podcast was hosted by PlaceTech reporter, Nicola Byrne.
This PlaceTech Podcast is sponsored by Essensys.2019-12-1926 min
Innovation by Place NorthSamy Kamkar on security in real estateSamy Kamkar, privacy and security researcher and cofounder of Openpath, joined PlaceTech to chat about the security threats in real estate, the time he was arrested by the US secret services and three simple steps companies can take to prevent being hacked. The podcast was hosted by PlaceTech reporter, Nicola Byrne.
This PlaceTech Podcast is sponsored by Essensys.2019-12-1926 min Getting Into InfosecAdrian Kaylor - From Network Admin to Trainer to Sales Engineer for LifeAdrian is a Sr. Sales Engineer at Splunk who focuses on security. He has worked for various security startups in the Bay Area for the past 15 years from vulnerability management to endpoint investigation to ML-based threat hunting.
Notes:
Had an interest in security early on, starting with opening binaries on Sierra King's quest games and looking for hints.
Took any opportunity he got to get exposed to security
His job as an instructor was very useful during support and later as a sales engineer
Keeps a Trello board for...2019-02-2234 min
Getting Into InfosecAdrian Kaylor - From Network Admin to Trainer to Sales Engineer for LifeAdrian is a Sr. Sales Engineer at Splunk who focuses on security. He has worked for various security startups in the Bay Area for the past 15 years from vulnerability management to endpoint investigation to ML-based threat hunting.
Notes:
Had an interest in security early on, starting with opening binaries on Sierra King's quest games and looking for hints.
Took any opportunity he got to get exposed to security
His job as an instructor was very useful during support and later as a sales engineer
Keeps a Trello board for...2019-02-2234 min Smashing Security092: Hacky sack hack hackIs your used car still connected to its old owner? Just how did Apple manage to identify the teenager hacker who stole 90GB of the firm's files? And why on earth would a firm of lawyers start producing pornographic videos? You'll be surprised by the answers! All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Paul Ducklin. Follow the show on Twitter at @SmashinSecurity, or visit our website for more episodes. Remember: Subscribe on Apple Podcasts, or your favourite...2018-08-2351 min
Smashing Security092: Hacky sack hack hackIs your used car still connected to its old owner? Just how did Apple manage to identify the teenager hacker who stole 90GB of the firm's files? And why on earth would a firm of lawyers start producing pornographic videos? You'll be surprised by the answers! All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Paul Ducklin. Follow the show on Twitter at @SmashinSecurity, or visit our website for more episodes. Remember: Subscribe on Apple Podcasts, or your favourite...2018-08-2351 min Smashing Security092: Hacky sack hack hack
Is your used car still connected to its old owner? Just how did Apple manage to identify the teenager hacker who stole 90GB of the firm's files? And why on earth would a firm of lawyers start producing pornographic videos? You'll be surprised by the answers!
All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Paul Ducklin.
Follow the show on Twitter at @SmashinSecurity, or visit our website for more episodes.
Remember...2018-08-2351 min
Smashing Security092: Hacky sack hack hack
Is your used car still connected to its old owner? Just how did Apple manage to identify the teenager hacker who stole 90GB of the firm's files? And why on earth would a firm of lawyers start producing pornographic videos? You'll be surprised by the answers!
All this and much much more is discussed in the latest edition of the "Smashing Security" podcast by computer security veterans Graham Cluley and Carole Theriault, joined this week by Paul Ducklin.
Follow the show on Twitter at @SmashinSecurity, or visit our website for more episodes.
Remember...2018-08-2351 min Unnamed Reverse Engineering Podcast006 - Marketing Via StickersA quick year end update and feedback show from just the hosts. We cover the Hackaday Superconference where we handed out stickers (track us down to get one of the last few). Key highlights that Alvaro missed first hand were: Michael Ossmann and Dominic Spill on IR RE Samy Kamkar talked about car remote RE See many more talks here Spotify playlist from the conference. We talked briefly about the ask for resources for getting started on the hardware side. If you have suggestions to share, email us! In the meanwhile Mountain view r...2017-12-0617 min
Unnamed Reverse Engineering Podcast006 - Marketing Via StickersA quick year end update and feedback show from just the hosts. We cover the Hackaday Superconference where we handed out stickers (track us down to get one of the last few). Key highlights that Alvaro missed first hand were: Michael Ossmann and Dominic Spill on IR RE Samy Kamkar talked about car remote RE See many more talks here Spotify playlist from the conference. We talked briefly about the ask for resources for getting started on the hardware side. If you have suggestions to share, email us! In the meanwhile Mountain view r...2017-12-0617 min Security Archives - Software Engineering DailyBrave Browser with Jonathan Sampson
Online advertising enables free content and services of the Internet. One of the free services that is powered by advertising is the browser. 60% of web browsing is done through Chrome, which is owned by Google, which is powered by advertising.
The application that most of us use to explore the web is made by a company that relies on ads, so it is unsurprising that the default of that browser is to allow close tracking of user behavior. When you hit a website, a variety of trackers are logging your data for the purpose of...2017-09-2051 min
Security Archives - Software Engineering DailyBrave Browser with Jonathan Sampson
Online advertising enables free content and services of the Internet. One of the free services that is powered by advertising is the browser. 60% of web browsing is done through Chrome, which is owned by Google, which is powered by advertising.
The application that most of us use to explore the web is made by a company that relies on ads, so it is unsurprising that the default of that browser is to allow close tracking of user behavior. When you hit a website, a variety of trackers are logging your data for the purpose of...2017-09-2051 min Security Archives - Software Engineering DailyAttack Attribution with John Davis
When a cyber attack occurs, how do we identify who committed it? There is no straightforward answer to that question.
Even if we know Chinese hackers have infiltrated our power grid with logic bombs, we might not be able to say with certainty whether those hackers were state actors or rogue Chinese hackers looking for an offensive asset to sell to their government.
Even if we know someone in Russia launched an attack on the banking system in Ukraine, we might not know whether that attack came from the government or from aggressive...2017-09-0744 min
Security Archives - Software Engineering DailyAttack Attribution with John Davis
When a cyber attack occurs, how do we identify who committed it? There is no straightforward answer to that question.
Even if we know Chinese hackers have infiltrated our power grid with logic bombs, we might not be able to say with certainty whether those hackers were state actors or rogue Chinese hackers looking for an offensive asset to sell to their government.
Even if we know someone in Russia launched an attack on the banking system in Ukraine, we might not know whether that attack came from the government or from aggressive...2017-09-0744 min Security Archives - Software Engineering DailySecurity Research with Samy Kamkar
Every digital system has vulnerabilities. Cars can be hacked, locked computers can be exploited, and credit cards can be spoofed. Security researchers make a career out of finding these types of vulnerabilities.
Samy Kamkar’s approach to security research is not just about dissection–it’s also about creativity. For many of the technologies he hacks on, Samy open-sources code that summarily describes the vulnerability he has been working on. For example, in his project PoisonTap, Samy open-sourced code that you can run on a $5 Raspberry Pi, and plug into a locked computer to exploit it.2017-01-0458 min
Security Archives - Software Engineering DailySecurity Research with Samy Kamkar
Every digital system has vulnerabilities. Cars can be hacked, locked computers can be exploited, and credit cards can be spoofed. Security researchers make a career out of finding these types of vulnerabilities.
Samy Kamkar’s approach to security research is not just about dissection–it’s also about creativity. For many of the technologies he hacks on, Samy open-sources code that summarily describes the vulnerability he has been working on. For example, in his project PoisonTap, Samy open-sourced code that you can run on a $5 Raspberry Pi, and plug into a locked computer to exploit it.2017-01-0458 min Security Now - 16k MP3SN587: Mobile & IoT NightmaresLeo and I discuss this week's major dynamic duo stories: Samy Kamkar is back with a weaponized $5 Raspberry Pi, and el cheapo Android phones bring new meaning to "phoning it in." Another big unrelated Android problem; watching a webcam getting taken over; Bruce Schneier speaks to Congress about the Internet; another iPhone lock screen bypass and another iPhone lockup link; ransomware author asks a security researcher for help fixing their broken crypto; Britain finally passed that very extreme surveillance law; some more fun miscellany, and more.2016-11-2300 min
Security Now - 16k MP3SN587: Mobile & IoT NightmaresLeo and I discuss this week's major dynamic duo stories: Samy Kamkar is back with a weaponized $5 Raspberry Pi, and el cheapo Android phones bring new meaning to "phoning it in." Another big unrelated Android problem; watching a webcam getting taken over; Bruce Schneier speaks to Congress about the Internet; another iPhone lock screen bypass and another iPhone lockup link; ransomware author asks a security researcher for help fixing their broken crypto; Britain finally passed that very extreme surveillance law; some more fun miscellany, and more.2016-11-2300 min Security Now 2016SN587: Mobile & IoT NightmaresLeo and I discuss this week's major dynamic duo stories: Samy Kamkar is back with a weaponized $5 Raspberry Pi, and el cheapo Android phones bring new meaning to "phoning it in." Another big unrelated Android problem; watching a webcam getting taken over; Bruce Schneier speaks to Congress about the Internet; another iPhone lock screen bypass and another iPhone lockup link; ransomware author asks a security researcher for help fixing their broken crypto; Britain finally passed that very extreme surveillance law; some more fun miscellany, and more.2016-11-2300 min
Security Now 2016SN587: Mobile & IoT NightmaresLeo and I discuss this week's major dynamic duo stories: Samy Kamkar is back with a weaponized $5 Raspberry Pi, and el cheapo Android phones bring new meaning to "phoning it in." Another big unrelated Android problem; watching a webcam getting taken over; Bruce Schneier speaks to Congress about the Internet; another iPhone lock screen bypass and another iPhone lockup link; ransomware author asks a security researcher for help fixing their broken crypto; Britain finally passed that very extreme surveillance law; some more fun miscellany, and more.2016-11-2300 min Liquidmatrix Security Digest PodcastLiquidmatrix Security Digest TV - mini0x1ESamy Kamkar - PoisonTap - https://samy.pl/poisontap/ RCMP want an iphone unlocker - http://www.cbc.ca/news/investigates/police-power-privacy-encryption-1.3856375 Discussion paper - https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/ntnl-scrt-grn-ppr-2016-bckgrndr/index-en.aspx2016-11-1804 min
Liquidmatrix Security Digest PodcastLiquidmatrix Security Digest TV - mini0x1ESamy Kamkar - PoisonTap - https://samy.pl/poisontap/ RCMP want an iphone unlocker - http://www.cbc.ca/news/investigates/police-power-privacy-encryption-1.3856375 Discussion paper - https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/ntnl-scrt-grn-ppr-2016-bckgrndr/index-en.aspx2016-11-1804 min The Amp HourThe Amp Hour #308 - An Interview with Samy Kamkar2016-07-221h 23
The Amp HourThe Amp Hour #308 - An Interview with Samy Kamkar2016-07-221h 23 Friends Without BenefitsSamy KamkarI talk to Samy Kamkar about hacking and stuff. Be a part of the show! Check us out on iTunes! bit.ly/jasonhortonpod Samy Kamkar: http://samy.pl/ Snapchat: thejasonhorton YouTube: bit.ly/subhorton Facebook: www.facebook.com/thejasonhorton Twitter: twitter.com/jason_horton Instagram: instagr.am/thejasonhorton Sideshow Network: www.sideshownetwork.tv Learn more about your ad choices. Visit podcastchoices.com/adchoices2016-04-2744 min
Friends Without BenefitsSamy KamkarI talk to Samy Kamkar about hacking and stuff. Be a part of the show! Check us out on iTunes! bit.ly/jasonhortonpod Samy Kamkar: http://samy.pl/ Snapchat: thejasonhorton YouTube: bit.ly/subhorton Facebook: www.facebook.com/thejasonhorton Twitter: twitter.com/jason_horton Instagram: instagr.am/thejasonhorton Sideshow Network: www.sideshownetwork.tv Learn more about your ad choices. Visit podcastchoices.com/adchoices2016-04-2744 min![DEF CON 23 [Audio] Speeches from the Hacker Convention](http://www.defcon.org/images/defcon-23/dc-23-itunes-logo-Audio.jpg) DEF CON 23 [Audio] Speeches from the Hacker ConventionSamy Kamkar - Drive it like you Hacked it - New Attacks and Tools to Wirelessly Steal CarsMaterials Available here: https://media.defcon.org/DEF%20CON%2023/DEF%20CON%2023%20presentations/DEFCON-23-Samy-Kamkar-README.txt
Extras: https://media.defcon.org/DEF%20CON%2023/DEF%20CON%2023%20presentations/DEFCON-23-Samy-Kamkar-Extras.rar
Drive It Like You Hacked It: New Attacks and Tools to Wirelessly Steal Cars
Samy Kamkar
Gary Numan said it best. Cars. They’re everywhere. You can hardly drive down a busy freeway without seeing one. But what about their security?
In this talk I’ll reveal new research and real attacks in the area of wirelessly controlled gates, garages, and cars. Many...2015-10-1600 min
DEF CON 23 [Audio] Speeches from the Hacker ConventionSamy Kamkar - Drive it like you Hacked it - New Attacks and Tools to Wirelessly Steal CarsMaterials Available here: https://media.defcon.org/DEF%20CON%2023/DEF%20CON%2023%20presentations/DEFCON-23-Samy-Kamkar-README.txt
Extras: https://media.defcon.org/DEF%20CON%2023/DEF%20CON%2023%20presentations/DEFCON-23-Samy-Kamkar-Extras.rar
Drive It Like You Hacked It: New Attacks and Tools to Wirelessly Steal Cars
Samy Kamkar
Gary Numan said it best. Cars. They’re everywhere. You can hardly drive down a busy freeway without seeing one. But what about their security?
In this talk I’ll reveal new research and real attacks in the area of wirelessly controlled gates, garages, and cars. Many...2015-10-1600 min Geeks & BeatsThe Merch AwakensHands-on: the Star Wars drone, even if it is the fastest hunk of junk in the galaxy, you shouldn’t buy it. Stealing cars the high tech way: We’ll introduce you to Samy Kamkar who not only broke Myspace, but the hearts of auto industry technicians worldwide. Get your pencils ready — The cassette is back. We’ll tell you why the only major manufacturer is seeing sales rise. Plus — Technics is getting back into the turntable business. Just bring your own toner arm and copy of Dark Side of the Moon. And attention travelers: we’re giving away a gadget tha...2015-09-0941 min
Geeks & BeatsThe Merch AwakensHands-on: the Star Wars drone, even if it is the fastest hunk of junk in the galaxy, you shouldn’t buy it. Stealing cars the high tech way: We’ll introduce you to Samy Kamkar who not only broke Myspace, but the hearts of auto industry technicians worldwide. Get your pencils ready — The cassette is back. We’ll tell you why the only major manufacturer is seeing sales rise. Plus — Technics is getting back into the turntable business. Just bring your own toner arm and copy of Dark Side of the Moon. And attention travelers: we’re giving away a gadget tha...2015-09-0941 min The Tim Ferriss Show#74: How a Computer Hacker Optimizes Online Dating, Opens Locked Cars, and Hijacks DronesSamy Kamkar is one of the most innovative and notorious computer hackers in the United States. He’s also a well-known whistleblower. If you want how Samy hacks everything from online dating to car alarms, this episode is for you. He is best known for creating the fastest spreading virus of all time, a MySpace worm named “Samy.” He got raided by the United States Secret Service for that one. More recently, he’s created SkyJack, a custom drone that hacks into any nearby drones, allowing him (or any operator) to control a swarm of devices; and Evercookie, which appeared in top-se...2015-05-022h 40
The Tim Ferriss Show#74: How a Computer Hacker Optimizes Online Dating, Opens Locked Cars, and Hijacks DronesSamy Kamkar is one of the most innovative and notorious computer hackers in the United States. He’s also a well-known whistleblower. If you want how Samy hacks everything from online dating to car alarms, this episode is for you. He is best known for creating the fastest spreading virus of all time, a MySpace worm named “Samy.” He got raided by the United States Secret Service for that one. More recently, he’s created SkyJack, a custom drone that hacks into any nearby drones, allowing him (or any operator) to control a swarm of devices; and Evercookie, which appeared in top-se...2015-05-022h 40 UAV News Talk – Drone News, eVTOLs, UAS Policy & Air MobilityUAS for Good, Bad, and the ImprobableThis Episode:Using a drone to smuggle contraband into a prison, learn to fly unmanned vehicles at a University, UAV privacy laws carve out drones as a special case, drones are blocked even for humanitarian purposes, the Amazon.com vision for UAS, and how to hack a drone.The News:Drones used to try to smuggle contraband into jailPrison guards, probably among the most perceptive people, noticed a hexacopter over Calhoun State Prison in Georgia. Four people were arrested after the drone was found in a car with some tobacco...2013-12-0730 min
UAV News Talk – Drone News, eVTOLs, UAS Policy & Air MobilityUAS for Good, Bad, and the ImprobableThis Episode:Using a drone to smuggle contraband into a prison, learn to fly unmanned vehicles at a University, UAV privacy laws carve out drones as a special case, drones are blocked even for humanitarian purposes, the Amazon.com vision for UAS, and how to hack a drone.The News:Drones used to try to smuggle contraband into jailPrison guards, probably among the most perceptive people, noticed a hexacopter over Calhoun State Prison in Georgia. Four people were arrested after the drone was found in a car with some tobacco...2013-12-0730 min Security Now 2010SN270: The EvercookieAfter reviewing the past week's security updates and news, Steve and Leo examine Samy Kamkar's (http://samy.pl/evercookie/) clever suite of Javascript Hacks, collectively used to create an "Evercookie" for tagging web browsers in a fashion that's extremely difficult to shake off.2010-10-1500 min
Security Now 2010SN270: The EvercookieAfter reviewing the past week's security updates and news, Steve and Leo examine Samy Kamkar's (http://samy.pl/evercookie/) clever suite of Javascript Hacks, collectively used to create an "Evercookie" for tagging web browsers in a fashion that's extremely difficult to shake off.2010-10-1500 min Security Now - 16k MP3SN270: The EvercookieAfter reviewing the past week's security updates and news, Steve and Leo examine Samy Kamkar's (http://samy.pl/evercookie/) clever suite of Javascript Hacks, collectively used to create an "Evercookie" for tagging web browsers in a fashion that's extremely difficult to shake off.2010-10-1500 min
Security Now - 16k MP3SN270: The EvercookieAfter reviewing the past week's security updates and news, Steve and Leo examine Samy Kamkar's (http://samy.pl/evercookie/) clever suite of Javascript Hacks, collectively used to create an "Evercookie" for tagging web browsers in a fashion that's extremely difficult to shake off.2010-10-1500 min![DEF CON 18 [Video] Speeches from the Hacker Convention.](http://www.defcon.org/podcast/dc-18-itunes-logo-video.jpg) DEF CON 18 [Video] Speeches from the Hacker Convention.Samy Kamkar - How I Met Your GirlfriendHow I Met Your Girlfriend: The discovery and execution of entirely new classes of Web attacks in order to meet your girlfriend.This includes newly discovered attacks including HTML5 client-side XSS (without XSS hitting the server!), PHP session hijacking and random numbers (accurately guessing PHP session cookies), browser protocol confusion (turning a browser into an SMTP server), firewall and NAT penetration via Javascript (turning your router against you), remote iPhone Google Maps hijacking (iPhone penetration combined with HTTP man-in-the-middle), extracting extremely accurate geolocation information from a Web browser (not using IP geolocation), and more.Samy Kamkar...2010-10-0837 min
DEF CON 18 [Video] Speeches from the Hacker Convention.Samy Kamkar - How I Met Your GirlfriendHow I Met Your Girlfriend: The discovery and execution of entirely new classes of Web attacks in order to meet your girlfriend.This includes newly discovered attacks including HTML5 client-side XSS (without XSS hitting the server!), PHP session hijacking and random numbers (accurately guessing PHP session cookies), browser protocol confusion (turning a browser into an SMTP server), firewall and NAT penetration via Javascript (turning your router against you), remote iPhone Google Maps hijacking (iPhone penetration combined with HTTP man-in-the-middle), extracting extremely accurate geolocation information from a Web browser (not using IP geolocation), and more.Samy Kamkar...2010-10-0837 min KUCI: Tech TalkSamy Kamkar and Ravind KumarSamy Kamkar is the creator of the MySpace Worm. The MySpace Worm infected over 1 million profiles on the site. Listen to Samy's suspenseful story in his own words! Then Ravind discusses the story of the iPhone prototype that was lost and examined by the tech blog Gizmodo.com.2010-05-1700 min
KUCI: Tech TalkSamy Kamkar and Ravind KumarSamy Kamkar is the creator of the MySpace Worm. The MySpace Worm infected over 1 million profiles on the site. Listen to Samy's suspenseful story in his own words! Then Ravind discusses the story of the iPhone prototype that was lost and examined by the tech blog Gizmodo.com.2010-05-1700 min