Shows
 AWS for Software Companies PodcastEp122: Securing the Software Supply Chain - How Sonatype Protects Developers in the Age of AIChief Product Development Officer Mitchell Johnson discusses how Sonatype protects enterprise developers from malicious open source components while keeping them productive through AI.Topics Include:Sonatype provides software supply chain solutions for enterprises using open source componentsThey serve large enterprises, government agencies, and critical infrastructure providers globallyMain challenge: keeping developers productive while maintaining secure software supply chainsCybercrime and supply chain attacks are massive, growing industries threatening developersAI adoption is happening faster than expected, profoundly changing development workflowsBad actors evolved from waiting for vulnerabilities to creating malicious componentsMalicious open source components specifically target developer and DevOps toolchainsSonatype's...2025-07-2319 min
AWS for Software Companies PodcastEp122: Securing the Software Supply Chain - How Sonatype Protects Developers in the Age of AIChief Product Development Officer Mitchell Johnson discusses how Sonatype protects enterprise developers from malicious open source components while keeping them productive through AI.Topics Include:Sonatype provides software supply chain solutions for enterprises using open source componentsThey serve large enterprises, government agencies, and critical infrastructure providers globallyMain challenge: keeping developers productive while maintaining secure software supply chainsCybercrime and supply chain attacks are massive, growing industries threatening developersAI adoption is happening faster than expected, profoundly changing development workflowsBad actors evolved from waiting for vulnerabilities to creating malicious componentsMalicious open source components specifically target developer and DevOps toolchainsSonatype's...2025-07-2319 min Security Weekly Podcast Network (Audio)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Shahar Man, Brian Fox, Mark Lambert - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04
Security Weekly Podcast Network (Audio)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Shahar Man, Brian Fox, Mark Lambert - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04 Security Weekly (Download Only)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Brian Fox, Mark Lambert, Shahar Man - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. As 'vibe coding", the practice of using AI tools with specialized coding LLMs to develop software, is ma...2025-05-271h 04
Security Weekly (Download Only)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Brian Fox, Mark Lambert, Shahar Man - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. As 'vibe coding", the practice of using AI tools with specialized coding LLMs to develop software, is ma...2025-05-271h 04 Application Security Weekly (Audio)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Shahar Man, Brian Fox, Mark Lambert - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04
Application Security Weekly (Audio)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Shahar Man, Brian Fox, Mark Lambert - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04 Application Security Weekly (Video)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Brian Fox, Mark Lambert, Shahar Man - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04
Application Security Weekly (Video)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Brian Fox, Mark Lambert, Shahar Man - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04 Application Security Weekly (Video)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Brian Fox, Mark Lambert, Shahar Man - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04
Application Security Weekly (Video)AI in AppSec: Agentic Tools, Vibe Coding Risks & Securing Non-Human Identities - Mo Aboul-Magd, Brian Fox, Mark Lambert, Shahar Man - ASW #332ArmorCode unveils Anya—the first agentic AI virtual security champion designed specifically for AppSec and product security teams. Anya brings together conversation and context to help AppSec, developers and security teams cut through the noise, prioritize risks, and make faster, smarter decisions across code, cloud, and infrastructure. Built into the ArmorCode ASPM Platform and backed by 25B findings, 285+ integrations, natural language intelligence, and role-aware insights, Anya turns complexity into clarity, helping teams scale securely and close the security skills gap. Anya is now generally available and included as part of the ArmorCode ASPM Platform. Visit https://securityweekly.co...2025-05-271h 04 FINOS Open Source in Finance PodcastThe Unexpected Risks of AI in Finance: Expert Panel Discussion - Nvidia & SonatypeIn this episode of the FINOS Open Source in Finance webinar series, Karl Moll hosts an engaging panel discussion with Tyler Warden from Sonatype and Aaron Erickson from Nvidia. The topic is 'The Unexpected Risks of AI in Finance,' covering hidden and novel security risks in AI-driven financial systems, the importance of hardware in AI security, and regulatory approaches to AI compliance. The panelists delve into common misconceptions, real-world examples of AI risks, software supply chain issues, and actionable advice for securing AI pipelines. They also discuss the fundamental role of human accountability and the importance of collaboration...2025-05-1254 min
FINOS Open Source in Finance PodcastThe Unexpected Risks of AI in Finance: Expert Panel Discussion - Nvidia & SonatypeIn this episode of the FINOS Open Source in Finance webinar series, Karl Moll hosts an engaging panel discussion with Tyler Warden from Sonatype and Aaron Erickson from Nvidia. The topic is 'The Unexpected Risks of AI in Finance,' covering hidden and novel security risks in AI-driven financial systems, the importance of hardware in AI security, and regulatory approaches to AI compliance. The panelists delve into common misconceptions, real-world examples of AI risks, software supply chain issues, and actionable advice for securing AI pipelines. They also discuss the fundamental role of human accountability and the importance of collaboration...2025-05-1254 min What the Dev?290: The state of software supply chain security (with Sonatype's Brian Fox)In this episode, David Rubinstein interviews Brian Fox, co-founder and CTO of Sonatype. They discuss the company's 10th annual State of the Software Supply Chain report. Key talking points include: The rapid growth of malicious open-source componentsThe increasing length of time needed to remediate vulnerabilitiesHow regulations impact supply chain securityNote: This will be the final episode of What The Dev released in 2024. We'll be back in early January 2025! 2024-12-1714 min
What the Dev?290: The state of software supply chain security (with Sonatype's Brian Fox)In this episode, David Rubinstein interviews Brian Fox, co-founder and CTO of Sonatype. They discuss the company's 10th annual State of the Software Supply Chain report. Key talking points include: The rapid growth of malicious open-source componentsThe increasing length of time needed to remediate vulnerabilitiesHow regulations impact supply chain securityNote: This will be the final episode of What The Dev released in 2024. We'll be back in early January 2025! 2024-12-1714 min Open Source SecurityEpisode 454 - The state of open source with Brian Fox from Sonatype and Donald Fischer from TideliftJosh and Kurt talk to Brian Fox from Sonatype and Donald Fischer from Tidelift about their recent reports as well as open source. There are really interesting connections between the two reports. The overall theme seems to be open source is huge, everywhere, and needs help. But all is no lost! There's some great ideas on what the future needs to look like. Show Notes Donald Fischer Brian Fox Tidelift Sonatype The 2024 Tidelift state of the open source maintainer report Sonatype State of the Software Supply Chain Anchore 2024 Software Supply Chain Security Report OpenSSF TAC issue 101 2024-11-1143 min
Open Source SecurityEpisode 454 - The state of open source with Brian Fox from Sonatype and Donald Fischer from TideliftJosh and Kurt talk to Brian Fox from Sonatype and Donald Fischer from Tidelift about their recent reports as well as open source. There are really interesting connections between the two reports. The overall theme seems to be open source is huge, everywhere, and needs help. But all is no lost! There's some great ideas on what the future needs to look like. Show Notes Donald Fischer Brian Fox Tidelift Sonatype The 2024 Tidelift state of the open source maintainer report Sonatype State of the Software Supply Chain Anchore 2024 Software Supply Chain Security Report OpenSSF TAC issue 101 2024-11-1143 min DayOne.FMOpen-Source Software: Balancing Innovation and Security with Ilkka Turunen, CTO of SonatypeEpisode SummaryIlkka Turunen is the CTO at Sonatype, a company that helps millions of software developers use open-source software while minimising security risk. In this conversation, Ilkka chats with Cole Cornford about the benefits and risk of using open-source software, how Maven helped standardise software development processes, the different approaches to AppSec regulation in Australia and Europe, and plenty more.Timestamps1:33 - Ilkka's career background4:00 - Varying quality of open-source software6:10 - How Maven helped standardise software development processes13:00 - The balance between speed of delivery...2024-10-0946 min
DayOne.FMOpen-Source Software: Balancing Innovation and Security with Ilkka Turunen, CTO of SonatypeEpisode SummaryIlkka Turunen is the CTO at Sonatype, a company that helps millions of software developers use open-source software while minimising security risk. In this conversation, Ilkka chats with Cole Cornford about the benefits and risk of using open-source software, how Maven helped standardise software development processes, the different approaches to AppSec regulation in Australia and Europe, and plenty more.Timestamps1:33 - Ilkka's career background4:00 - Varying quality of open-source software6:10 - How Maven helped standardise software development processes13:00 - The balance between speed of delivery...2024-10-0946 min Secured by Galah Cyber with Cole CornfordOpen-Source Software: Balancing Innovation and Security with Ilkka Turunen, CTO of SonatypeEpisode SummaryIlkka Turunen is the CTO at Sonatype, a company that helps millions of software developers use open-source software while minimising security risk. In this conversation, Ilkka chats with Cole Cornford about the benefits and risk of using open-source software, how Maven helped standardise software development processes, the different approaches to AppSec regulation in Australia and Europe, and plenty more.Timestamps1:33 - Ilkka's career background4:00 - Varying quality of open-source software6:10 - How Maven helped standardise software development processes13:00 - The balance between speed of delivery...2024-10-0946 min
Secured by Galah Cyber with Cole CornfordOpen-Source Software: Balancing Innovation and Security with Ilkka Turunen, CTO of SonatypeEpisode SummaryIlkka Turunen is the CTO at Sonatype, a company that helps millions of software developers use open-source software while minimising security risk. In this conversation, Ilkka chats with Cole Cornford about the benefits and risk of using open-source software, how Maven helped standardise software development processes, the different approaches to AppSec regulation in Australia and Europe, and plenty more.Timestamps1:33 - Ilkka's career background4:00 - Varying quality of open-source software6:10 - How Maven helped standardise software development processes13:00 - The balance between speed of delivery...2024-10-0946 min What's in the SOSS? An OpenSSF PodcastSonatype’s Brian Fox and the Perplexing Phenomenon of Downloading Known VulnerabilitiesBrian Fox is Co-founder and Chief Technology Officer at Sonatype, bringing over 28 years of hands-on experience driving software development for organizations of all sizes, from startups to large enterprises. A recognized figure in the Apache Maven ecosystem and a longstanding member of the Apache Software Foundation, Brian has played a crucial role in creating popular plugins like the maven-dependency-plugin and maven-enforcer-plugin. His leadership includes overseeing Maven Central, the world's largest repository of open-source Java components, which recently surpassed a trillion downloads annually.As a Governing Board member for the Open Source Security Foundation, Brian actively c...2024-07-1622 min
What's in the SOSS? An OpenSSF PodcastSonatype’s Brian Fox and the Perplexing Phenomenon of Downloading Known VulnerabilitiesBrian Fox is Co-founder and Chief Technology Officer at Sonatype, bringing over 28 years of hands-on experience driving software development for organizations of all sizes, from startups to large enterprises. A recognized figure in the Apache Maven ecosystem and a longstanding member of the Apache Software Foundation, Brian has played a crucial role in creating popular plugins like the maven-dependency-plugin and maven-enforcer-plugin. His leadership includes overseeing Maven Central, the world's largest repository of open-source Java components, which recently surpassed a trillion downloads annually.As a Governing Board member for the Open Source Security Foundation, Brian actively c...2024-07-1622 min FINOS Open Source in Finance PodcastFINOS May 24 2024 Debrief - with Eddie Knight, SonatypeIn this episode of the podcast, Grizz and Eddie Knight of Sonatype return to our FINOS Debrief episodes that wrap up the past month or so in the FINOS Ecosystem - and look forward to the next month and beyond.
Save 20% off OSFF with this code: OSFFL24LF20
Register Here & Attend the London Open Source in Finance Forum 26 June 2024: https://events.linuxfoundation.org/open-source-finance-forum-london/
2023 State of Open Source in Financial Services Download: https://www.finos.org/state-of-open-source-in-financial-services-2023
FINOS Current Newsletter Here: https://www.finos.org/newsletter - more show notes to com...2024-05-261h 02
FINOS Open Source in Finance PodcastFINOS May 24 2024 Debrief - with Eddie Knight, SonatypeIn this episode of the podcast, Grizz and Eddie Knight of Sonatype return to our FINOS Debrief episodes that wrap up the past month or so in the FINOS Ecosystem - and look forward to the next month and beyond.
Save 20% off OSFF with this code: OSFFL24LF20
Register Here & Attend the London Open Source in Finance Forum 26 June 2024: https://events.linuxfoundation.org/open-source-finance-forum-london/
2023 State of Open Source in Financial Services Download: https://www.finos.org/state-of-open-source-in-financial-services-2023
FINOS Current Newsletter Here: https://www.finos.org/newsletter - more show notes to com...2024-05-261h 02 Foojay.io, the Friends Of OpenJDK!JCON Report, Part 2 (#50) - Maven, Software Security, Code QualityThis is part 2 of the interviews we recorded at the JCON conference earlier this month in Germany. In this episode you get two main topics: Maven and Code Quality. In the first part, you'll hear Karl Heinz Marbaise and Steve Pool about the Maven project, the repository, Sonaytype and the security impact of dependencies. But next to security, we as developers are also responsible for the creation of readable and maintainable code. Miro Wengner, Marit van Dijk, and Hinse ter Schuur dive into this topic.00:28 Karl Heinz Marbaise: Apache Maven version 4, Sonatype, Maven Repositoryhttps://www...2024-05-2552 min
Foojay.io, the Friends Of OpenJDK!JCON Report, Part 2 (#50) - Maven, Software Security, Code QualityThis is part 2 of the interviews we recorded at the JCON conference earlier this month in Germany. In this episode you get two main topics: Maven and Code Quality. In the first part, you'll hear Karl Heinz Marbaise and Steve Pool about the Maven project, the repository, Sonaytype and the security impact of dependencies. But next to security, we as developers are also responsible for the creation of readable and maintainable code. Miro Wengner, Marit van Dijk, and Hinse ter Schuur dive into this topic.00:28 Karl Heinz Marbaise: Apache Maven version 4, Sonatype, Maven Repositoryhttps://www...2024-05-2552 min The Business of Open SourceTrying All the Open Source Business Models with Brian FoxThis week on The Business of Open Source, I spoke with Brian Fox, co-founder and CTO of Sonatype. In addition to having a really interesting discussion about the usual topic of how to build a business around open source software, we also had a good conversation about security — it was hard to avoid, because we recorded this right after the xz backdoor discovery, and software supply chain security is kind of Brian’s thing. Business-wise, though, we also covered some really cool topics. Including: The tension between an open source projec...2024-05-0145 min
The Business of Open SourceTrying All the Open Source Business Models with Brian FoxThis week on The Business of Open Source, I spoke with Brian Fox, co-founder and CTO of Sonatype. In addition to having a really interesting discussion about the usual topic of how to build a business around open source software, we also had a good conversation about security — it was hard to avoid, because we recorded this right after the xz backdoor discovery, and software supply chain security is kind of Brian’s thing. Business-wise, though, we also covered some really cool topics. Including: The tension between an open source projec...2024-05-0145 min Side Project Spotlight#56: Diving Into DependenciesIn this final episode of 2023, the trio dive into the topic of dependencies! What kinds are there? How do you manage them? What are some examples? This episode is jam packed with great advice and a ton of useful links (see below!) to help you think about the tradeoffs of different kinds of dependencies as well as concrete advice on how to write cleaner code that your future self will appreciate. Have a great holiday season and a happy new year as you embark on your own developer journey into 2024! The trio will return in January!
2023-12-041h 05
Side Project Spotlight#56: Diving Into DependenciesIn this final episode of 2023, the trio dive into the topic of dependencies! What kinds are there? How do you manage them? What are some examples? This episode is jam packed with great advice and a ton of useful links (see below!) to help you think about the tradeoffs of different kinds of dependencies as well as concrete advice on how to write cleaner code that your future self will appreciate. Have a great holiday season and a happy new year as you embark on your own developer journey into 2024! The trio will return in January!
2023-12-041h 05 Open Source SecurityIs only 11% of open source maintained?Josh and Kurt talk about Sonatype's 9th Annual State of the Software Supply Chain. There's a ton of data in the report, but the thing we want to talk about is the statistic that only 11% of open source is actually being maintained. Do we think that's true? Does it really matter? Show Notes Sonatype report ecosyste.ms GNOME libcue flaw Reality 2.0 supply chain episode 2023-10-2336 min
Open Source SecurityIs only 11% of open source maintained?Josh and Kurt talk about Sonatype's 9th Annual State of the Software Supply Chain. There's a ton of data in the report, but the thing we want to talk about is the statistic that only 11% of open source is actually being maintained. Do we think that's true? Does it really matter? Show Notes Sonatype report ecosyste.ms GNOME libcue flaw Reality 2.0 supply chain episode 2023-10-2336 min It's 5:05! Daily cybersecurity and open source briefingEpisode #245: npm Typo-Squat Deploys RootKits; Software Supply Chain: What Matters to an Architect; Security During Software Creation; OpenSSF Scorecards for Open Source🎙️ Free, ungated access to all 235+ episodes of “It’s 5:05!” on your favorite podcast platforms: https://bit.ly/505-updates. ♻️ You’re welcome to 𝗿𝗲𝗽𝗼𝘀𝘁 if your followers will find this of value.The stories we're covering today.Marcel Brown: October 6th, 1942. Chester Carlson is issued a patent on a process called electrophotography, now commonly known as photocopying. It was not until 1946 that a company had any interest in pursuing photocopying commercially.Edwin Kwan: A malicious component in the npm package registry has been found to be deploying an open-source rootkit. This incident is a reminder that developers need to take caution...2023-10-0614 min
It's 5:05! Daily cybersecurity and open source briefingEpisode #245: npm Typo-Squat Deploys RootKits; Software Supply Chain: What Matters to an Architect; Security During Software Creation; OpenSSF Scorecards for Open Source🎙️ Free, ungated access to all 235+ episodes of “It’s 5:05!” on your favorite podcast platforms: https://bit.ly/505-updates. ♻️ You’re welcome to 𝗿𝗲𝗽𝗼𝘀𝘁 if your followers will find this of value.The stories we're covering today.Marcel Brown: October 6th, 1942. Chester Carlson is issued a patent on a process called electrophotography, now commonly known as photocopying. It was not until 1946 that a company had any interest in pursuing photocopying commercially.Edwin Kwan: A malicious component in the npm package registry has been found to be deploying an open-source rootkit. This incident is a reminder that developers need to take caution...2023-10-0614 min Люди и кодDevSecOps: как защитить цепочки поставок ПО и создать безопасный софтСодержание выпуска
— Что такое DevOps, как и зачем придумали эту методологию, какие инструменты в ней задействованы.
— Цепочки поставок программного обеспечения: что это такое и из чего они состоят.
— Баги, уязвимости, бэкдоры и другие угрозы, которые несёт Open Source.
— Яркие примеры атак на цепочки поставок ПО.
— Что такое DevSecOps и какие проблемы «обычного» DevOps он решает. Понятие Shift left.
— Как выглядит работа DevSecOps-специалистов.
— Что такое software composition analysis и как он осуществляется.
— Как самостоятельно проверить безопасность пайплайнов: базовые принципы, SAST, Trivy и другие инструменты.
— Что почитать про DevSecOps. Фреймворки и концепции, которые полезно знать специалисту.
— Метрики и бенчмарки в DevSecOps.
Гость. Антон Башарин. Технический директор Swordfish Security, сооснователь платформы AppSec.Hub, архитектор продукта и ведущий эксперт по его развитию.
Общий опыт работы в IT — более 20 лет. Прошёл суровую школу от рядового разработчика до системного архитектора и руководителя команды разработки в Luxoft и EPAM Systems, участвовал в проектах для Boeing, Сбербанка и «Альфа-банка».Полезные ссылки
— Статья про бэкдор в event-stream https://habr.com/ru/articles/431360/— отчет Group IB о Redcurl https://www.facct.ru/resources/research-hub/red-curl/— блог Swordfish Security на Хабре https://habr.com/ru/companies/swordfish_security/articles/— YouTube-канал Swordfish Security https://www.youtube.com/@swordfishsecurity— Марк Миллер, «Epic Failures in DevSecOps: Volume 1» https://www.sonatype.com/thanks/white-paper-epic-failures-vol-1— Марк Миллер, «Epic Failures, Volume 2: Compliments of Sonatype» https://www.sonatype.com/thanks/white-paper-epic-failures-vol-2Предложить тему, стать гостем подкаста, похвалить или поругать выпуск: code.media@skillbox.ru, t.me/antoxa_s95
Стартовать в программировании вместе со Skillbox: skillbox.ru/code
Подписывайтесь, ставьте лайки, делитесь с друзьями и оставляйте комментарии!
2023-09-0750 min
Люди и кодDevSecOps: как защитить цепочки поставок ПО и создать безопасный софтСодержание выпуска
— Что такое DevOps, как и зачем придумали эту методологию, какие инструменты в ней задействованы.
— Цепочки поставок программного обеспечения: что это такое и из чего они состоят.
— Баги, уязвимости, бэкдоры и другие угрозы, которые несёт Open Source.
— Яркие примеры атак на цепочки поставок ПО.
— Что такое DevSecOps и какие проблемы «обычного» DevOps он решает. Понятие Shift left.
— Как выглядит работа DevSecOps-специалистов.
— Что такое software composition analysis и как он осуществляется.
— Как самостоятельно проверить безопасность пайплайнов: базовые принципы, SAST, Trivy и другие инструменты.
— Что почитать про DevSecOps. Фреймворки и концепции, которые полезно знать специалисту.
— Метрики и бенчмарки в DevSecOps.
Гость. Антон Башарин. Технический директор Swordfish Security, сооснователь платформы AppSec.Hub, архитектор продукта и ведущий эксперт по его развитию.
Общий опыт работы в IT — более 20 лет. Прошёл суровую школу от рядового разработчика до системного архитектора и руководителя команды разработки в Luxoft и EPAM Systems, участвовал в проектах для Boeing, Сбербанка и «Альфа-банка».Полезные ссылки
— Статья про бэкдор в event-stream https://habr.com/ru/articles/431360/— отчет Group IB о Redcurl https://www.facct.ru/resources/research-hub/red-curl/— блог Swordfish Security на Хабре https://habr.com/ru/companies/swordfish_security/articles/— YouTube-канал Swordfish Security https://www.youtube.com/@swordfishsecurity— Марк Миллер, «Epic Failures in DevSecOps: Volume 1» https://www.sonatype.com/thanks/white-paper-epic-failures-vol-1— Марк Миллер, «Epic Failures, Volume 2: Compliments of Sonatype» https://www.sonatype.com/thanks/white-paper-epic-failures-vol-2Предложить тему, стать гостем подкаста, похвалить или поругать выпуск: code.media@skillbox.ru, t.me/antoxa_s95
Стартовать в программировании вместе со Skillbox: skillbox.ru/code
Подписывайтесь, ставьте лайки, делитесь с друзьями и оставляйте комментарии!
2023-09-0750 min Techstrong 55Episode #123 - Techstrong 55, Wednesday, August 9, 2023Hello everyone and welcome to Techstrong 55. Today is Wednesday, August 9th, and I am your host William Willis. In today’s show, we will hear about the cost of breaches with John Dwyer from IBM. Then, we will hear about AI-powered DevSecOps for the enterprise with Derek Holt from Digital.ai. Finally, we will hear about the Cyber Resilience Act with Brian Fox from Sonatype.
Without further ado, let's get the show started. Enjoy.
In this Episode:
Cost of Breaches - John Dwyer, IBM
AI-Powered DevSe...2023-08-0958 min
Techstrong 55Episode #123 - Techstrong 55, Wednesday, August 9, 2023Hello everyone and welcome to Techstrong 55. Today is Wednesday, August 9th, and I am your host William Willis. In today’s show, we will hear about the cost of breaches with John Dwyer from IBM. Then, we will hear about AI-powered DevSecOps for the enterprise with Derek Holt from Digital.ai. Finally, we will hear about the Cyber Resilience Act with Brian Fox from Sonatype.
Without further ado, let's get the show started. Enjoy.
In this Episode:
Cost of Breaches - John Dwyer, IBM
AI-Powered DevSe...2023-08-0958 min Millennium Live | A Leadership & Discovery PodcastEpisode 208 | Develop Software FearlesslySoftware development is evolving. 90% of modern applications use open source code for good reason—speed. But when open source components go unmaintained, they become liabilities that leave organizations open to security and licensing risks. Millennium Live welcomed Brian Fox, CO-Founder and CTO of Sonatype to discuss how they are helping customers get a better handle on software supply chain security. Sonatype's Software Supply Chain Report shows an average 742% increase in software supply chain attacks each year since 2019, it's now thr time for leaders to emphasize the continued importance of and investment in cybersecurity organizations prepare to mitigate liability Brian al...2023-06-1520 min
Millennium Live | A Leadership & Discovery PodcastEpisode 208 | Develop Software FearlesslySoftware development is evolving. 90% of modern applications use open source code for good reason—speed. But when open source components go unmaintained, they become liabilities that leave organizations open to security and licensing risks. Millennium Live welcomed Brian Fox, CO-Founder and CTO of Sonatype to discuss how they are helping customers get a better handle on software supply chain security. Sonatype's Software Supply Chain Report shows an average 742% increase in software supply chain attacks each year since 2019, it's now thr time for leaders to emphasize the continued importance of and investment in cybersecurity organizations prepare to mitigate liability Brian al...2023-06-1520 min FOCUS ON: DevOpsRed Hat Summit Special - OpenShift Security
Die Anforderungen an Sicherheit werden stetig größer. Zugegeben, die Cloud-Native-Welt bietet uns Möglichkeiten, Applikationen mittels Open Source "On Scale" zu entwickeln und zu betreiben. Doch leider birgt dies das Risiko, dass Schadcode im gleichen Maße verbreitet wird.
Bei Red Hat ist dieser Aufwand gar nicht nötig. Denn OpenShift bietet Security by Default. Was genau darunter zu verstehen ist, wollten wir von den Red Hat-Kollegen ganz genau wissen. Enrico spricht in dieser Folge mit Sebastian Zoll, Sebb Dehn und Steffen Lützenkirchen über die Relevanz und Etablierung von Security in der Container-Plattform sowie über klassisc...2023-06-0749 min
FOCUS ON: DevOpsRed Hat Summit Special - OpenShift Security
Die Anforderungen an Sicherheit werden stetig größer. Zugegeben, die Cloud-Native-Welt bietet uns Möglichkeiten, Applikationen mittels Open Source "On Scale" zu entwickeln und zu betreiben. Doch leider birgt dies das Risiko, dass Schadcode im gleichen Maße verbreitet wird.
Bei Red Hat ist dieser Aufwand gar nicht nötig. Denn OpenShift bietet Security by Default. Was genau darunter zu verstehen ist, wollten wir von den Red Hat-Kollegen ganz genau wissen. Enrico spricht in dieser Folge mit Sebastian Zoll, Sebb Dehn und Steffen Lützenkirchen über die Relevanz und Etablierung von Security in der Container-Plattform sowie über klassisc...2023-06-0749 min Side Project Spotlight#41: Package Oriented ProgrammingThis week, the trio celebrates their podcast mid-life crisis by discussing a concept coined by Daniel Steinberg in a 2022 talk, "Packaged Oriented Programming." How do you organize your app using Swift Package Manager packages? What are the benefits and costs? There is also some discussion on dealing with JSON API changes, using Codable vs DTOs, and strategies for caching external package dependencies for the longterm. Be sure to stay until the end where Kotaro engages in some live "prompt engineering" with Chat GPT that generates some impressively bad jokes.
## Topics Discussed
...2023-05-081h 00
Side Project Spotlight#41: Package Oriented ProgrammingThis week, the trio celebrates their podcast mid-life crisis by discussing a concept coined by Daniel Steinberg in a 2022 talk, "Packaged Oriented Programming." How do you organize your app using Swift Package Manager packages? What are the benefits and costs? There is also some discussion on dealing with JSON API changes, using Codable vs DTOs, and strategies for caching external package dependencies for the longterm. Be sure to stay until the end where Kotaro engages in some live "prompt engineering" with Chat GPT that generates some impressively bad jokes.
## Topics Discussed
...2023-05-081h 00 Wicked Good DevelopmentEpisode 32: Java Queens at Devnexus 2023Prepare for an insightful discussion with Java Champions Erin Schnable, Emily Jiang, Mary Gygleski, and Holly Cummins at Devnexus 2023.
They sit down with Sonatype’s Kadi Grigg and Theresa Mammarella for an unforgettable conversation about making an impact in the tech community. They cover topics like:
Their unique journeys in tech
Embracing the mindset of a lifelong learner
The power of goal setting for personal growth
The essential qualities of a great leader
Why conference talks, like this one, fuel their passion and drive
Don...2023-04-2841 min
Wicked Good DevelopmentEpisode 32: Java Queens at Devnexus 2023Prepare for an insightful discussion with Java Champions Erin Schnable, Emily Jiang, Mary Gygleski, and Holly Cummins at Devnexus 2023.
They sit down with Sonatype’s Kadi Grigg and Theresa Mammarella for an unforgettable conversation about making an impact in the tech community. They cover topics like:
Their unique journeys in tech
Embracing the mindset of a lifelong learner
The power of goal setting for personal growth
The essential qualities of a great leader
Why conference talks, like this one, fuel their passion and drive
Don...2023-04-2841 min Pub House NetworkOffHeap 79. DevNexus 2023! With Brian Fox (CTO of Sonatype)We are at it again! We went to DevNexus in Atlanta, and we have the WHOLE GANG showing up! It has been great catching up in person and oh boy, there's so much tech to talk about! For this episode we have Brian Fox (@Brian_Fox), CTO of Sonatype talk...2023-04-2700 min
Pub House NetworkOffHeap 79. DevNexus 2023! With Brian Fox (CTO of Sonatype)We are at it again! We went to DevNexus in Atlanta, and we have the WHOLE GANG showing up! It has been great catching up in person and oh boy, there's so much tech to talk about! For this episode we have Brian Fox (@Brian_Fox), CTO of Sonatype talk...2023-04-2700 min Pub House NetworkOffHeap 79. DevNexus 2023! With Brian Fox (CTO of Sonatype)We are at it again! We went to DevNexus in Atlanta, and we have the WHOLE GANG showing up! It has been great catching up in person and oh boy, there's so much tech to talk about! For this episode we have Brian Fox (@Brian_Fox), CTO of Sonatype talk...2023-04-2700 min
Pub House NetworkOffHeap 79. DevNexus 2023! With Brian Fox (CTO of Sonatype)We are at it again! We went to DevNexus in Atlanta, and we have the WHOLE GANG showing up! It has been great catching up in person and oh boy, there's so much tech to talk about! For this episode we have Brian Fox (@Brian_Fox), CTO of Sonatype talk...2023-04-2700 min Java Off-HeapOffHeap 79. DevNexus 2023! With Brian Fox (CTO of Sonatype)We are at it again! We went to DevNexus in Atlanta, and we have the WHOLE GANG showing up! It has been great catching up in person and oh boy, there's so much tech to talk about! For this episode we have Brian Fox (@Brian_Fox), CTO of Sonatype talk...2023-04-2700 min
Java Off-HeapOffHeap 79. DevNexus 2023! With Brian Fox (CTO of Sonatype)We are at it again! We went to DevNexus in Atlanta, and we have the WHOLE GANG showing up! It has been great catching up in person and oh boy, there's so much tech to talk about! For this episode we have Brian Fox (@Brian_Fox), CTO of Sonatype talk...2023-04-2700 min Remote Work Life PodcastRWL171 - Sonatype, on the Remote Work Life Business SpotlightHey, it’s Alex from Remote Work Life... On today’s episode of the Remote Work Life Business Spotlight, I’m featuring yet another top remote business called, Sonatype! Want to work remotely from home or anywhere so you can avoid the morning commute and have more freedom? Download a list of 100 tech businesses that hire remote professionals and freelancersDOWNLOAD 100 Remote Business List FREE: https://remoteworklife.ioGet a Free eCourse and Remote CEO Insights That Reveal How to Grow Your Work-From-Anywhere Career, Get Hired And Thrive,PLUS Get A List of 100 Hiring Remote B...2023-04-2509 min
Remote Work Life PodcastRWL171 - Sonatype, on the Remote Work Life Business SpotlightHey, it’s Alex from Remote Work Life... On today’s episode of the Remote Work Life Business Spotlight, I’m featuring yet another top remote business called, Sonatype! Want to work remotely from home or anywhere so you can avoid the morning commute and have more freedom? Download a list of 100 tech businesses that hire remote professionals and freelancersDOWNLOAD 100 Remote Business List FREE: https://remoteworklife.ioGet a Free eCourse and Remote CEO Insights That Reveal How to Grow Your Work-From-Anywhere Career, Get Hired And Thrive,PLUS Get A List of 100 Hiring Remote B...2023-04-2509 min Wicked Good DevelopmentEpisode 31: Testcontainers with Oleg ŠelajevReady to take a dive into the world of TestContainers? Join Kadi Grigg and Sonatype Developer Advocate Jamie Coleman as they sit down with the one and only Oleg Šelajev of AtomicJar, Inc., for an episode packed with insights and laughs.
Together, they'll delve into the world of Testcontainers and uncover the secrets behind these powerful tools that have revolutionized the testing landscape. From the origin of Testcontainers to the crucial importance of reliability in testing, they'll cover it all and so much more
Check out the resources for this episode on the Sonatype Blog. ...2023-04-1138 min
Wicked Good DevelopmentEpisode 31: Testcontainers with Oleg ŠelajevReady to take a dive into the world of TestContainers? Join Kadi Grigg and Sonatype Developer Advocate Jamie Coleman as they sit down with the one and only Oleg Šelajev of AtomicJar, Inc., for an episode packed with insights and laughs.
Together, they'll delve into the world of Testcontainers and uncover the secrets behind these powerful tools that have revolutionized the testing landscape. From the origin of Testcontainers to the crucial importance of reliability in testing, they'll cover it all and so much more
Check out the resources for this episode on the Sonatype Blog. ...2023-04-1138 min Tech TransformsEpisode 56: Safeguarding Our Most Trusted Software with Open Source Technology with Stephen MagillStephen Magill, Vice President, Product Innovation at Sonatype dives into the complexities of open source and software security. Find out how government agencies are utilizing open source, and what Sonatype is doing to help secure our most trusted software.Episode Table of Contents[0:23] The Core Focus Area of Open Source Technology[7:24] The Security Measures Open Source Implements[14:32] A Vulnerability in the Open Source[21:42] The Vulnerability Log4j Poses in the Open Source[29:06] Identifying the Root of the Problem[36:01] Watching Out for Malicious CodeEpisode Links and ResourcesStephen MagillSonatypeSonatype Safety RatingMaven Central2023-03-2941 min
Tech TransformsEpisode 56: Safeguarding Our Most Trusted Software with Open Source Technology with Stephen MagillStephen Magill, Vice President, Product Innovation at Sonatype dives into the complexities of open source and software security. Find out how government agencies are utilizing open source, and what Sonatype is doing to help secure our most trusted software.Episode Table of Contents[0:23] The Core Focus Area of Open Source Technology[7:24] The Security Measures Open Source Implements[14:32] A Vulnerability in the Open Source[21:42] The Vulnerability Log4j Poses in the Open Source[29:06] Identifying the Root of the Problem[36:01] Watching Out for Malicious CodeEpisode Links and ResourcesStephen MagillSonatypeSonatype Safety RatingMaven Central2023-03-2941 min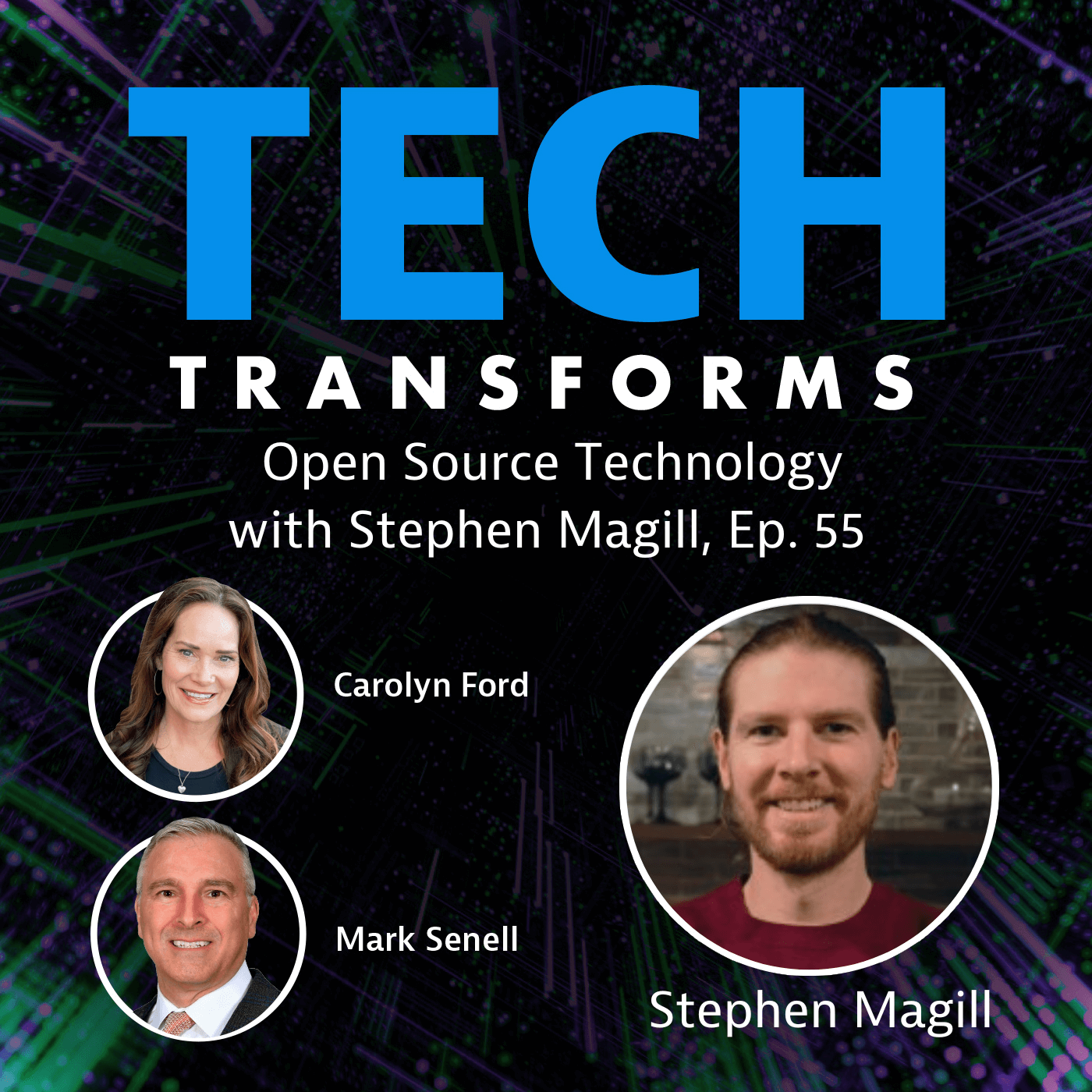 Tech TransformsSafeguarding Our Most Trusted Software with Open Source Technology with Stephen MagillStephen Magill, Vice President, Product Innovation at Sonatype dives into the complexities of open source and software security. Find out how government agencies are utilizing open source, and what Sonatype is doing to help secure our most trusted software.Episode Table of Contents[0:23] The Core Focus Area of Open Source Technology[7:24] The Security Measures Open Source Implements[14:32] A Vulnerability in the Open Source[21:42] The Vulnerability Log4j Poses in the Open Source[29:06] Identifying the Root of the Problem[36:01] Watching Out for Malicious CodeEpisode Links and ResourcesStephen MagillSonatypeSonatype Safety RatingMaven Central2023-03-2941 min
Tech TransformsSafeguarding Our Most Trusted Software with Open Source Technology with Stephen MagillStephen Magill, Vice President, Product Innovation at Sonatype dives into the complexities of open source and software security. Find out how government agencies are utilizing open source, and what Sonatype is doing to help secure our most trusted software.Episode Table of Contents[0:23] The Core Focus Area of Open Source Technology[7:24] The Security Measures Open Source Implements[14:32] A Vulnerability in the Open Source[21:42] The Vulnerability Log4j Poses in the Open Source[29:06] Identifying the Root of the Problem[36:01] Watching Out for Malicious CodeEpisode Links and ResourcesStephen MagillSonatypeSonatype Safety RatingMaven Central2023-03-2941 min Wicked Good DevelopmentEpisode 30: JUG aka The Java User GroupIn our latest episode, we sit down with Steve Poole (Leader of London JUG | Director, Developer Relations, Sonatype), Frank Greco (Founder of NYJavaSIG | Director, Technology and Strategy, Crossroads Technologies), and Sharat Chander (Sr. Director, Java and Cloud Native Product Management and Developer Relations, Oracle).
Java user groups (JUGs) have seen changes over the years due to the growing prominence of Java and a continuously maturing audience. We’ll be revisiting the late 90s/early 2000s when JUGs first started appearing. Listen in for answers to questions like:
What was their purpose?
What are...2023-03-2841 min
Wicked Good DevelopmentEpisode 30: JUG aka The Java User GroupIn our latest episode, we sit down with Steve Poole (Leader of London JUG | Director, Developer Relations, Sonatype), Frank Greco (Founder of NYJavaSIG | Director, Technology and Strategy, Crossroads Technologies), and Sharat Chander (Sr. Director, Java and Cloud Native Product Management and Developer Relations, Oracle).
Java user groups (JUGs) have seen changes over the years due to the growing prominence of Java and a continuously maturing audience. We’ll be revisiting the late 90s/early 2000s when JUGs first started appearing. Listen in for answers to questions like:
What was their purpose?
What are...2023-03-2841 min Wicked Good DevelopmentEpisode 29: White House Unveils New National Cybersecurity StrategyOn March 2, 2023 the Biden-Harris administration made a historic move with the release of the National Cybersecurity Strategy. This is the first time the US government has taken a stance on product liability with regard to software.
In this episode, Jeff Wayman–Conduit of Goodness at Sonatype–takes the mic to speak with Sonatype’s Co-founder and CTO, Brian Fox. Listen in as they break down important details of this historic new strategy, its meaning, and how it impacts you and your organization.
Check out the resources for this episode on the blog. 2023-03-1431 min
Wicked Good DevelopmentEpisode 29: White House Unveils New National Cybersecurity StrategyOn March 2, 2023 the Biden-Harris administration made a historic move with the release of the National Cybersecurity Strategy. This is the first time the US government has taken a stance on product liability with regard to software.
In this episode, Jeff Wayman–Conduit of Goodness at Sonatype–takes the mic to speak with Sonatype’s Co-founder and CTO, Brian Fox. Listen in as they break down important details of this historic new strategy, its meaning, and how it impacts you and your organization.
Check out the resources for this episode on the blog. 2023-03-1431 min Wicked Good DevelopmentEpisode 28: Simon Brown on Visualizing Software ArchitectureWhen you interview your dream guest, the conversation is wicked good. In this episode, Kadi and co-host Sal Kimmich sit down with Simon Brown–creator of the C4 Software Architecture Model–and Developer Advocate Dann Conn. Topics of conversation include the ins and outs of the C4 model, how having a detailed architecture diagram can make or break you, and more.
Tune in as we discuss the intention behind the model, best practices, and how critical it is for technical and non-technical folks alike to understand.
Today's episode resources can be found here. 2023-03-0328 min
Wicked Good DevelopmentEpisode 28: Simon Brown on Visualizing Software ArchitectureWhen you interview your dream guest, the conversation is wicked good. In this episode, Kadi and co-host Sal Kimmich sit down with Simon Brown–creator of the C4 Software Architecture Model–and Developer Advocate Dann Conn. Topics of conversation include the ins and outs of the C4 model, how having a detailed architecture diagram can make or break you, and more.
Tune in as we discuss the intention behind the model, best practices, and how critical it is for technical and non-technical folks alike to understand.
Today's episode resources can be found here. 2023-03-0328 min Wicked Good DevelopmentEpisode 27: Build Breaking and More with ABN AMRO's Ingmar VisJoin Kadi and guest co-host Sola Otudeko for a chat with ABN AMRO’s Ingmar Vis. Listen in as they discuss:
The value of breaking builds.
Why automation is key for agile development.
Lessons he’s learned throughout his open source journey.
What pushed him to give back to open source.
Tune in for the full conversation and check out the resources from this episode here.2023-02-1737 min
Wicked Good DevelopmentEpisode 27: Build Breaking and More with ABN AMRO's Ingmar VisJoin Kadi and guest co-host Sola Otudeko for a chat with ABN AMRO’s Ingmar Vis. Listen in as they discuss:
The value of breaking builds.
Why automation is key for agile development.
Lessons he’s learned throughout his open source journey.
What pushed him to give back to open source.
Tune in for the full conversation and check out the resources from this episode here.2023-02-1737 min FINOS Open Source in Finance PodcastOS in Finance 101: Open Source Developers, Contributors, and Maintainers - Eddie Knight, Sonatype and Colin Griffin, KrumwareIn this episode of the podcast, we sit down with Eddie Knight of Sonatype and Colin Griffin of Krumware. We talk about views on open source in financial services from the developer side, contributor side, and maintainer side. Plus we look at how open source consumption and contribution has changed over the years, and what we see driving the future... security is a big part of all of this. We hope you enjoy!
Eddie's Info: https://www.linkedin.com/in/knight1776/
Colin's Info: https://www.linkedin.com/in/colin-e-griffin/
2022 State of Open Source...2023-02-081h 09
FINOS Open Source in Finance PodcastOS in Finance 101: Open Source Developers, Contributors, and Maintainers - Eddie Knight, Sonatype and Colin Griffin, KrumwareIn this episode of the podcast, we sit down with Eddie Knight of Sonatype and Colin Griffin of Krumware. We talk about views on open source in financial services from the developer side, contributor side, and maintainer side. Plus we look at how open source consumption and contribution has changed over the years, and what we see driving the future... security is a big part of all of this. We hope you enjoy!
Eddie's Info: https://www.linkedin.com/in/knight1776/
Colin's Info: https://www.linkedin.com/in/colin-e-griffin/
2022 State of Open Source...2023-02-081h 09 Wicked Good DevelopmentEpisode 26: Learning with Tom CoolsToday we are celebrating World Open Source Day: A day of celebration of the hard work and dedication done in the open source community and an opportunity to come together and share knowledge and experiences. At Wicked Good Development we thank open source maintainers and contributors for their endless pursuit of showcasing the power of open collaboration for the advancement of technology.
In this episode, Kadi and guest co-host Theresa Mammarella invite open-source contributor, Tom Cools, to share his journey in the world of open source. Sit back and relax as we talk through why he got...2023-02-0331 min
Wicked Good DevelopmentEpisode 26: Learning with Tom CoolsToday we are celebrating World Open Source Day: A day of celebration of the hard work and dedication done in the open source community and an opportunity to come together and share knowledge and experiences. At Wicked Good Development we thank open source maintainers and contributors for their endless pursuit of showcasing the power of open collaboration for the advancement of technology.
In this episode, Kadi and guest co-host Theresa Mammarella invite open-source contributor, Tom Cools, to share his journey in the world of open source. Sit back and relax as we talk through why he got...2023-02-0331 min Wicked Good DevelopmentEpisode 25: The Struggle With Open Source LicensingIn this episode, Kadi and guest co-host, Dariush Griffin, sit down with Filipp Kofman (Partner, Davis Wright Tremaine LLC) and Adam Such (Solutions Architect, Sonatype) to discuss struggles with open source licensing.
There’s not always a clear-cut answer on the best way to handle open source licensing, especially when it comes to managing your dependencies. Topics of discussion include ideas from legal and development perspectives, the struggles they face, and best practices for working together to reach mutually beneficial goals.
Tune in for the full conversation and check out the resources from this episode he...2023-01-2036 min
Wicked Good DevelopmentEpisode 25: The Struggle With Open Source LicensingIn this episode, Kadi and guest co-host, Dariush Griffin, sit down with Filipp Kofman (Partner, Davis Wright Tremaine LLC) and Adam Such (Solutions Architect, Sonatype) to discuss struggles with open source licensing.
There’s not always a clear-cut answer on the best way to handle open source licensing, especially when it comes to managing your dependencies. Topics of discussion include ideas from legal and development perspectives, the struggles they face, and best practices for working together to reach mutually beneficial goals.
Tune in for the full conversation and check out the resources from this episode he...2023-01-2036 min Wicked Good DevelopmentEpisode 24: Cross over with the Federal Tech Podcast featuring Dr. Stephen MagillWhen an interview is that good, you need to share it!
Sonatype's Dr. Stephen Magill joins Federal Tech host, John Gilroy, for a discussion on how software developers can be assured code they develop is safe. Listen in as they discuss topics that range from how even bespoke code needs new versions and improvements over time to other interesting aspects of software risk, like artifacts.
For more information on this episode, check out the resources here.
2023-01-0632 min
Wicked Good DevelopmentEpisode 24: Cross over with the Federal Tech Podcast featuring Dr. Stephen MagillWhen an interview is that good, you need to share it!
Sonatype's Dr. Stephen Magill joins Federal Tech host, John Gilroy, for a discussion on how software developers can be assured code they develop is safe. Listen in as they discuss topics that range from how even bespoke code needs new versions and improvements over time to other interesting aspects of software risk, like artifacts.
For more information on this episode, check out the resources here.
2023-01-0632 min Wicked Good DevelopmentEpisode 23: Demystifying Tech DebtIn this episode, Kadi sits down with Sonatype’s Director of Product Management, Justin Young, and Engineering Manager, Brad Cupit to discuss all things tech debt. What is it? Can different types be treated the same? How do you quantify it? And more importantly, how do you prioritize it?
Tune in and learn how you too can begin to understand your tech debt and begin to tactically manage it.
Check out the resources from today's episode here. 2022-12-1639 min
Wicked Good DevelopmentEpisode 23: Demystifying Tech DebtIn this episode, Kadi sits down with Sonatype’s Director of Product Management, Justin Young, and Engineering Manager, Brad Cupit to discuss all things tech debt. What is it? Can different types be treated the same? How do you quantify it? And more importantly, how do you prioritize it?
Tune in and learn how you too can begin to understand your tech debt and begin to tactically manage it.
Check out the resources from today's episode here. 2022-12-1639 min Dev InterruptedIt’s Not Open Source, It’s You. Where Open Source Risk Comes From w/ SonatypePicture this: an auto manufacturer with no clue what parts are in its supply chain, where those parts come from and no ability to recall those parts if vulnerabilities are discovered.That’s not a reality consumers would accept. So why do organizations (and manufacturers!) tolerate it when it comes to software? On this week’s episode of Dev Interrupted, Brian Fox, co-founder & CTO, and Stephen Magill, VP of Product Innovation, join us to talk about Sonatype’s State of the Software Supply Chain Report. Listen as Brian and Stephen explain the ins and outs...2022-12-1336 min
Dev InterruptedIt’s Not Open Source, It’s You. Where Open Source Risk Comes From w/ SonatypePicture this: an auto manufacturer with no clue what parts are in its supply chain, where those parts come from and no ability to recall those parts if vulnerabilities are discovered.That’s not a reality consumers would accept. So why do organizations (and manufacturers!) tolerate it when it comes to software? On this week’s episode of Dev Interrupted, Brian Fox, co-founder & CTO, and Stephen Magill, VP of Product Innovation, join us to talk about Sonatype’s State of the Software Supply Chain Report. Listen as Brian and Stephen explain the ins and outs...2022-12-1336 min Wicked Good DevelopmentEpisode 22: Fall 2022 Maven Central UpdatesThis session features Brian Fox (CTO and Co-Founder), Joel Orlina (Engineering Manager, Maven), Jason Swank (Director of Engineering, Technical Operations) and Lakshmi Mohandas (Senior Product Manager). Listen in as they discuss Maven Central's relationship with Sonatype, its pain points and how we are addressing them, and the latest updates that make Maven more unified and powerful than before.
Check out the resources from today's episode here.2022-12-0221 min
Wicked Good DevelopmentEpisode 22: Fall 2022 Maven Central UpdatesThis session features Brian Fox (CTO and Co-Founder), Joel Orlina (Engineering Manager, Maven), Jason Swank (Director of Engineering, Technical Operations) and Lakshmi Mohandas (Senior Product Manager). Listen in as they discuss Maven Central's relationship with Sonatype, its pain points and how we are addressing them, and the latest updates that make Maven more unified and powerful than before.
Check out the resources from today's episode here.2022-12-0221 min Wicked Good DevelopmentEpisode 21: James McLeod Shares His Journey to FINOS and BeyondThis session features open source war stories from James McLeod, Director of Community for FINOS–the Financial Technology vertical of the Linux Foundation.
After years in FinTech as a bank software developer, James McLeod now works to create impactful open source technology and communities. He works closely with contributors from the world’s largest investment banks and cloud providers on a daily basis, providing experiences and insights we’re excited to share with our listeners.
Check out the resources from today's episode here. 2022-11-2138 min
Wicked Good DevelopmentEpisode 21: James McLeod Shares His Journey to FINOS and BeyondThis session features open source war stories from James McLeod, Director of Community for FINOS–the Financial Technology vertical of the Linux Foundation.
After years in FinTech as a bank software developer, James McLeod now works to create impactful open source technology and communities. He works closely with contributors from the world’s largest investment banks and cloud providers on a daily basis, providing experiences and insights we’re excited to share with our listeners.
Check out the resources from today's episode here. 2022-11-2138 min Wicked Good DevelopmentEpisode 20: State of the Software Supply Chain Highlights With Tara CondonIn this episode, we're joined by Sonatype's VP Product Marketing and Analyst Relations, Tara Condon. Join us as we talk trends and recommendations for open source dependency management and other critical takeaways from the 8th Annual State of the Software Supply Chain Report.
Check out resources from today's episode here. 2022-11-1706 min
Wicked Good DevelopmentEpisode 20: State of the Software Supply Chain Highlights With Tara CondonIn this episode, we're joined by Sonatype's VP Product Marketing and Analyst Relations, Tara Condon. Join us as we talk trends and recommendations for open source dependency management and other critical takeaways from the 8th Annual State of the Software Supply Chain Report.
Check out resources from today's episode here. 2022-11-1706 min Wicked Good DevelopmentEpisode 19: State of the Software Supply Chain Highlights With Brian FoxCTO and Sonatype Co-Founder Brian Fox is back. Join him and our host for a discussion featuring trends and recommendations for source dependency management and other key takeaways from the 8th Annual State of the Software Supply Chain Report.
Check out resources from today's episode here.2022-11-1705 min
Wicked Good DevelopmentEpisode 19: State of the Software Supply Chain Highlights With Brian FoxCTO and Sonatype Co-Founder Brian Fox is back. Join him and our host for a discussion featuring trends and recommendations for source dependency management and other key takeaways from the 8th Annual State of the Software Supply Chain Report.
Check out resources from today's episode here.2022-11-1705 min Wicked Good DevelopmentEpisode 18: State of the Software Supply Chain Highlights With Stephen MagillThis episode welcomes Ph. D. Stephen Magill, VP of Product Innovation at Sonatype. Listen in as we discuss project quality metrics and key takeaways from the 8th Annual State of the Software Supply Chain Report.
Check out resources from today's episode here.2022-11-1705 min
Wicked Good DevelopmentEpisode 18: State of the Software Supply Chain Highlights With Stephen MagillThis episode welcomes Ph. D. Stephen Magill, VP of Product Innovation at Sonatype. Listen in as we discuss project quality metrics and key takeaways from the 8th Annual State of the Software Supply Chain Report.
Check out resources from today's episode here.2022-11-1705 min Wicked Good DevelopmentEpisode 17: State of the Software Supply Chain Highlights With Ilkka TurunenIn this episode, Sonatype Field CTO, Ilkka Turunen, visits to talk open source supply and critical points from the 8th Annual State of the Software Supply Chain Report.
Check out the resources from today's episode here. 2022-11-1713 min
Wicked Good DevelopmentEpisode 17: State of the Software Supply Chain Highlights With Ilkka TurunenIn this episode, Sonatype Field CTO, Ilkka Turunen, visits to talk open source supply and critical points from the 8th Annual State of the Software Supply Chain Report.
Check out the resources from today's episode here. 2022-11-1713 min Federal Tech Podcast: for innovators, entrepreneurs, and CEOs who want to increase reach and improve brand awarenessEp 32 Reducing Risk for Federal Software Supply ChainsAttacks on the software supply chain have grown by an average of 742% a year since 2019. It makes complete sense if you look at several factors. Years ago, a software developer would write code as part of a large project. It is quite possible they had the opportunity to examine all aspects of their code for vulnerabilities. That transitioned to developers grabbing blocks of code from libraries. Even then, they had at least a chance to review code grabbed from software repositories. Federal mandates regarding cybersecurity are forcing systems administrators to speed along work by using...2022-11-0131 min
Federal Tech Podcast: for innovators, entrepreneurs, and CEOs who want to increase reach and improve brand awarenessEp 32 Reducing Risk for Federal Software Supply ChainsAttacks on the software supply chain have grown by an average of 742% a year since 2019. It makes complete sense if you look at several factors. Years ago, a software developer would write code as part of a large project. It is quite possible they had the opportunity to examine all aspects of their code for vulnerabilities. That transitioned to developers grabbing blocks of code from libraries. Even then, they had at least a chance to review code grabbed from software repositories. Federal mandates regarding cybersecurity are forcing systems administrators to speed along work by using...2022-11-0131 min Wicked Good DevelopmentEpisode 16: Ted Neward's Philosophy 101What does philosophy have to do with software development? More than you might think! In this episode, hosts Kadi and Omar sit down with Technologist, Ted Neward and Developer Advocate, Steve Poole to discuss how philosophy is at the heart of everything. Ted provides great insight as to how his background has influenced his outlook on software development and why developers should be asking themselves the hard questions. As Ted puts it, “It is the hard questions that are usually the good ones that will lead you to a positive outcome.”
Check out the resources from today's epis...2022-10-2154 min
Wicked Good DevelopmentEpisode 16: Ted Neward's Philosophy 101What does philosophy have to do with software development? More than you might think! In this episode, hosts Kadi and Omar sit down with Technologist, Ted Neward and Developer Advocate, Steve Poole to discuss how philosophy is at the heart of everything. Ted provides great insight as to how his background has influenced his outlook on software development and why developers should be asking themselves the hard questions. As Ted puts it, “It is the hard questions that are usually the good ones that will lead you to a positive outcome.”
Check out the resources from today's epis...2022-10-2154 min Wicked Good DevelopmentEpisode 15: Russ Eling Talks Founding OSS Consultants and Open Source ComplianceIn the latest episode, Russ Eling–Founder and CEO of OSS Consultants–sits down with Kadi Grigg and co-host A.J. Brown to discuss his journey with open source. Tune in to hear valuable lessons learned during his tenure as an Open Source Compliance Officer at General Motors and how that eventually led to the creation of OSS Consultants.
Check out the resources from today's episode here.2022-09-2233 min
Wicked Good DevelopmentEpisode 15: Russ Eling Talks Founding OSS Consultants and Open Source ComplianceIn the latest episode, Russ Eling–Founder and CEO of OSS Consultants–sits down with Kadi Grigg and co-host A.J. Brown to discuss his journey with open source. Tune in to hear valuable lessons learned during his tenure as an Open Source Compliance Officer at General Motors and how that eventually led to the creation of OSS Consultants.
Check out the resources from today's episode here.2022-09-2233 min Wicked Good DevelopmentEpisode 14: The Secret Life of Maven CentralIn this episode, Joel Orlina joins Kadi Grigg to provide insights and knowledge on “The Secret Life of Maven Central,” his talk given at Devoxx UK and OpenSFF Day. Joel sheds light on the previously unknown history of Maven Central and how it works under the covers. He also discusses how the Central team addresses critical security risks like dependency confusion and how it responded to security events such as Log4Shell, and most importantly, how you can get involved.
Check out the resources from today's episode here. 2022-08-2637 min
Wicked Good DevelopmentEpisode 14: The Secret Life of Maven CentralIn this episode, Joel Orlina joins Kadi Grigg to provide insights and knowledge on “The Secret Life of Maven Central,” his talk given at Devoxx UK and OpenSFF Day. Joel sheds light on the previously unknown history of Maven Central and how it works under the covers. He also discusses how the Central team addresses critical security risks like dependency confusion and how it responded to security events such as Log4Shell, and most importantly, how you can get involved.
Check out the resources from today's episode here. 2022-08-2637 min Wicked Good DevelopmentEpisode 13: Hacks & Ax: July UpdateAx Sharma, a security researcher at Sonatype and tech journalist at large, joins Kadi and Omar for his monthly malware update. Ax breaks down the latest on protestware and ransomware.
Check out the resources from today's episode here. 2022-08-0316 min
Wicked Good DevelopmentEpisode 13: Hacks & Ax: July UpdateAx Sharma, a security researcher at Sonatype and tech journalist at large, joins Kadi and Omar for his monthly malware update. Ax breaks down the latest on protestware and ransomware.
Check out the resources from today's episode here. 2022-08-0316 min Wicked Good DevelopmentEpisode 12: Devoxx Poland RecapAfter attending the Devoxx Poland Developer Conference in June in Krakow, Kadi and co-host Steve Poole sat down with speakers Oleg Šelajev, Developer Relations at Atomic Jar Inc, Ana-Maria Mihalceanu, Java Champion and Developer Advocate at Redhat, and Brain Vermeer, Java Champion and JUG Leader Netherlands about their key takeaways from the event, trends on cloud adoption, how hot the developer market is right now, and their favorite presentations (hint: they weren’t their own talks!).
Check out the resources from today's episode here. 2022-07-1536 min
Wicked Good DevelopmentEpisode 12: Devoxx Poland RecapAfter attending the Devoxx Poland Developer Conference in June in Krakow, Kadi and co-host Steve Poole sat down with speakers Oleg Šelajev, Developer Relations at Atomic Jar Inc, Ana-Maria Mihalceanu, Java Champion and Developer Advocate at Redhat, and Brain Vermeer, Java Champion and JUG Leader Netherlands about their key takeaways from the event, trends on cloud adoption, how hot the developer market is right now, and their favorite presentations (hint: they weren’t their own talks!).
Check out the resources from today's episode here. 2022-07-1536 min Wicked Good DevelopmentEpisode 11: Vulnerability Drills: What’s the Intention, Habit, and ImpactIn this episode, Kadi and Omar sit down and chat with members of the Developer Relations team at Sonatype to discuss the value in engineering teams doing vulnerability drills. We now live in a world where it's not a matter of if you will get attacked, it’s now a matter of when you will get attacked. So what can you do to protect yourself when that does happen? Learn why this shouldn’t be viewed as an incident response but more as streamlining your operational and engineering levels that need to be in lockstep with one another.
Ch...2022-06-3037 min
Wicked Good DevelopmentEpisode 11: Vulnerability Drills: What’s the Intention, Habit, and ImpactIn this episode, Kadi and Omar sit down and chat with members of the Developer Relations team at Sonatype to discuss the value in engineering teams doing vulnerability drills. We now live in a world where it's not a matter of if you will get attacked, it’s now a matter of when you will get attacked. So what can you do to protect yourself when that does happen? Learn why this shouldn’t be viewed as an incident response but more as streamlining your operational and engineering levels that need to be in lockstep with one another.
Ch...2022-06-3037 min ICS Cyber Talks PodcastAlejandro Gamboa Regional Sales Director Iberia Italy & North Africa @Sonatype about SW supply chainנחשון פינקו מארח את אלחנדרו אסטרדה גמבוהה, מנהל מכירות לאזור איבריה, איטליה וצפון אפריקה בסונאטייפ, בשיחה על האתגרים בתחום הגנת סייבר על שרשראות אספקה בתחום פיתוח תוכנה
מה הגדרת שרשרת האספקה בתחום התוכנה? הצורך בכלי סריקה והגנה לאורך כול שלבי מחזור חיי התוכנה במיוחד בשימוש בספריות קוד פתוח. זיהוי פגיעויות ידועות ולא ידועות בכול שלבי הפיתוח על מנת למנוע התקפות כגון סולרווינדז ועוד
Nachshon Pincu hosts Alejandro Estrada Gamboa, Regional Sales Director Iberia, Italy, and North Africa, at @Sonatype in a conversation about software supply chain cyber risks.
What is a software supply chain? Why is managing the software supply chain so important? What are the consequences if it's not managed? Examples of software supply chain attacks?
What are Sonatype lifecycle software cyber management differentiators from other code scanning tools? And more
2022-06-1449 min
ICS Cyber Talks PodcastAlejandro Gamboa Regional Sales Director Iberia Italy & North Africa @Sonatype about SW supply chainנחשון פינקו מארח את אלחנדרו אסטרדה גמבוהה, מנהל מכירות לאזור איבריה, איטליה וצפון אפריקה בסונאטייפ, בשיחה על האתגרים בתחום הגנת סייבר על שרשראות אספקה בתחום פיתוח תוכנה
מה הגדרת שרשרת האספקה בתחום התוכנה? הצורך בכלי סריקה והגנה לאורך כול שלבי מחזור חיי התוכנה במיוחד בשימוש בספריות קוד פתוח. זיהוי פגיעויות ידועות ולא ידועות בכול שלבי הפיתוח על מנת למנוע התקפות כגון סולרווינדז ועוד
Nachshon Pincu hosts Alejandro Estrada Gamboa, Regional Sales Director Iberia, Italy, and North Africa, at @Sonatype in a conversation about software supply chain cyber risks.
What is a software supply chain? Why is managing the software supply chain so important? What are the consequences if it's not managed? Examples of software supply chain attacks?
What are Sonatype lifecycle software cyber management differentiators from other code scanning tools? And more
2022-06-1449 min Wicked Good DevelopmentEpisode 10: Evolution of Supply Chain AttacksFor this episode, Jamie Whitehouse, Director of Product Management at Sonatype, joins Kadi as guest host. With the unique perspectives of a Product Manager, Engineering Manager Daryl Handley, Data Scientist Cody Nash, and principal Engineer AJ Brown, we dissect the evolution of software supply chain attacks and lessons learned. We’ll dive into how credit card fraud detection and supply chain attack detection is similar, the data science behind these systems, and the behavior of the developers.
Check out the resources from today's episode here. 2022-06-0933 min
Wicked Good DevelopmentEpisode 10: Evolution of Supply Chain AttacksFor this episode, Jamie Whitehouse, Director of Product Management at Sonatype, joins Kadi as guest host. With the unique perspectives of a Product Manager, Engineering Manager Daryl Handley, Data Scientist Cody Nash, and principal Engineer AJ Brown, we dissect the evolution of software supply chain attacks and lessons learned. We’ll dive into how credit card fraud detection and supply chain attack detection is similar, the data science behind these systems, and the behavior of the developers.
Check out the resources from today's episode here. 2022-06-0933 min Wicked Good DevelopmentEpisode 9: Developer and Open Source Contributor Stories at Devnexus Part 3This episode is three fold as we finish up the roundtable discussion on Devnexus 2022 and we get a chance to interview two more developers who contribute to the open source community. We connect with Luis Majano, CEO of Ortus Solutions and long-time computer engineer, about putting in the open source work. From using a 70/30 ratio to dedicate time building open source in between client work to getting the next generation involved in maintaining minor code fixes first-hand, hear how the level of work put in makes the difference in professional open source. We also learn with Grace Jansen, Developer...2022-05-1430 min
Wicked Good DevelopmentEpisode 9: Developer and Open Source Contributor Stories at Devnexus Part 3This episode is three fold as we finish up the roundtable discussion on Devnexus 2022 and we get a chance to interview two more developers who contribute to the open source community. We connect with Luis Majano, CEO of Ortus Solutions and long-time computer engineer, about putting in the open source work. From using a 70/30 ratio to dedicate time building open source in between client work to getting the next generation involved in maintaining minor code fixes first-hand, hear how the level of work put in makes the difference in professional open source. We also learn with Grace Jansen, Developer...2022-05-1430 min Wicked Good DevelopmentEpisode 8: Developer and Open Source Contributor Stories at Devnexus Part 2Brad Wood, Software Architect at Ortus Solutions says “everybody should be secure” when it comes to open source security. Hear Brad’s distinctive perspective after occupying roles of both an open source maintainer and contributor. From the advantages of using ColdFusion to the effects of trust in development like abandonware and namespace confusion attacks, Brad covers it all with Wicked Good Development at DevNexus 2022.
Check out the resources from today's episode here. 2022-05-1328 min
Wicked Good DevelopmentEpisode 8: Developer and Open Source Contributor Stories at Devnexus Part 2Brad Wood, Software Architect at Ortus Solutions says “everybody should be secure” when it comes to open source security. Hear Brad’s distinctive perspective after occupying roles of both an open source maintainer and contributor. From the advantages of using ColdFusion to the effects of trust in development like abandonware and namespace confusion attacks, Brad covers it all with Wicked Good Development at DevNexus 2022.
Check out the resources from today's episode here. 2022-05-1328 min Wicked Good DevelopmentEpisode 7: Developer and Open Source Contributor Stories at Devnexus Part 1This episode is the first in a mini-series from our experience at Devnexus 2022. It was an exciting time to learn from developers and capture wisdom from the open source community. The life of a contributor told by Maarten Mulders, Consultant, Trainer, and Technology Advocate at Info Support, plays out on Wicked Good Development during DevNexus 2022. Considering Apache Maven to be the cornerstone for Java development, hear how Maarten navigates fixing bugs, avoiding build breaks, and Java derivative languages.
Check out the resources from today's episode here. 2022-05-1126 min
Wicked Good DevelopmentEpisode 7: Developer and Open Source Contributor Stories at Devnexus Part 1This episode is the first in a mini-series from our experience at Devnexus 2022. It was an exciting time to learn from developers and capture wisdom from the open source community. The life of a contributor told by Maarten Mulders, Consultant, Trainer, and Technology Advocate at Info Support, plays out on Wicked Good Development during DevNexus 2022. Considering Apache Maven to be the cornerstone for Java development, hear how Maarten navigates fixing bugs, avoiding build breaks, and Java derivative languages.
Check out the resources from today's episode here. 2022-05-1126 min Tech Stories from HackerNoonCan We Protect Ourselves Against Zero-click Attacks?If you’re still not scared of cybercriminals now, you might be after hearing about zero-click attacks from Cam Canales, a Cybersecurity Analyst at CDW 👀 Amy and Cam chat about zero-click attacks like the NGO Baharani attack, Jeff Bezos’ zero-click downfall (almost forgot he was even alive anymore 😜), and the WhatsApp Pegasus phone call attack. They also get into securing devices on and off your corporate network. 💚
On this episode of The HackerNoon Podcast:
What is a zero-click attack? (03:35) 😱
What did we learn from the NGO Baharani attack? (06:09) 🥺
What layers of security do I need when I am deali...2022-05-1031 min
Tech Stories from HackerNoonCan We Protect Ourselves Against Zero-click Attacks?If you’re still not scared of cybercriminals now, you might be after hearing about zero-click attacks from Cam Canales, a Cybersecurity Analyst at CDW 👀 Amy and Cam chat about zero-click attacks like the NGO Baharani attack, Jeff Bezos’ zero-click downfall (almost forgot he was even alive anymore 😜), and the WhatsApp Pegasus phone call attack. They also get into securing devices on and off your corporate network. 💚
On this episode of The HackerNoon Podcast:
What is a zero-click attack? (03:35) 😱
What did we learn from the NGO Baharani attack? (06:09) 🥺
What layers of security do I need when I am deali...2022-05-1031 min Tech Stories from HackerNoonGathering Threat Intelligence to Strengthen SecurityStand up and listen in, Hackers! Nour Fateen, a Sales Engineering Manager at Recorded Future, talks to Amy about threat intelligence. They chat about the Threat Intelligence Lifecycle process of gathering data, analyzing it, and using it to secure your organization.
On this episode of The HackerNoon Podcast:
How did Nour get into cybersecurity? (02:00)
Where do people start when they want to set up their security stack? (07:06)
What kind of data do I need to gather to understand my organization’s state of security? (12:08)
How can people who have a technical background learn about cyb...2022-04-2734 min
Tech Stories from HackerNoonGathering Threat Intelligence to Strengthen SecurityStand up and listen in, Hackers! Nour Fateen, a Sales Engineering Manager at Recorded Future, talks to Amy about threat intelligence. They chat about the Threat Intelligence Lifecycle process of gathering data, analyzing it, and using it to secure your organization.
On this episode of The HackerNoon Podcast:
How did Nour get into cybersecurity? (02:00)
Where do people start when they want to set up their security stack? (07:06)
What kind of data do I need to gather to understand my organization’s state of security? (12:08)
How can people who have a technical background learn about cyb...2022-04-2734 min Tech Stories from HackerNoonDiscussing the Russia-Ukraine Cyber War with Eran FineAmy chats with Eran Fine, the CEO and Co-founder of Nanolock Security, about the ongoing cyber war in Ukraine. They also chat about the history of Russian-Ukrainian cyber attacks, ransomware, the Colonial Pipeline attack, and more. 🇺🇦
On this episode of The HackerNoon Podcast:
Who needs to care about ransomware? 😱
Why is Ukraine not experiencing massive infrastructure-related cyber attacks - like what happened with Colonial Pipeline? ⛽️
Who needs to be worried about cyber threats right now? 😫
How can we prevent and mitigate such cyber attacks? 🥺
This episode is sponsored by Sonatype - the software supply c...2022-04-1923 min
Tech Stories from HackerNoonDiscussing the Russia-Ukraine Cyber War with Eran FineAmy chats with Eran Fine, the CEO and Co-founder of Nanolock Security, about the ongoing cyber war in Ukraine. They also chat about the history of Russian-Ukrainian cyber attacks, ransomware, the Colonial Pipeline attack, and more. 🇺🇦
On this episode of The HackerNoon Podcast:
Who needs to care about ransomware? 😱
Why is Ukraine not experiencing massive infrastructure-related cyber attacks - like what happened with Colonial Pipeline? ⛽️
Who needs to be worried about cyber threats right now? 😫
How can we prevent and mitigate such cyber attacks? 🥺
This episode is sponsored by Sonatype - the software supply c...2022-04-1923 min Wicked Good DevelopmentEpisode 6: The Logic of Code QualityWrite code so good you don’t need documentation to go along with it. Achieving code quality that is measurable, efficient, and scalable across even the leanest development teams can feel like a stunt. Yet, the costs of growing tech debt make setting a standard a no-brainer. From defining code quality, how to measure it, and the best time to involve quality checks in the development process, join a comprehensive talk on the logic of high code quality.
Coming straight from Sonatype in-house industry experts Product Manager Rohan Bhaumik, Developer Advocate Sal Kimmich, and VP of product in...2022-04-1333 min
Wicked Good DevelopmentEpisode 6: The Logic of Code QualityWrite code so good you don’t need documentation to go along with it. Achieving code quality that is measurable, efficient, and scalable across even the leanest development teams can feel like a stunt. Yet, the costs of growing tech debt make setting a standard a no-brainer. From defining code quality, how to measure it, and the best time to involve quality checks in the development process, join a comprehensive talk on the logic of high code quality.
Coming straight from Sonatype in-house industry experts Product Manager Rohan Bhaumik, Developer Advocate Sal Kimmich, and VP of product in...2022-04-1333 min Tech Stories from HackerNoonWomen in Cybersecurity with SheSec PakistanGirl, pull up a chair and take a seat at the head of the boardroom because we are talking about women in cybersecurity this week on The HackerNoon Podcast. Misbah Fatima (Head of Security) and Farza Ashraf (Security Analyst) from Idenfo and SheSec Pakistan talk about how we can increase the number of women in STEM.
On this episode of The HackerNoon Podcast:
How did Farza get into tech and cybersecurity? 💃
How did Misbah get her first job in the cybersecurity industry? 👩💻
Is cybersecurity a good field for women to get into? 🤔
How important is community building for w...2022-04-1238 min
Tech Stories from HackerNoonWomen in Cybersecurity with SheSec PakistanGirl, pull up a chair and take a seat at the head of the boardroom because we are talking about women in cybersecurity this week on The HackerNoon Podcast. Misbah Fatima (Head of Security) and Farza Ashraf (Security Analyst) from Idenfo and SheSec Pakistan talk about how we can increase the number of women in STEM.
On this episode of The HackerNoon Podcast:
How did Farza get into tech and cybersecurity? 💃
How did Misbah get her first job in the cybersecurity industry? 👩💻
Is cybersecurity a good field for women to get into? 🤔
How important is community building for w...2022-04-1238 min Wicked Good DevelopmentEpisode 5: Women in Tech #Breaking the Bias“I’ll block, you run.” In this encouraging talk from four women in tech at Sonatype, hear how their career paths have shaped how they support mitigating and interrupting bias at work and ways to create environments that empower women to be their authentic selves every day.
Join Senior Security Researcher Ankita Lamba, Product Manager Grace Lee, Customer Success Engineer Santi Mulukutla, and Director of Agile Coaching Sue Jasmin as they create space to discuss:
-The importance of active sponsorship and mentorship
-How to eliminate bias in the hiring process
-Cultural limita...2022-04-0738 min
Wicked Good DevelopmentEpisode 5: Women in Tech #Breaking the Bias“I’ll block, you run.” In this encouraging talk from four women in tech at Sonatype, hear how their career paths have shaped how they support mitigating and interrupting bias at work and ways to create environments that empower women to be their authentic selves every day.
Join Senior Security Researcher Ankita Lamba, Product Manager Grace Lee, Customer Success Engineer Santi Mulukutla, and Director of Agile Coaching Sue Jasmin as they create space to discuss:
-The importance of active sponsorship and mentorship
-How to eliminate bias in the hiring process
-Cultural limita...2022-04-0738 min Wicked Good DevelopmentEpisode 4: Spring4shellDid Spring4Shell set the internet on fire again? Not so fast. In a special episode of Wicked Good Development, we dissect the zero-day RCE vulnerability in the Spring Framework dubbed Spring4Shell or Springshell. From comparisons to Log4j to how to remediate it and what versions on vulnerable, the experts on today's show break down what we know so far about this new vulnerability. And most importantly, how to determine if you're affected.
Check out the resources from today's episode here.2022-04-0215 min
Wicked Good DevelopmentEpisode 4: Spring4shellDid Spring4Shell set the internet on fire again? Not so fast. In a special episode of Wicked Good Development, we dissect the zero-day RCE vulnerability in the Spring Framework dubbed Spring4Shell or Springshell. From comparisons to Log4j to how to remediate it and what versions on vulnerable, the experts on today's show break down what we know so far about this new vulnerability. And most importantly, how to determine if you're affected.
Check out the resources from today's episode here.2022-04-0215 min Wicked Good DevelopmentEpisode 3: Central: A Look Back and a Look ForwardIf you utilize Java or any other JVM, there’s a good chance you know the Maven Central repository. Today’s episode brings long-time maintainers and contributors of Maven Central, Brian Fox, Jason Swank, and Joel Orlina to the mic to rehash the early days of Maven Central, lessons learned from managing open source ecosystems, and bring insight into the platform’s practical software supply chain management capabilities of the past, present, and future.
Check out the resources from today's episode here. 2022-03-2140 min
Wicked Good DevelopmentEpisode 3: Central: A Look Back and a Look ForwardIf you utilize Java or any other JVM, there’s a good chance you know the Maven Central repository. Today’s episode brings long-time maintainers and contributors of Maven Central, Brian Fox, Jason Swank, and Joel Orlina to the mic to rehash the early days of Maven Central, lessons learned from managing open source ecosystems, and bring insight into the platform’s practical software supply chain management capabilities of the past, present, and future.
Check out the resources from today's episode here. 2022-03-2140 min Tech Stories from HackerNoonHow to Recover from the Log4j Supply Chain Attack with Ilkka TurunenIn this episode of the HackerNoon Podcast, Amy Tom sits down with Ilkka Turunen to talk about Supply Chain Security. They go over the Log4J incident that made a lot of apps built-in Java vulnerable to exploitation, what it means to be a field CTO, how companies can place themselves to collect user feedback, and a lot more!
Ilkka Turunen is the Field CTO of https://www.sonatype.com/ (Sonatype).
On this episode of the HackerNoon Podcast, Amy Tom and Ilkka Turunen chat about:
What is a field CTO an...2022-03-1635 min
Tech Stories from HackerNoonHow to Recover from the Log4j Supply Chain Attack with Ilkka TurunenIn this episode of the HackerNoon Podcast, Amy Tom sits down with Ilkka Turunen to talk about Supply Chain Security. They go over the Log4J incident that made a lot of apps built-in Java vulnerable to exploitation, what it means to be a field CTO, how companies can place themselves to collect user feedback, and a lot more!
Ilkka Turunen is the Field CTO of https://www.sonatype.com/ (Sonatype).
On this episode of the HackerNoon Podcast, Amy Tom and Ilkka Turunen chat about:
What is a field CTO an...2022-03-1635 min IT VisionariesSecuring the Supply Chain… for Software With Brian Fox, Co-Founder, SVP and CTOIf companies don't truly know the elements in their products, then they are set up for trouble. According to Brian Fox, Co-Founder, SVP and CTO of Sonatype, without this knowledge they won’t know how to address issues or if bad actors have infiltrated their products with disruptive parts. Brian advises that all aspects in the supply chain for software must be identified and secured just like any physical product. Tune in to learn:How does Sonatype help companies make better supply chain decisions for their software? (01:56)How did Sonatype evolve to focus on supply cha...2022-03-1542 min
IT VisionariesSecuring the Supply Chain… for Software With Brian Fox, Co-Founder, SVP and CTOIf companies don't truly know the elements in their products, then they are set up for trouble. According to Brian Fox, Co-Founder, SVP and CTO of Sonatype, without this knowledge they won’t know how to address issues or if bad actors have infiltrated their products with disruptive parts. Brian advises that all aspects in the supply chain for software must be identified and secured just like any physical product. Tune in to learn:How does Sonatype help companies make better supply chain decisions for their software? (01:56)How did Sonatype evolve to focus on supply cha...2022-03-1542 min Wicked Good DevelopmentEpisode 2: Starting Security LeftIn today's episode, we're tackling the ongoing discussion about shifting security left - or really starting security left. What do developers need to understand about the current state of application security? How should they be involved in security decisions? What's involved in building secure code from the beginning? This episode wraps up on the topic of what questions organizations and developers should be asking themselves when it comes to their security practices.
Check out the resources from today's episode here. 2022-02-1831 min
Wicked Good DevelopmentEpisode 2: Starting Security LeftIn today's episode, we're tackling the ongoing discussion about shifting security left - or really starting security left. What do developers need to understand about the current state of application security? How should they be involved in security decisions? What's involved in building secure code from the beginning? This episode wraps up on the topic of what questions organizations and developers should be asking themselves when it comes to their security practices.
Check out the resources from today's episode here. 2022-02-1831 min Wicked Good DevelopmentEpisode 1: Cybersecurity Experts, Log4j, and Open SourceThree industry experts with different ties to the world of software talk about the latest in software, from Log4j to today, and what remediation looks like for development teams. We discuss update behaviors in the development community and the risks associated with using old code. To round out our debut episode - we talk about the silent industrial revolution and who bears the burden of maintaining open source software.
Check out the resources from today's episode here. 2022-02-0346 min
Wicked Good DevelopmentEpisode 1: Cybersecurity Experts, Log4j, and Open SourceThree industry experts with different ties to the world of software talk about the latest in software, from Log4j to today, and what remediation looks like for development teams. We discuss update behaviors in the development community and the risks associated with using old code. To round out our debut episode - we talk about the silent industrial revolution and who bears the burden of maintaining open source software.
Check out the resources from today's episode here. 2022-02-0346 min CTO Confessions Brought to you by IT LabsEpisode 78: Open Source, Open Security With Brian FoxThe open-source world is a wonderful democracy and meritocracy of innovation, software elements, and applications. Its creativity is incorporated into countless (if not all) major applications across the tech arena. But with it comes complexities. And in this podcast, we get to speak to Brian Fox, the CTO & Co-founder of Sonatype, about those complexities. In particular, the worrying world of security. Sonatype runs the central repository of Maven, where the world gets its open-source Java. A kind of Center of the open-source universe. Or at least one of them. Sonatype also focuses on developing a smarter, faster, and more secure...2021-10-271h 18
CTO Confessions Brought to you by IT LabsEpisode 78: Open Source, Open Security With Brian FoxThe open-source world is a wonderful democracy and meritocracy of innovation, software elements, and applications. Its creativity is incorporated into countless (if not all) major applications across the tech arena. But with it comes complexities. And in this podcast, we get to speak to Brian Fox, the CTO & Co-founder of Sonatype, about those complexities. In particular, the worrying world of security. Sonatype runs the central repository of Maven, where the world gets its open-source Java. A kind of Center of the open-source universe. Or at least one of them. Sonatype also focuses on developing a smarter, faster, and more secure...2021-10-271h 18 Na PodsłuchuNP #035 - ten, w którym wszędzie przewija się ZombieW tym odcinku rozmawiamy o skanowaniu numerów i sieci telefonicznych, stalkowaniu partnerek (i partnerów) nie tylko AirTagami, a także wspominamy McAfee'ego (R.I.P.) i zastanawiamy się nad tym, czy routery powinny mieć daty ważności. == LINKI ==Co ten Windows z Amazonem:https://www.theverge.com/2021/6/24/22548428/microsoft-windows-11-android-apps-support-amazon-storeRaport ze skanowania sieci telefonicznej w poszukiwaniu Zombie: https://shufflingbytes.com/posts/wardialing-finnish-freephones/Webinar o technikach komunikacji szpiegów:https://sklep.niebezpiecznik.pl/opis/17Sprytna usługa Google:https://cloud.google.com/speech-to-textBriar - komunikator na czasy apokalipsy Zombie:https://briarproject.org/Inwigilacja AirTagami:https://www.macrumors.com/guide/airtags/h...2021-07-0200 min
Na PodsłuchuNP #035 - ten, w którym wszędzie przewija się ZombieW tym odcinku rozmawiamy o skanowaniu numerów i sieci telefonicznych, stalkowaniu partnerek (i partnerów) nie tylko AirTagami, a także wspominamy McAfee'ego (R.I.P.) i zastanawiamy się nad tym, czy routery powinny mieć daty ważności. == LINKI ==Co ten Windows z Amazonem:https://www.theverge.com/2021/6/24/22548428/microsoft-windows-11-android-apps-support-amazon-storeRaport ze skanowania sieci telefonicznej w poszukiwaniu Zombie: https://shufflingbytes.com/posts/wardialing-finnish-freephones/Webinar o technikach komunikacji szpiegów:https://sklep.niebezpiecznik.pl/opis/17Sprytna usługa Google:https://cloud.google.com/speech-to-textBriar - komunikator na czasy apokalipsy Zombie:https://briarproject.org/Inwigilacja AirTagami:https://www.macrumors.com/guide/airtags/h...2021-07-0200 min Na PodsłuchuNP #035 - ten, w którym wszędzie przewija się ZombieW tym odcinku rozmawiamy o skanowaniu numerów i sieci telefonicznych, stalkowaniu partnerek (i partnerów) nie tylko AirTagami, a także wspominamy McAfee'ego (R.I.P.) i zastanawiamy się nad tym, czy routery powinny mieć daty ważności. == LINKI ==Co ten Windows z Amazonem:https://www.theverge.com/2021/6/24/22548428/microsoft-windows-11-android-apps-support-amazon-storeRaport ze skanowania sieci telefonicznej w poszukiwaniu Zombie: https://shufflingbytes.com/posts/wardialing-finnish-freephones/Webinar o technikach komunikacji szpiegów:https://sklep.niebezpiecznik.pl/opis/17Sprytna usługa Google:https://cloud.google.com/speech-to-textBriar - komunikator na czasy apokalipsy Zombie:https://briarproject.org/Inwigilacja AirTagami:https://www.macrumors.com/guide/airtags/h...2021-07-0200 min
Na PodsłuchuNP #035 - ten, w którym wszędzie przewija się ZombieW tym odcinku rozmawiamy o skanowaniu numerów i sieci telefonicznych, stalkowaniu partnerek (i partnerów) nie tylko AirTagami, a także wspominamy McAfee'ego (R.I.P.) i zastanawiamy się nad tym, czy routery powinny mieć daty ważności. == LINKI ==Co ten Windows z Amazonem:https://www.theverge.com/2021/6/24/22548428/microsoft-windows-11-android-apps-support-amazon-storeRaport ze skanowania sieci telefonicznej w poszukiwaniu Zombie: https://shufflingbytes.com/posts/wardialing-finnish-freephones/Webinar o technikach komunikacji szpiegów:https://sklep.niebezpiecznik.pl/opis/17Sprytna usługa Google:https://cloud.google.com/speech-to-textBriar - komunikator na czasy apokalipsy Zombie:https://briarproject.org/Inwigilacja AirTagami:https://www.macrumors.com/guide/airtags/h...2021-07-0200 min SANS Internet Storm Center's Daily Network Security News PodcastNetwork Security News Summary for Wednesday June 23rd, 2021Phishing Avoiding Reports; PyPi Cryptominer; dovecot TLS Fix; Incomplete Sonicwall Patch Phishing asking recipients not to report abuse https://isc.sans.edu/forums/diary/Phishing+asking+recipients+not+to+report+abuse/27556/ PyPi Cryptomining Malware https://blog.sonatype.com/sonatype-catches-new-pypi-cryptomining-malware-via-automated-detection Dovecot TLS Implementation Vulnerability https://hackerone.com/reports/1204962 (see the link to the PDF for more details) Sonicwall Patch Incomplete https://www.tripwire.com/state-of-security/featured/analyzing-sonicwalls-unsuccessful-fix-for-cve-2020-5135/ keywords: sonicwall; dovecot; tls; starttls; pypi; phishing; abuse2021-06-2306 min
SANS Internet Storm Center's Daily Network Security News PodcastNetwork Security News Summary for Wednesday June 23rd, 2021Phishing Avoiding Reports; PyPi Cryptominer; dovecot TLS Fix; Incomplete Sonicwall Patch Phishing asking recipients not to report abuse https://isc.sans.edu/forums/diary/Phishing+asking+recipients+not+to+report+abuse/27556/ PyPi Cryptomining Malware https://blog.sonatype.com/sonatype-catches-new-pypi-cryptomining-malware-via-automated-detection Dovecot TLS Implementation Vulnerability https://hackerone.com/reports/1204962 (see the link to the PDF for more details) Sonicwall Patch Incomplete https://www.tripwire.com/state-of-security/featured/analyzing-sonicwalls-unsuccessful-fix-for-cve-2020-5135/ keywords: sonicwall; dovecot; tls; starttls; pypi; phishing; abuse2021-06-2306 min CISO Series PodcastHoly Crap! We’ve Been Doing This for Three Years!All links and images for this episode can be found on CISO Series https://cisoseries.com/holy-crap-weve-been-doing-this-for-three-years/ On this day three years ago, Mike Johnson and I released the first episode of CISO Series’ CISO/Security Vendor Relationship Podcast. Our primary goal was to talk about the strained yet much needed relationship between security practitioners and vendors. With the help of our guest Dan Walsh, CISO, VillageMD and plenty of contributors we look back and ask ourselves, “What’s changed and has anything improved?” If you're interested in hearing the full story of...2021-06-0133 min
CISO Series PodcastHoly Crap! We’ve Been Doing This for Three Years!All links and images for this episode can be found on CISO Series https://cisoseries.com/holy-crap-weve-been-doing-this-for-three-years/ On this day three years ago, Mike Johnson and I released the first episode of CISO Series’ CISO/Security Vendor Relationship Podcast. Our primary goal was to talk about the strained yet much needed relationship between security practitioners and vendors. With the help of our guest Dan Walsh, CISO, VillageMD and plenty of contributors we look back and ask ourselves, “What’s changed and has anything improved?” If you're interested in hearing the full story of...2021-06-0133 min Defense in DepthHiring Talent with No Security ExperienceAll links and images for this episode can be found on CISO Series https://cisoseries.com/defense-in-depth-hiring-talent-with-no-security-experience/ Should you look for the ideal candidate that has all the security talent you want, or should you find the right person and train them with the security talent you want. And if the latter, what is the right person to work in security who doesn't have security experience? Check out this post and this Twitter discussion for the basis for our conversation on this week’s episode which features me, David Spark (@dspark), producer of CI...2021-05-2727 min
Defense in DepthHiring Talent with No Security ExperienceAll links and images for this episode can be found on CISO Series https://cisoseries.com/defense-in-depth-hiring-talent-with-no-security-experience/ Should you look for the ideal candidate that has all the security talent you want, or should you find the right person and train them with the security talent you want. And if the latter, what is the right person to work in security who doesn't have security experience? Check out this post and this Twitter discussion for the basis for our conversation on this week’s episode which features me, David Spark (@dspark), producer of CI...2021-05-2727 min CISO Series PodcastSomething Stinks In Here. I Think It’s Your Code.All links and images for this episode can be found on CISO Series https://cisoseries.com/something-stinks-in-here-i-think-it's-your-code/ The problem isn't our users, it's you and your past due code. Something happened. It's either been tainted or expired, but whatever it is, it smells and you need to clean it up. This episode is hosted by me, David Spark (@dspark), producer of CISO Series and Mike Johnson. Our sponsored guest this week is Brian Fox (@brian_fox), co-founder and CTO, Sonatype. Thanks to our podcast sponsor, Sonatype With sec...2021-05-2535 min
CISO Series PodcastSomething Stinks In Here. I Think It’s Your Code.All links and images for this episode can be found on CISO Series https://cisoseries.com/something-stinks-in-here-i-think-it's-your-code/ The problem isn't our users, it's you and your past due code. Something happened. It's either been tainted or expired, but whatever it is, it smells and you need to clean it up. This episode is hosted by me, David Spark (@dspark), producer of CISO Series and Mike Johnson. Our sponsored guest this week is Brian Fox (@brian_fox), co-founder and CTO, Sonatype. Thanks to our podcast sponsor, Sonatype With sec...2021-05-2535 min Defense in DepthSecurity Hygiene for Software DevelopmentAll links and images for this episode can be found on CISO Series https://cisoseries.com/defense-in-depth-security-hygiene-for-software-development/ How do we improve the quality of our software? In the rush to be competitive, security has often taken a back seat to be first to market. What's the formula for fast and secure applications? Check out this post for the basis for our conversation on this week’s episode which features me, David Spark (@dspark), producer of CISO Series, co-host, Geoff Belknap (@geoffbelknap), CISO LinkedIn, and sponsored guest Wayne Jackson, CEO, Sonatype. Thanks to...2021-05-2025 min
Defense in DepthSecurity Hygiene for Software DevelopmentAll links and images for this episode can be found on CISO Series https://cisoseries.com/defense-in-depth-security-hygiene-for-software-development/ How do we improve the quality of our software? In the rush to be competitive, security has often taken a back seat to be first to market. What's the formula for fast and secure applications? Check out this post for the basis for our conversation on this week’s episode which features me, David Spark (@dspark), producer of CISO Series, co-host, Geoff Belknap (@geoffbelknap), CISO LinkedIn, and sponsored guest Wayne Jackson, CEO, Sonatype. Thanks to...2021-05-2025 min CISO Series PodcastPushing This to the Top Of Your Inbox So You Can Delete It AgainAll links and images for this episode can be found on CISO Series https://cisoseries.com/pushing-this-to-the-top-of-your-inbox-so-you-can-delete-it-again/ We're following up on our previous email because we love to engage in self-defeat. We assume you don't want to hear from me again, but just to make sure, I've delivered another email for you to delete. This episode is hosted by me, David Spark (@dspark), producer of CISO Series and Mike Johnson. Our guest this week is Rinki Sethi (@rinkisethi), CISO, Twitter. Thanks to our podcast sponsor, Sonatype ...2021-04-2734 min
CISO Series PodcastPushing This to the Top Of Your Inbox So You Can Delete It AgainAll links and images for this episode can be found on CISO Series https://cisoseries.com/pushing-this-to-the-top-of-your-inbox-so-you-can-delete-it-again/ We're following up on our previous email because we love to engage in self-defeat. We assume you don't want to hear from me again, but just to make sure, I've delivered another email for you to delete. This episode is hosted by me, David Spark (@dspark), producer of CISO Series and Mike Johnson. Our guest this week is Rinki Sethi (@rinkisethi), CISO, Twitter. Thanks to our podcast sponsor, Sonatype ...2021-04-2734 min Colin Wynd's Thoughts & Discourses on Digital TransformationDigital Transformation with Derek Weeks from SonatypeDerek Weeks from Sonatype talks about how the software industry is going through a transformation. Derek co-founded AllDayDevops, one of the largest online conferences in the world, discusses the future of conferences and the State of Software Supply Chain.2021-02-1242 min
Colin Wynd's Thoughts & Discourses on Digital TransformationDigital Transformation with Derek Weeks from SonatypeDerek Weeks from Sonatype talks about how the software industry is going through a transformation. Derek co-founded AllDayDevops, one of the largest online conferences in the world, discusses the future of conferences and the State of Software Supply Chain.2021-02-1242 min The Backend Engineering Show with Hussein NasserInstalling This Twilio Malware NPM Package Opens a Backdoor on Your Developer MachineSonaType detected a Malware in NPM registry imitating to be Twilio package that opens a reverse connection to a remote server and allows attacker to access your local machine content. Let us discuss
Since this command is unix specific it won’t work on Windows
https://blog.sonatype.com/twilio-npm-is-brandjacking-malware-in-disguise
Resources
SSH Tunneling https://youtu.be/N8f5zv9UUMI
Ngrok https://www.youtube.com/watch?v=pR2qNnVIuKE
2020-11-0319 min
The Backend Engineering Show with Hussein NasserInstalling This Twilio Malware NPM Package Opens a Backdoor on Your Developer MachineSonaType detected a Malware in NPM registry imitating to be Twilio package that opens a reverse connection to a remote server and allows attacker to access your local machine content. Let us discuss
Since this command is unix specific it won’t work on Windows
https://blog.sonatype.com/twilio-npm-is-brandjacking-malware-in-disguise
Resources
SSH Tunneling https://youtu.be/N8f5zv9UUMI
Ngrok https://www.youtube.com/watch?v=pR2qNnVIuKE
2020-11-0319 min IT VisionariesWhy Your Code is My Code with Sonatype’s Vice President Derek Week’sDerek Weeks has spent his entire career teaching, educating, and fostering relationships. From his first job with Atari teaching people how to use its consoles, to his role today as a Vice President and DevOps advocate at Sonatype, Derek works to educate others. Derek joined IT Visionaries for a conversation centered on the growth of the DevOps industry and how he is helping to grow that community through All Day DevOps, an online 24-hour conference featuring more than 100 speakers. Key Takeaways A Growing Industry: Five years ago if 1,000 people attended a developer’s conference it...2020-09-0348 min
IT VisionariesWhy Your Code is My Code with Sonatype’s Vice President Derek Week’sDerek Weeks has spent his entire career teaching, educating, and fostering relationships. From his first job with Atari teaching people how to use its consoles, to his role today as a Vice President and DevOps advocate at Sonatype, Derek works to educate others. Derek joined IT Visionaries for a conversation centered on the growth of the DevOps industry and how he is helping to grow that community through All Day DevOps, an online 24-hour conference featuring more than 100 speakers. Key Takeaways A Growing Industry: Five years ago if 1,000 people attended a developer’s conference it...2020-09-0348 min Le Comptoir Sécu[SECHebdo] 30 juin 2020 - Leçons NotPetya, iOS & presse papier, Micode, Ransomware Snatch, Vulnerbilitiés & dépendances, CornerVuln, Aurora IR, etc.2020-06-3000 min
Le Comptoir Sécu[SECHebdo] 30 juin 2020 - Leçons NotPetya, iOS & presse papier, Micode, Ransomware Snatch, Vulnerbilitiés & dépendances, CornerVuln, Aurora IR, etc.2020-06-3000 min Agile Amped Podcast - Inspiring ConversationsOpen Source Code Security and Your EnterpriseThe average enterprise is relying upon about 3,500 open source projects to support faster software development. Unfortunately, external suppliers of the code are often chosen based on popularity or familiarity rather than code quality. Vice President at Sonatype and the co-founder of All Day DevOpsDerek Weeks sat down with us to discuss open source as well as the main findings in the 2019 State of the Software Supply Chain Report. The report details the following: Where open source components are used in software development and how many of them What percentage of components have known security vulnerabilities The policies and regulations on...2019-11-2831 min
Agile Amped Podcast - Inspiring ConversationsOpen Source Code Security and Your EnterpriseThe average enterprise is relying upon about 3,500 open source projects to support faster software development. Unfortunately, external suppliers of the code are often chosen based on popularity or familiarity rather than code quality. Vice President at Sonatype and the co-founder of All Day DevOpsDerek Weeks sat down with us to discuss open source as well as the main findings in the 2019 State of the Software Supply Chain Report. The report details the following: Where open source components are used in software development and how many of them What percentage of components have known security vulnerabilities The policies and regulations on...2019-11-2831 min DevOps ChatNexus Firewall Supports Artifactory RepoThere are really only two repositories of any scale for software components today. The Nexus repo managed by Sonatype and the Artifactory artifact repo managed by JFrog. Up until now they were separate and apart, working with one was independent of another.
In a big move towards keeping DevOps open, the Sonatype people have released a plugin that will allow their Nexus Firewall to work with Artifactory as well as Nexus.
This means that users of both repos can now use the Nexus firewall to make sure that components or artifacts they download are in compliance with the policies they...2019-02-2828 min
DevOps ChatNexus Firewall Supports Artifactory RepoThere are really only two repositories of any scale for software components today. The Nexus repo managed by Sonatype and the Artifactory artifact repo managed by JFrog. Up until now they were separate and apart, working with one was independent of another.
In a big move towards keeping DevOps open, the Sonatype people have released a plugin that will allow their Nexus Firewall to work with Artifactory as well as Nexus.
This means that users of both repos can now use the Nexus firewall to make sure that components or artifacts they download are in compliance with the policies they...2019-02-2828 min The OWASP Podcast Seriesevent-stream: Analysis of a Compromised npm PackageOnce again, the pattern of taking over a known package and modifying it with malicious intent has happened. In this case, it's with the event-stream module in the npm repository. In this broadcast I speaker with Thomas Hunter, Software Developer at Intrinsic and author of "Compromised npm Package: event-stream", and Brian Fox, CTO of Sonatype, author of the Forbes "Open Source Developers And Infrastructure Are The New Front Line Of Security?" article.
Compromised npm Package: event-stream
https://medium.com/intrinsic/compromi...
Open Source Developers And Infrastructure Are The New Front Line Of Security
https://www.forbes.com/sites/forbestechcouncil/2018/05/11/open-source-developers-and-infrastructure-are-the-new-front-line-of-security/#2...2018-11-2721 min
The OWASP Podcast Seriesevent-stream: Analysis of a Compromised npm PackageOnce again, the pattern of taking over a known package and modifying it with malicious intent has happened. In this case, it's with the event-stream module in the npm repository. In this broadcast I speaker with Thomas Hunter, Software Developer at Intrinsic and author of "Compromised npm Package: event-stream", and Brian Fox, CTO of Sonatype, author of the Forbes "Open Source Developers And Infrastructure Are The New Front Line Of Security?" article.
Compromised npm Package: event-stream
https://medium.com/intrinsic/compromi...
Open Source Developers And Infrastructure Are The New Front Line Of Security
https://www.forbes.com/sites/forbestechcouncil/2018/05/11/open-source-developers-and-infrastructure-are-the-new-front-line-of-security/#2...2018-11-2721 min The OWASP Podcast SeriesThe Journey to Open Source at Capital One w/ Tapabrata "Topo" PalWhy would you allow open source usage in your company. What are the compelling reasons to take the risk. In this discussion, I talk with Topo Pal and Derek Weeks about the industry perception of open source and what's really happening behind the curtain at large enterprises. Topo had just finished his keynote presentation at DevOps Enterprise Summit 2018 and I wanted to dive a little deeper into some of the things he talked about.
About Topo Pal
Dr. Topo Pal is Senior Director & Sr. Engineering Fellow
Capital One. His main areas of expertise are in DevOps/DevOpsSec/ Rugged DevOps and...2018-10-2919 min
The OWASP Podcast SeriesThe Journey to Open Source at Capital One w/ Tapabrata "Topo" PalWhy would you allow open source usage in your company. What are the compelling reasons to take the risk. In this discussion, I talk with Topo Pal and Derek Weeks about the industry perception of open source and what's really happening behind the curtain at large enterprises. Topo had just finished his keynote presentation at DevOps Enterprise Summit 2018 and I wanted to dive a little deeper into some of the things he talked about.
About Topo Pal
Dr. Topo Pal is Senior Director & Sr. Engineering Fellow
Capital One. His main areas of expertise are in DevOps/DevOpsSec/ Rugged DevOps and...2018-10-2919 min Business Security Weekly (Video)Imperva, Allstate, & Sonatype - Business Security Weekly #98Imperva acquires app security firm Prevoty in $140 million deal, Allstate accelerates expansion into Identity Protection with acquisition of InfoArmor, Sonatype receives $80 million investment from TPG, Very Good Security makes data unhackable with $8.5 million from Andreessen, Lacework raises $24 million for AI-based cloud security platform, Synapsefi raises over $17 million in Series A funding, and more! Full Show Notes: https://wiki.securityweekly.com/BSWEpisode982018-09-1238 min
Business Security Weekly (Video)Imperva, Allstate, & Sonatype - Business Security Weekly #98Imperva acquires app security firm Prevoty in $140 million deal, Allstate accelerates expansion into Identity Protection with acquisition of InfoArmor, Sonatype receives $80 million investment from TPG, Very Good Security makes data unhackable with $8.5 million from Andreessen, Lacework raises $24 million for AI-based cloud security platform, Synapsefi raises over $17 million in Series A funding, and more! Full Show Notes: https://wiki.securityweekly.com/BSWEpisode982018-09-1238 min 21st Century Work LifeA Question of Trust- a Virtual Team Talk specialWhat contributes to team members trusting each other in virtual teams? In today's episode, we present a range of thoughts, questions and suggestions to help maintain trust in virtual teams. visit www.virtualnotdistant.com “If we don’t have the trust, eventually you don’t have a team, you have a bunch of individuals that are sort of working together, but not really working together towards the same purpose.” (Mark Kilby) History of Virtual Team Talk and this project 06:50mins "What level of trust does my team need, right now, to be effective?" Calculat...2017-04-1355 min
21st Century Work LifeA Question of Trust- a Virtual Team Talk specialWhat contributes to team members trusting each other in virtual teams? In today's episode, we present a range of thoughts, questions and suggestions to help maintain trust in virtual teams. visit www.virtualnotdistant.com “If we don’t have the trust, eventually you don’t have a team, you have a bunch of individuals that are sort of working together, but not really working together towards the same purpose.” (Mark Kilby) History of Virtual Team Talk and this project 06:50mins "What level of trust does my team need, right now, to be effective?" Calculat...2017-04-1355 min Code Monkey TalksEpisode 6: Governing Open Source Usage with Brian FoxBrian Fox (http://www.codemonkey.fm/guests/brian-fox), CTO at Sonatype (https://www.sonatype.com) joins us to discuss how to secure and govern open source usage in your company
In the News:
Evernote migrates to Google Cloud (https://blog.evernote.com/tech/2017/02/08/part-1-evernote-service-options-migrate-google-cloud-platform-gcp/)
Java 9's Jigsaw Auto Modules (http://www.sonatype.org/nexus/2017/01/23/advice-for-jigsaw-regarding-auto-modules/) are a step down with designing dependency management properly
ThoughtWorks shuts down SnapCI (https://blog.snap-ci.com/blog/2017/02/06/2017-02-06-snap-announcement/)
Links
The Expanse (TV (http://www.syfy.com/theexpanse/about), book series (https://www.amazon.com/gp/bookseries/B00K7B2CRQ/ref...2017-02-1000 min
Code Monkey TalksEpisode 6: Governing Open Source Usage with Brian FoxBrian Fox (http://www.codemonkey.fm/guests/brian-fox), CTO at Sonatype (https://www.sonatype.com) joins us to discuss how to secure and govern open source usage in your company
In the News:
Evernote migrates to Google Cloud (https://blog.evernote.com/tech/2017/02/08/part-1-evernote-service-options-migrate-google-cloud-platform-gcp/)
Java 9's Jigsaw Auto Modules (http://www.sonatype.org/nexus/2017/01/23/advice-for-jigsaw-regarding-auto-modules/) are a step down with designing dependency management properly
ThoughtWorks shuts down SnapCI (https://blog.snap-ci.com/blog/2017/02/06/2017-02-06-snap-announcement/)
Links
The Expanse (TV (http://www.syfy.com/theexpanse/about), book series (https://www.amazon.com/gp/bookseries/B00K7B2CRQ/ref...2017-02-1000 min The OWASP Podcast Series2016 State of the Software Supply Chain Report with Derek WeeksThe "State of the Software Supply Chain Report" featured in today's show is an industry report produced by Sonatype. In the spirit of full disclosure, Mark Miller is the Senior Storyteller and DevOps Advocate for Sonatype. That said, no products are mentioned, nothing is being sold. Sonatype is the steward of the Central Repository and has access to an incredible set of data. The information in the report relates directly to A9 within the OWASP Top 10: Using components with known vulnerabilities. The full report is available as a free download.
To describe the findings of the report and the discoveries...2016-07-1116 min
The OWASP Podcast Series2016 State of the Software Supply Chain Report with Derek WeeksThe "State of the Software Supply Chain Report" featured in today's show is an industry report produced by Sonatype. In the spirit of full disclosure, Mark Miller is the Senior Storyteller and DevOps Advocate for Sonatype. That said, no products are mentioned, nothing is being sold. Sonatype is the steward of the Central Repository and has access to an incredible set of data. The information in the report relates directly to A9 within the OWASP Top 10: Using components with known vulnerabilities. The full report is available as a free download.
To describe the findings of the report and the discoveries...2016-07-1116 min The OWASP Podcast SeriesJim Manico's 100th Episode, featuring Mark Miller, Executive Producer of OWASP 24/7In this episode, Jim Manico turns the tables on me for for his 100th podcast. He digs into my past, asks about my motivations for participating in OWASP, inquires on what I hope to accomplish through the series and how DevOps and security can be part of a single conversation when it comes to the software supply chain.
Mark Miller is the Senior Storyteller and Developer Evangelist for Sonatype. He is the curator of TheNexus Community Project, while participating in DevOps and security conferences as a frequent panel host. He recently helped build the DevOps track for RSAC Conference 2016, InfoSec...2016-06-2938 min
The OWASP Podcast SeriesJim Manico's 100th Episode, featuring Mark Miller, Executive Producer of OWASP 24/7In this episode, Jim Manico turns the tables on me for for his 100th podcast. He digs into my past, asks about my motivations for participating in OWASP, inquires on what I hope to accomplish through the series and how DevOps and security can be part of a single conversation when it comes to the software supply chain.
Mark Miller is the Senior Storyteller and Developer Evangelist for Sonatype. He is the curator of TheNexus Community Project, while participating in DevOps and security conferences as a frequent panel host. He recently helped build the DevOps track for RSAC Conference 2016, InfoSec...2016-06-2938 min Welcome to Cybersecurity Insights and PerspectivesInterview with Josh Corman of SonatypeHost Kevin Greene and guest Joshua Corman, chief technology officer at Sonatype, discuss the importance of secure and trusted software in car cybersafety. Corman talks about the possibilities of self-healing software for securing the Internet of Things. He also discusses the significance of an “underwriters lab” for software to help ensure software integrity and provide visibility in the software supply chain.2016-05-2700 min
Welcome to Cybersecurity Insights and PerspectivesInterview with Josh Corman of SonatypeHost Kevin Greene and guest Joshua Corman, chief technology officer at Sonatype, discuss the importance of secure and trusted software in car cybersafety. Corman talks about the possibilities of self-healing software for securing the Internet of Things. He also discusses the significance of an “underwriters lab” for software to help ensure software integrity and provide visibility in the software supply chain.2016-05-2700 min![DEF CON 22 [Materials] Speeches from the Hacker Convention.](https://www.defcon.org/images/defcon-22/dc-22-itunes-logo-materials.jpg) DEF CON 22 [Materials] Speeches from the Hacker Convention.Joshua Corman and Nicholas J Percoco - The Cavalry Year[0] & a Path Forward for Public SafetySlides Here: https://defcon.org/images/defcon-22/dc-22-presentations/Corman-Percoco/DEFCON-22-Josh-Corman-Nicholas-Percoco-Cavalry-Year-0-UPDATED.pdf
The Cavalry Year[0] & a Path Forward for Public Safety
Joshua Corman CTO, SONATYPE
Nicholas J Percoco VP STRATEGIC SERVICES, RAPID7
At DEF CON 21, The Cavalry was born. In the face of clear & present threats to "Body, Mind & Soul" it was clear: The Cavalry Isn't Coming... it falls to us... the willing & able... and we have to try to have impact. Over the past year, the initiative reduced its focus and increased its momentum. With a focus on public safety & human...2014-12-1357 min
DEF CON 22 [Materials] Speeches from the Hacker Convention.Joshua Corman and Nicholas J Percoco - The Cavalry Year[0] & a Path Forward for Public SafetySlides Here: https://defcon.org/images/defcon-22/dc-22-presentations/Corman-Percoco/DEFCON-22-Josh-Corman-Nicholas-Percoco-Cavalry-Year-0-UPDATED.pdf
The Cavalry Year[0] & a Path Forward for Public Safety
Joshua Corman CTO, SONATYPE
Nicholas J Percoco VP STRATEGIC SERVICES, RAPID7
At DEF CON 21, The Cavalry was born. In the face of clear & present threats to "Body, Mind & Soul" it was clear: The Cavalry Isn't Coming... it falls to us... the willing & able... and we have to try to have impact. Over the past year, the initiative reduced its focus and increased its momentum. With a focus on public safety & human...2014-12-1357 min 30 in 30Debbie Rosen - The Missing Connection Between Sales and MarketingDiscussion Highlights
0:00 Barriers to aligning the marketing team with the sales team
2:42 Using social media to reach individuals, not market segments
4:15 The architecture of unfolding your message
6:25 The core to developing a consistent, brand message
A while back, I worked with Debbie Rosen and Jennifer Troxell at Global360 to help design and implement a marketing campaign to give international visibility to their BPM solution in the SharePoint space. In a year and a half, we were able garner two Partner of the Year Awards at the Microsoft WPC in 2011 and place the company in a position to be purchased by...2013-02-0109 min
30 in 30Debbie Rosen - The Missing Connection Between Sales and MarketingDiscussion Highlights
0:00 Barriers to aligning the marketing team with the sales team
2:42 Using social media to reach individuals, not market segments
4:15 The architecture of unfolding your message
6:25 The core to developing a consistent, brand message
A while back, I worked with Debbie Rosen and Jennifer Troxell at Global360 to help design and implement a marketing campaign to give international visibility to their BPM solution in the SharePoint space. In a year and a half, we were able garner two Partner of the Year Awards at the Microsoft WPC in 2011 and place the company in a position to be purchased by...2013-02-0109 min Chaos Computer Club - archive feed (high quality)Supported Self-Administration (linuxtag12)Softwareentwickler/innen sind eine besondere Spezies. Sie probieren gern Neues aus. Oft entscheidet sich ein Projekt relativ spontan für oder gegen den Einsatz bestimmter Tools. Die Entscheidung basiert nicht selten eher auf einem simplen, kurzen Antesten verschiedener Alternativen statt auf einem dokumentierten Variantenvergleich anhand vorher definierter Kriterien. Vielen Projekten fehlt die Zeit, sich erst ein vollständiges Konzept für die Entwicklungsinfrastruktur zu überlegen und umzusetzen, und dann mit der eigentlich Entwicklungsarbeit zu beginnen. Meist stehen hier nur eine zügige Bereitstellung eines Version-Control-Systems und die Konfiguration der Entwicklungsumgebungen im Vordergrund. Weitere Tools fügen die Mitglieder häufig erst be...2012-05-2429 min
Chaos Computer Club - archive feed (high quality)Supported Self-Administration (linuxtag12)Softwareentwickler/innen sind eine besondere Spezies. Sie probieren gern Neues aus. Oft entscheidet sich ein Projekt relativ spontan für oder gegen den Einsatz bestimmter Tools. Die Entscheidung basiert nicht selten eher auf einem simplen, kurzen Antesten verschiedener Alternativen statt auf einem dokumentierten Variantenvergleich anhand vorher definierter Kriterien. Vielen Projekten fehlt die Zeit, sich erst ein vollständiges Konzept für die Entwicklungsinfrastruktur zu überlegen und umzusetzen, und dann mit der eigentlich Entwicklungsarbeit zu beginnen. Meist stehen hier nur eine zügige Bereitstellung eines Version-Control-Systems und die Konfiguration der Entwicklungsumgebungen im Vordergrund. Weitere Tools fügen die Mitglieder häufig erst be...2012-05-2429 min Les Cast Codeurs PodcastLes Cast Codeurs Podcast - Episode 35 - Leerooooooooy JenkiiiiiiiinnnnsEnregistré le 8 février 2011
Hudson vs Jenkins
http://java.net/projects/hudson/
http://jenkins-ci.org/
Bamboo - http://www.atlassian.com/software/bamboo/
CloudBees - http://www.cloudbees.com/
InfraDNA - http://infradna.com/
DEV@Cloud - http://www.cloudbees.com/dev.cb
RUN@Cloud - http://www.cloudbees.com/run.cb
Kenai - http://kenai.com/
Software Freedom Conservancy - http://sfconservancy.org/
Sonatype - http://www.sonatype.com/
http://www.sonatype.com/people/2011/02/hudsons-bright-future/
http://jenkins-ci.org/content/hudsons-future
http://kohsuke.org/bye-bye-hudson-hello-jenkins/
http://nighthacks.org/roller/jag/entry/hudson_is_dead_long_live
http://jenkins-ci.org/content/jenkins
ht...2011-02-131h 02
Les Cast Codeurs PodcastLes Cast Codeurs Podcast - Episode 35 - Leerooooooooy JenkiiiiiiiinnnnsEnregistré le 8 février 2011
Hudson vs Jenkins
http://java.net/projects/hudson/
http://jenkins-ci.org/
Bamboo - http://www.atlassian.com/software/bamboo/
CloudBees - http://www.cloudbees.com/
InfraDNA - http://infradna.com/
DEV@Cloud - http://www.cloudbees.com/dev.cb
RUN@Cloud - http://www.cloudbees.com/run.cb
Kenai - http://kenai.com/
Software Freedom Conservancy - http://sfconservancy.org/
Sonatype - http://www.sonatype.com/
http://www.sonatype.com/people/2011/02/hudsons-bright-future/
http://jenkins-ci.org/content/hudsons-future
http://kohsuke.org/bye-bye-hudson-hello-jenkins/
http://nighthacks.org/roller/jag/entry/hudson_is_dead_long_live
http://jenkins-ci.org/content/jenkins
ht...2011-02-131h 02 Les Cast Codeurs PodcastLes Cast Codeurs Podcast - Episode 35 - Leerooooooooy JenkiiiiiiiinnnnsEnregistré le 8 février 2011
Hudson vs Jenkins
http://java.net/projects/hudson/
http://jenkins-ci.org/
Bamboo - http://www.atlassian.com/software/bamboo/
CloudBees - http://www.cloudbees.com/
InfraDNA - http://infradna.com/
DEV@Cloud - http://www.cloudbees.com/dev.cb
RUN@Cloud - http://www.cloudbees.com/run.cb
Kenai - http://kenai.com/
Software Freedom Conservancy - http://sfconservancy.org/
Sonatype - http://www.sonatype.com/
http://www.sonatype.com/people/2011/02/hudsons-bright-future/
http://jenkins-ci.org/content/hudsons-future
http://kohsuke.org/bye-bye-hudson-hello-jenkins/
http://nighthacks.org/roller/jag/entry/hudson_is_dead_long_live
http://jenkins-ci.org/content/jenkins
ht...2011-02-131h 02
Les Cast Codeurs PodcastLes Cast Codeurs Podcast - Episode 35 - Leerooooooooy JenkiiiiiiiinnnnsEnregistré le 8 février 2011
Hudson vs Jenkins
http://java.net/projects/hudson/
http://jenkins-ci.org/
Bamboo - http://www.atlassian.com/software/bamboo/
CloudBees - http://www.cloudbees.com/
InfraDNA - http://infradna.com/
DEV@Cloud - http://www.cloudbees.com/dev.cb
RUN@Cloud - http://www.cloudbees.com/run.cb
Kenai - http://kenai.com/
Software Freedom Conservancy - http://sfconservancy.org/
Sonatype - http://www.sonatype.com/
http://www.sonatype.com/people/2011/02/hudsons-bright-future/
http://jenkins-ci.org/content/hudsons-future
http://kohsuke.org/bye-bye-hudson-hello-jenkins/
http://nighthacks.org/roller/jag/entry/hudson_is_dead_long_live
http://jenkins-ci.org/content/jenkins
ht...2011-02-131h 02 The Java PosseJava Posse #301 - Newscast for April 2nd 2010
Newscast for April 2nd 2010
Fully formatted shownotes can always be found at http://javaposse.com
Last chance - Javazone call for papers extended 1 week. http://jz10.java.no/program.html
Apple, Android, HTC, marketplaces and ex-CEOs.
http://www.apple.com/pr/library/2010/03/02patents.html
http://techcrunch.com/2010/03/02/apple-goes-after-htc-in-lawsuit-over-20-iphone-patents/
http://techcrunch.com/2010/03/02/the-complaint-apples-patent-lawsuit-against-htc-is-all-about-android/
http://www.reuters.com/article/idUSTRE62H0EA20100318
http://java.dzone.com/dose/dzone-daily-dose-34
http://threatpost.com/en_us/blogs/htc-phones-pre-installed-mariposa-bot-client-030910
http://www.petitiononline.com/androidm/
http://www.ilounge.com/index.php/news/comments/eff-posts-apples-iphone-developer-agreement-online/
http://jonathanischwartz.wordpress.com/2010/03/09/good-artists-copy-great-artists-steal/
Tim Bray, co-editor of the XML specifications a...2010-04-021h 39
The Java PosseJava Posse #301 - Newscast for April 2nd 2010
Newscast for April 2nd 2010
Fully formatted shownotes can always be found at http://javaposse.com
Last chance - Javazone call for papers extended 1 week. http://jz10.java.no/program.html
Apple, Android, HTC, marketplaces and ex-CEOs.
http://www.apple.com/pr/library/2010/03/02patents.html
http://techcrunch.com/2010/03/02/apple-goes-after-htc-in-lawsuit-over-20-iphone-patents/
http://techcrunch.com/2010/03/02/the-complaint-apples-patent-lawsuit-against-htc-is-all-about-android/
http://www.reuters.com/article/idUSTRE62H0EA20100318
http://java.dzone.com/dose/dzone-daily-dose-34
http://threatpost.com/en_us/blogs/htc-phones-pre-installed-mariposa-bot-client-030910
http://www.petitiononline.com/androidm/
http://www.ilounge.com/index.php/news/comments/eff-posts-apples-iphone-developer-agreement-online/
http://jonathanischwartz.wordpress.com/2010/03/09/good-artists-copy-great-artists-steal/
Tim Bray, co-editor of the XML specifications a...2010-04-021h 39